Is an agentless stand-alone software (which requires no installation) that allows ANYONE to investigate ANY Windows endpoint ANYWHERE the endpoint may be--whether on-premises, in the cloud, offline, "dead" hard drives, with or without an Internet connection

Challenges of Investigating Windows Endpoint Compromise


- Investigating dead or offline endpoints is time consuming and prone to errors
- Using multiple tools to triage, often omitting crucial evidence not available without raw disk Access
- Inadequate specialized skills in forensics or incident response, resulting in hiring an expert consultant

The Solution ThreatResponder® FORENSICS
ThreatResponder® FORENSICS is a ”chip off” ThreatResponder® PLATFORM.
No software installation is necessary; simply run the executable and start seeing results in minutes!
Allows you to pinpoint when and how an endpoint got compromised or infected and under what user context
Helps you determine if data was exfiltrated and save thousands in (potential) consulting costs
Allows you to examine the system in a forensically-sound manner without the risk of "spoiling" the evidence

Benefits

Quickly identify and mitigate threats and reduce impact of business disruption

Perform remote enterprise investigations on any endpoint anywhere – local, remote, or cloud

Conduct legally defensible investigations

Use by anyone – from novice IT to seasoned forensics professionals

Reduce cost of investigations

ThreatResponder® FORENSICS for SOC Operations
Short-staff in your SOC operations? Integrate ThreatResponder® FORENSICS as part of your SOC and do more with limited resources and with little or no experience in forensics.


- Detect exploit, fileless, and malware attacks
- Monitor process, file system, registry, network, and memory activities
- Leverage threat intelligence, IOCs, signatures, MITRE ATT@CK techniques, behavior, and Machine Learning (ML) algorithms to detect threats quickly
Forensics Investigation
Quickly gain insight into the context of a breach or compromise
Recover deleted, hidden, or lost files from your assets
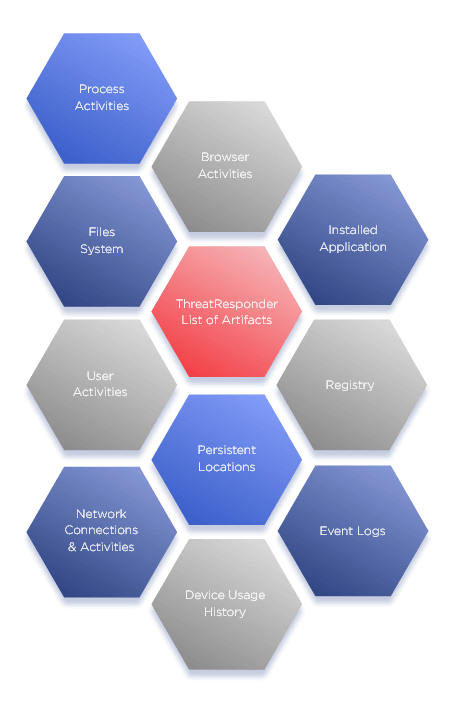
Examine file systems, user activity, Internet history, emails, and registry entries to uncover crucial evidence
Construct timelines of user activity, file access, and system events to understand the sequence of events
Generate report generation that compiles the findings into a clear, concise, and legally defensible format

Incident Remediation
Immediately identify and neutralize threats within minutes of conducting the analysis


Are you suspecting that one of your remote endpoints has been compromised? Have you isolated or shut down a machine that is infected? Whether a Windows machine is offline or online, in the cloud, or in a VM, or you have a drive or VMDK file of a machine that is acting “strange,” you can leverage ThreatResponder® FORENSICS to get answers quickly and implement appropriate remediation actions.

Datasheets and Screenshots
Gain a better understanding of the capabilities of ThreatResponder® FORENSICS

NetSecurity ThreatResponder Capability Brief
NetSecurity ThreatResponder Capability Brief
NetSecurity ThreatResponder Capability Brief

NetSecurity ThreatResponder IR Datasheet
NetSecurity ThreatResponder IR Datasheet
NetSecurity ThreatResponder IR Datasheet

NetSecurity ThreatResponder Use Cases
NetSecurity ThreatResponder Use Cases
NetSecurity ThreatResponder Use Cases

Download a FREE Copy

How do you know that your organization has not already been compromised by a nation-state or insider threat actor?
A chip off ThreatResponder® Platform, ThreatResponder® FORENSICS is a standalone executable for investigating Windows endpoints that are infected or compromised, with speed and accuracy. Whether the endpoint is offline, online, dead (physical or virtual hard drives), and located in on-premises, remote, or the cloud, you can execute legally defensible forensics investigation against any Windows endpoint from the comfort of your home or office. Best of all, there is no experience necessary to use the software.
Download a FREE Copy of ThreatResponder® FORENSICS so you can conduct forensics (breach) investigation and incident response like a pro. Complete the form to the right and quickly identify Who is Hacking your Network™?.





