Prevent Phobos Ransomware Attacks with ThreatResponder
Phobos ransomware emerged as a significant threat in 2019, plaguing businesses and individuals. This malicious software encrypts valuable files, rendering them inaccessible and demanding a ransom payment for decryption. Understanding Phobos ransomware, its tactics, and how to defend against it is crucial in today’s digital landscape.
What is Phobos Ransomware?
Phobos is structured as a ransomware-as-a-service (RaaS) model. Since May 2019, Phobos ransomware incidents impacting state, local, tribal, and territorial (SLTT) governments have been regularly reported to the MS-ISAC. These incidents successfully targeted municipal and county governments, emergency services, education, public healthcare, and other critical infrastructure entities to ransom several million U.S. dollars.
In recent times, security researchers have identified that Phobos shares a close resemblance to Elking, Eight, Devos, Backmydata, and Faust ransomware due to similar TTPs observed in Phobos intrusions. Phobos primarily targets business servers, exploiting weaknesses in Remote Desktop Protocol (RDP) configurations. Millions of users rely on RDP for remote network access, making it a lucrative attack vector for cybercriminals.
Key Tactics and Techniques of Phobos Ransomware
Phobos employs a multi-pronged approach to infiltrate systems, encrypt files, and extort victims. Let’s delve into its key tactics and techniques and see how ThreatResponder was successful in detecting every move of the Phobos ransomware :
-
Initial Access (TA0001): Phobos leverages techniques like phishing attacks [T1566] and brute-force attacks [T1110] on Remote Desktop Protocol (RDP) [T1595.001] to gain initial access to any organization. Phishing emails often contain malicious attachments disguised as legitimate documents, which will be the initial droppers. Once opened, threat actors use the malware’s functionality to download the Phobos payload and exfiltrate data from the compromised system.
-
Execution (TA0002):
Hackers may transfer the ransomware executable directly to the victim’s system after gaining initial access. Phobos actors run executables like
1saas.exeorcmd.exeto deploy additional Phobos payloads that have elevated privileges enabled [TA0004]
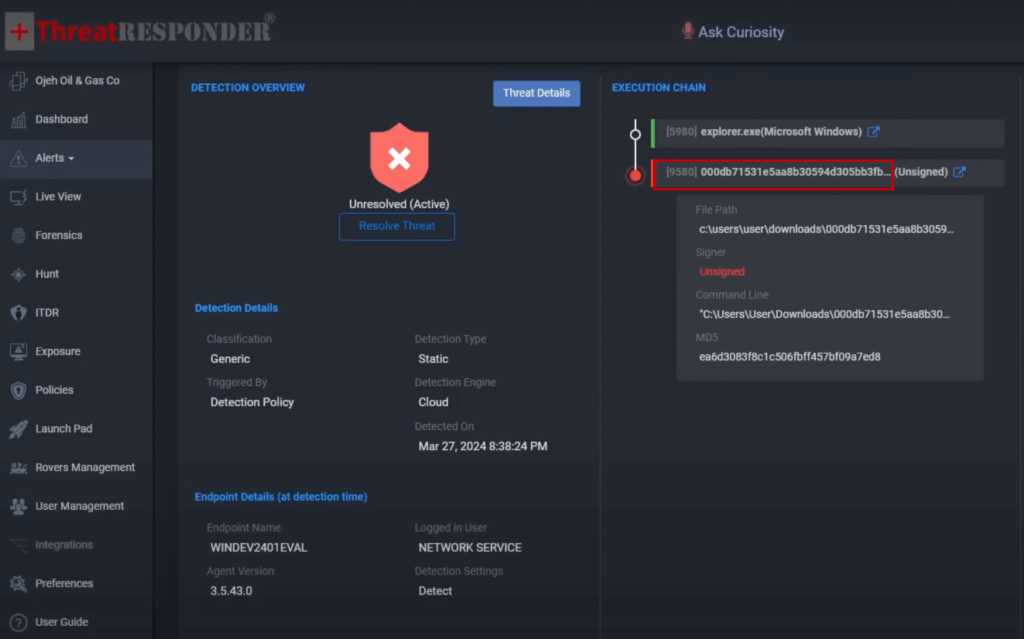
Figure: ThreatResponder Detecting Phobos Ransomware Attack Immediately after Execution
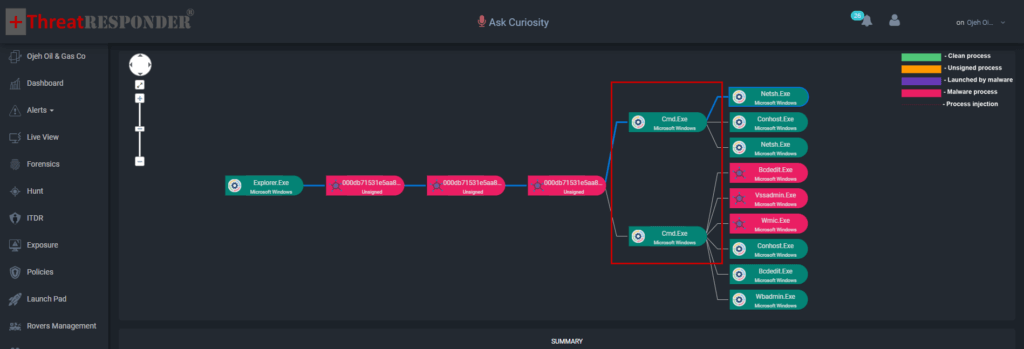
Figure: ThreatResponder Detecting Malicious Command Line Execution by Phobos Ransomware
-
Persistence (TA0003):
Phobos ransomware uses commands such as
Exec.exethebcdedit[.]execontrol mechanism. Phobos has also been observed using Windows Startup folders and Run Registry Keys, such asC:/Users\Admin\AppData\Local\directory[T1490][T1547.001] to maintain persistence within compromised environments.
