The Modern Battlefield: Why We Need to Revolutionize Threat Detection in 2024
The digital landscape is a battlefield. Every day, businesses face a relentless onslaught of cyberattacks with the potential to cripple operations, steal sensitive data, and erode consumer trust. In this constantly evolving threat environment, relying on outdated security measures is akin to sending knights in shining armor against tanks. We need a revolution in threat detection, and that’s where NetSecurity’s ThreatResponder comes in.
The Evolving Threat Landscape:
Gone are the days of easily identifiable, single-point-of-failure attacks. Cybercriminals are now sophisticated and highly adaptable. They exploit vulnerabilities in complex systems, leverage social engineering tactics, and weaponize readily available tools to launch multi-faceted assaults. The rise of zero-day attacks, previously unknown vulnerabilities, further complicates the situation, leaving traditional signature-based detection struggling to keep up.
The Shortcomings of Traditional Methods:
Many organizations still rely on legacy security solutions. These systems often operate in silos, creating blind spots for attackers to exploit. Additionally, manual threat analysis is time-consuming and prone to human error, leaving businesses vulnerable while analysts race to identify and contain threats.
The Urgent Need for Modernization:
Considering the evolving threat landscape and limitations of traditional methods, the need for modernized threat detection capabilities becomes abundantly clear. This modernization requires a shift towards:
- Cloud-native Platforms: Cloud-based solutions offer scalability, centralized management, and access to the latest security updates, removing the burden of managing and maintaining on-premise infrastructure.
- Automation: Automating threat detection, investigation, and response processes helps organizations address security incidents swiftly and efficiently, minimizing damage and downtime.
- Machine Learning and AI: Leveraging these technologies allows for analyzing large volumes of data in real-time, identifying anomalies, and predicting potential threats before they materialize.
- Unified Threat Management (UTM): Integrating various security functions, such as antivirus, firewall, and intrusion detection, into a single platform provides a comprehensive view of the security posture and simplifies management.
NetSecurity’s ThreatResponder: Your Modernized Defense System:
As the threat landscape continues to evolve, traditional security measures are often insufficient. CISOs need a more comprehensive approach to cybersecurity that goes beyond perimeter defenses. This is where ThreatResponder by NetSecurity comes into play. ThreatResponder is an all-in-one, unified, cloud-native, machine learning-driven cyber-resilient endpoint security platform.
ThreatResponder, designed and developed by NetSecurity, is an all-in-one cloud-native cyber-resilient endpoint platform that embodies these very principles. Packed with cutting-edge technology, ThreatResponder empowers you to consolidate security, harness the power of AI, automate digital forensics and incident response, gain real-time insights, enhance threat hunting, and simplify threat and vulnerability management
ThreatResponder is more than just a product; it’s a paradigm shift in how you approach cyber security. It equips you with the tools and intelligence to proactively anticipate threats, swiftly respond to incidents, and ultimately, fortify your defenses and keep your digital assets safe and protected.
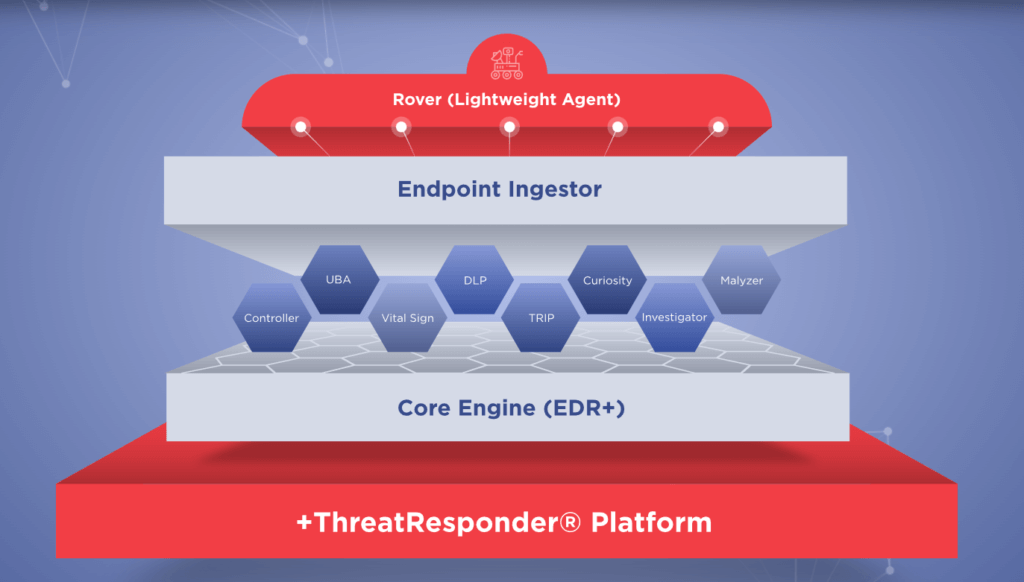
These pillars collectively create a formidable defense system against a wide range of cyber threats. However, in an ever-evolving digital world, there’s always room for improvement and expansion.