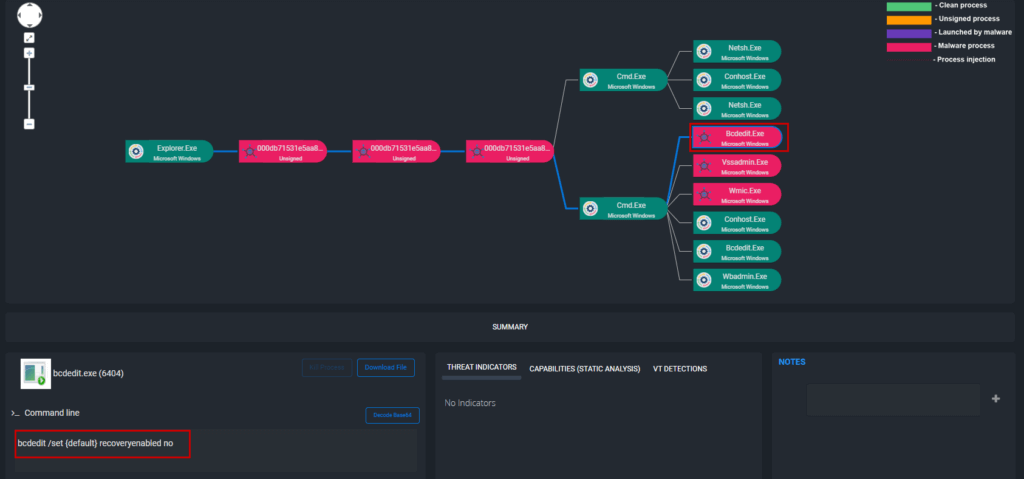
Figure: ThreatResponder Detecting bcdedit.exe execution by Phobos ransomware to disable Recovery Mode
- Defense Evasion (TA0005):
Phobos may attempt to disable or tamper with antivirus software to evade detection and facilitate encryption. The ransomware can utilize the Windows Management Instrumentation (WMIC) command-line utility to hinder file recovery efforts.
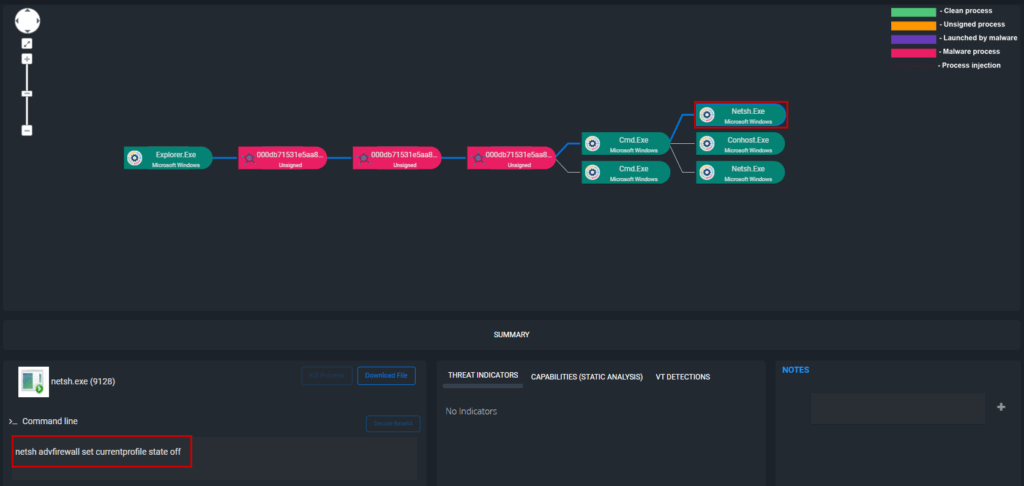
Figure: ThreatResponder Detecting Phobos Disabling Firewall on Infected Endpoint
- Impact (TA0040):
After the exfiltration phase, Phobos actors then hunt for backups. They use vssadmin.exe and Windows Management Instrumentation command-line utility (WMIC) to discover and delete volume shadow copies in Windows environments. This prevents victims from recovering files after encryption has taken place [T1047][T1490]. In addition, after encrypting the victim’s machine, Phobos deploys a ransom note on the victim’s desktop.
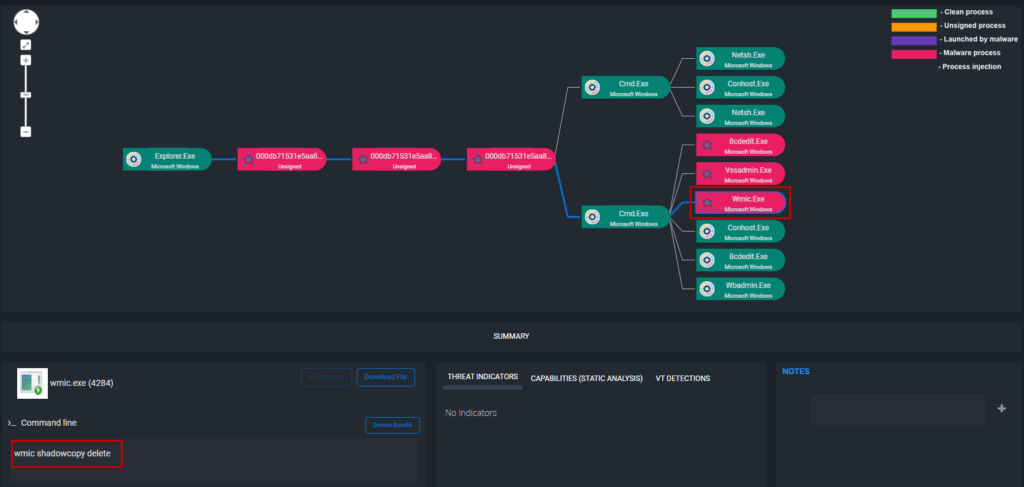
Figure: ThreatResponder Detecting Phobos executing WMIC
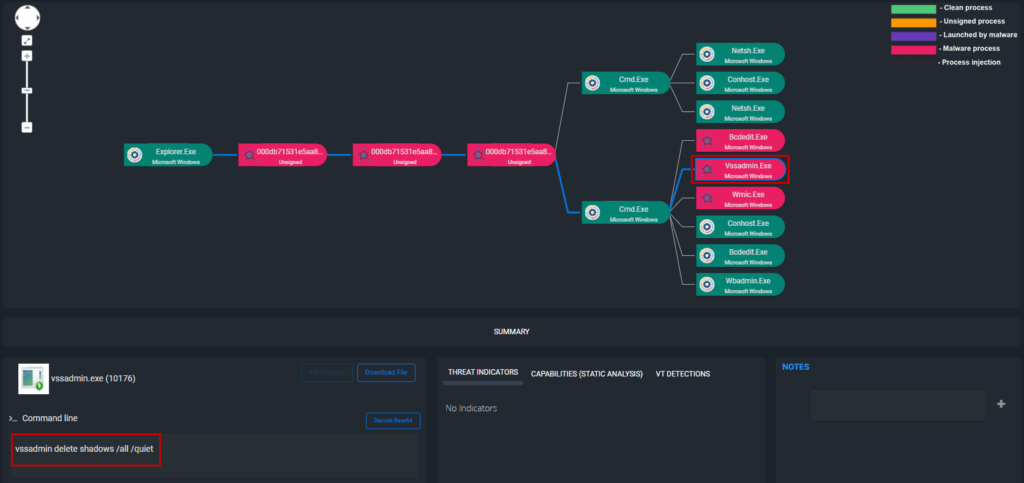
Figure: ThreatResponder Detecting Phobos executing vssadmin to delete shadow copies
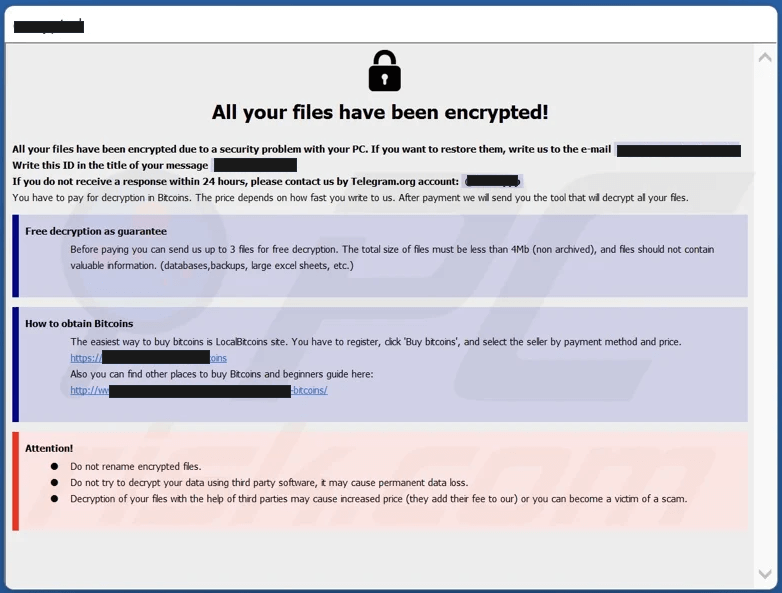
Figure: Phobos Ransomware Ransom Note
Indicators of Compromise:
- ea6d3083f8c1c506fbff457bf09a7ed8
- SHA256: 000db71531e5aa8b30594d305bb3fbce8e2c71f66e2170091ef58b3c1f306f46
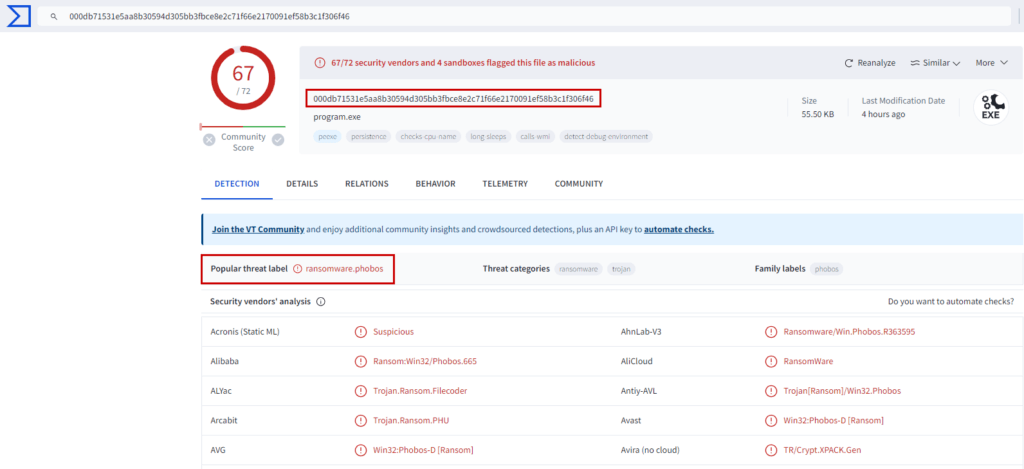
Figure: VirusTotal Score for Detected Phobos Ransomware Threat
See How ThreatResponder Prevents Phobos Ransomware Attacks:
NetSecurity’s ThreatResponder® Platform is a comprehensive, cloud-native endpoint threat detection, prevention, response, analytics, intelligence, investigation, and hunting solution that can help businesses stay ahead of the latest cyber threats.
With ThreatResponder®, organizations gain situational awareness and immediate threat visibility into thousands of endpoints, allowing them to respond to and neutralize cyber attacks across their enterprise. The platform provides 361° threat visibility of enterprise assets, regardless of their location, and is capable of detecting and preventing a wide range of attacks, including exploit, fileless, malware, and ransomware attacks.
The platform is also designed to provide powerful tools for incident response and forensics investigation on remote endpoints, as well as insider threat and data loss prevention capabilities. Furthermore, ThreatResponder® can ingest data from millions of endpoints, providing organizations with valuable insights into users’ activities and network bandwidth utilization. The platform offers a comprehensive threat intelligence module, allowing organizations to consume threat intel from various sources, produce their own threat intelligence, and perform malware analysis using MaLyzer™.
NetSecurity’s ThreatResponder® Platform can help organizations stay ahead of the latest cyber threats. With its comprehensive features, ThreatResponder® provides organizations with the tools they need to detect, prevent, respond to, and investigate cyber attacks, all in one place.
See ThreatResponder In Action
Want to try our ThreatResponder, cutting-edge Endpoint Detection & Response (EDR), and ThreatResponder FORENSICS, the Swiss knife for forensic investigators in action? Click on the below button to request a free demo of our NetSecurity’s ThreatResponder platform.
Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).