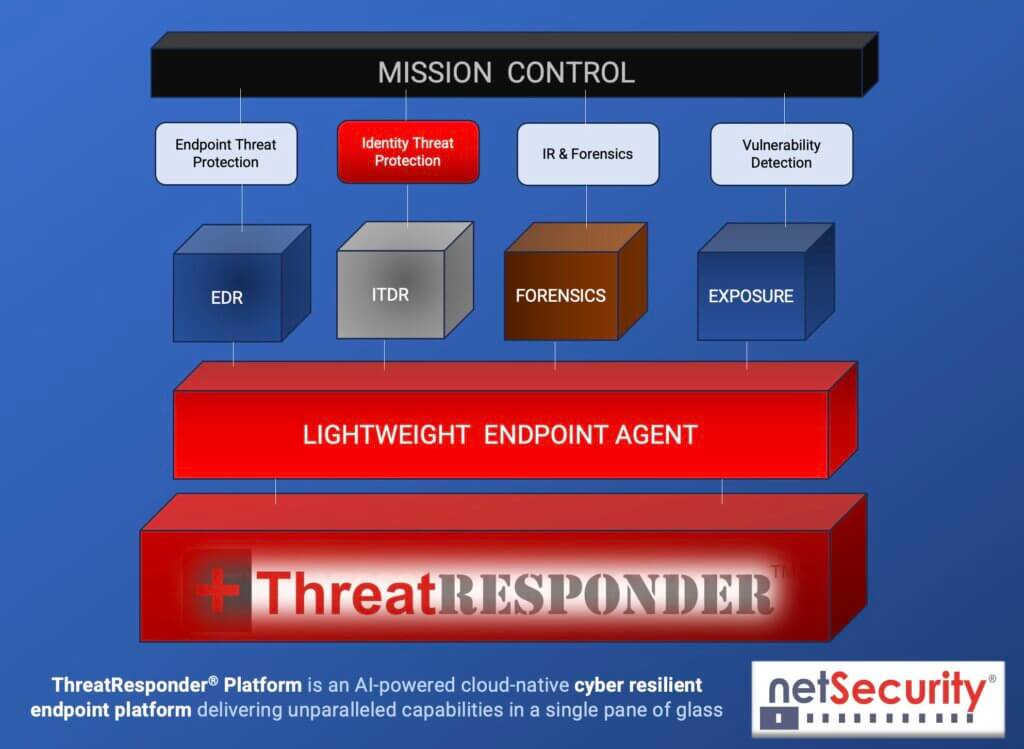
It is designed to provide cybersecurity teams with the necessary tools and insights to defend their organizations effectively. Let’s take a closer look at the core features of ThreatResponder:
- Endpoint Detection and Response (EDR): Endpoint Detection and Response is a critical component of modern cybersecurity. ThreatResponder continuously monitors endpoints (devices and servers) for signs of suspicious activities, such as malware infections or unusual behavior. When a threat is detected, ThreatResponder responds in real-time to mitigate the risk, making it an invaluable asset in threat containment and incident response.
- Identity Threat Detection and Response: User identities are a prime target for attackers. ThreatResponder analyzes user behaviors and privileges to identify suspicious activities and potential threats. By understanding user identity and access patterns, it can detect unauthorized access and protect sensitive data from breaches.
- Forensics: In the aftermath of a security incident, forensics play a crucial role in understanding the attack and its impact. ThreatResponder provides detailed forensic capabilities, helping CISOs and their teams analyze the scope of an incident, track the attacker’s movements, and collect evidence for potential legal action.
- Threat Hunting: Proactive threat hunting is essential for identifying threats before they cause significant damage. ThreatResponder equips CISOs with advanced threat hunting tools, enabling them to search for hidden threats, vulnerabilities, and indicators of compromise within their organization’s network.
- Vulnerability Detection: Identifying and patching vulnerabilities is a fundamental part of cybersecurity. ThreatResponder helps CISOs stay on top of vulnerabilities within their organization’s systems and applications, allowing them to prioritize and address weaknesses before attackers exploit them.
Don’t wait for disaster to strike. Modernize your threat detection capabilities with our ThreatResponder platform today. Contact NetSecurity to learn more and request a free demo.
Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).