The Nefarious Five: Top Russian State-Sponsored Cyber Threat Groups
The digital landscape is a battlefield, and in the shadows lurk cyber threats that can cripple infrastructure, steal secrets, and sow discord. Among these threats, state-sponsored actors pose a significant risk, with Russia being a major player. Today, we delve into the top five Russian state-sponsored cyber threat groups, notorious for their sophisticated attacks and far-reaching impact.
1. APT29 (Cozy Bear, The Dukes)
APT29, also known as Cozy Bear and The Dukes, is a highly skilled group believed to be affiliated with the Russian Foreign Intelligence Service (SVR). Active since at least 2014, APT29 has targeted a wide range of victims, including:
- Government Agencies: Foreign ministries, defense departments, and other government institutions have been compromised by APT29 to steal sensitive information related to foreign policy, military capabilities, and negotiations.
- Think Tanks and Research Institutions: Valuable intellectual property and research data related to various fields, including energy, technology, and national security, have been targeted by APT29.
- Critical Infrastructure: Power grids, transportation systems, and other vital infrastructure have been probed by APT29, raising concerns about potential disruption.
APT29’s tactics are diverse, but they often rely on spear phishing emails containing malicious attachments or links. Once initial access is gained, the group establishes persistence within the victim’s network, exfiltrates data, and moves laterally to compromise additional systems. APT29 is known for its patience, carefully planning and executing attacks over extended periods.
2. APT28 (Fancy Bear)
Another prominent group, APT28 (Fancy Bear), is linked to Russia’s military intelligence agency, the Main Directorate of the General Staff (GRU). Unlike APT29, APT28 seems more focused on influencing political events. Here’s a glimpse into their targets:
- Political Campaigns: APT28 has been accused of interfering in elections by hacking into campaign servers, stealing emails, and leaking them to influence public opinion.
- Anti-Doping Agencies: The World Anti-Doping Agency (WADA) was targeted by APT28, resulting in the leak of confidential athlete data, potentially impacting anti-doping efforts.
- Media Organizations: Hackers affiliated with APT28 have compromised media outlets, potentially aiming to manipulate news coverage and spread disinformation.
APT28’s modus operandi involves a mix of social engineering techniques, phishing attacks, and exploiting software vulnerabilities. They are also known for their destructive capabilities, as seen in the NotPetya ransomware attack of 2017, which inflicted major damage on Ukrainian infrastructure.
3. Sandworm Team (TeleBots, TEMP. Noble, VOODOO BEAR)
The Sandworm Team, also known by various aliases, is a unit linked to Russia’s GRU. They are infamous for disruptive cyberattacks targeting critical infrastructure and government institutions. Some of their notable actions include:
- 2015 Ukrainian Power Grid Attack: Sandworm crippled parts of the Ukrainian power grid by launching a sophisticated cyberattack, demonstrating their ability to disrupt essential services.
- 2016 Democratic National Committee (DNC) Hack: The DNC email hack, which released sensitive information during the 2016 US presidential election, is attributed to Sandworm.
- 2017 Olympic Destroyer Attack: The Pyeongchang Winter Olympics were marred by a cyberattack believed to be orchestrated by Sandworm, disrupting operations and causing embarrassment.
The Sandworm Team utilizes a potent arsenal, including custom malware, zero-day exploits, and distributed denial-of-service (DDoS) attacks. Their attacks are often meticulously planned and executed with a high degree of precision, causing significant damage.
4. Turla (Snake, Uroboros)
Turla, also known as Snake or Uroboros, is a cyberespionage group with suspected ties to the Russian government. They are known for their persistence and sophisticated techniques, making them a formidable threat. Here are some of their targets:
- Government Agencies and Embassies: Turla has successfully breached the networks of government agencies and embassies, stealing sensitive diplomatic and intelligence information.
- Defense Contractors and Aerospace Companies: Valuable intellectual property related to military technology and advanced weaponry has been targeted by Turla, potentially bolstering Russian military capabilities.
- Telecom Companies: Compromising telecom companies allows Turla to gain access to vast amounts of communication data, facilitating further espionage efforts.
Turla employs a range of techniques, including spear phishing, watering hole attacks (compromising legitimate websites to infect visitors), and custom-developed malware. They are known for their ability to maintain long-term access to victim networks, enabling continuous data collection.
5. APT30 (Lotus Blossom, Naikon, G0013)
Rounding out our list is APT30, a cyberespionage group believed to be affiliated with the Chinese government. While their exact connection remains murky, APT30 has carved a niche for itself in Southeast Asia. Let’s explore their targets and tactics:
- Governments and Businesses: APT30 primarily targets entities in Southeast Asia, particularly governments and businesses with access to valuable political, economic, and military information.
- Organizations of Strategic Interest: Organizations critical to regional infrastructure, technology development, and national security are also on APT30’s radar.
APT30’s attack methods involve a blend of traditional and innovative techniques which include Spear Phishing, custom backdoors, USB and flash drives, etc. These top five Russian state-sponsored cyber threat groups pose a significant and ever-evolving threat. They constantly refine their tactics, develop new tools, and exploit emerging vulnerabilities. As nation-states increasingly rely on digital infrastructure, the potential impact of cyberattacks becomes more severe.
NetSecurity’s ThreatResponder: Your Trusted Partner to Prevent Advanced Cyber Attacks
As the threat landscape continues to evolve, traditional security measures are often insufficient. Companies need a more comprehensive approach to cybersecurity that goes beyond perimeter defenses. This is where ThreatResponder by NetSecurity comes into play.
ThreatResponder, designed and developed by NetSecurity, is an all-in-one cloud-native cyber-resilient endpoint platform that embodies these very principles. Packed with cutting-edge technology, ThreatResponder empowers you to consolidate security, harness the power of AI, automate digital forensics and incident response, gain real-time insights, enhance threat hunting, and simplify threat and vulnerability management
ThreatResponder is more than just a product; it’s a paradigm shift in how you approach cyber security. It equips you with the tools and intelligence to proactively anticipate threats, swiftly respond to incidents, and ultimately, fortify your defenses and keep your digital assets safe and protected.
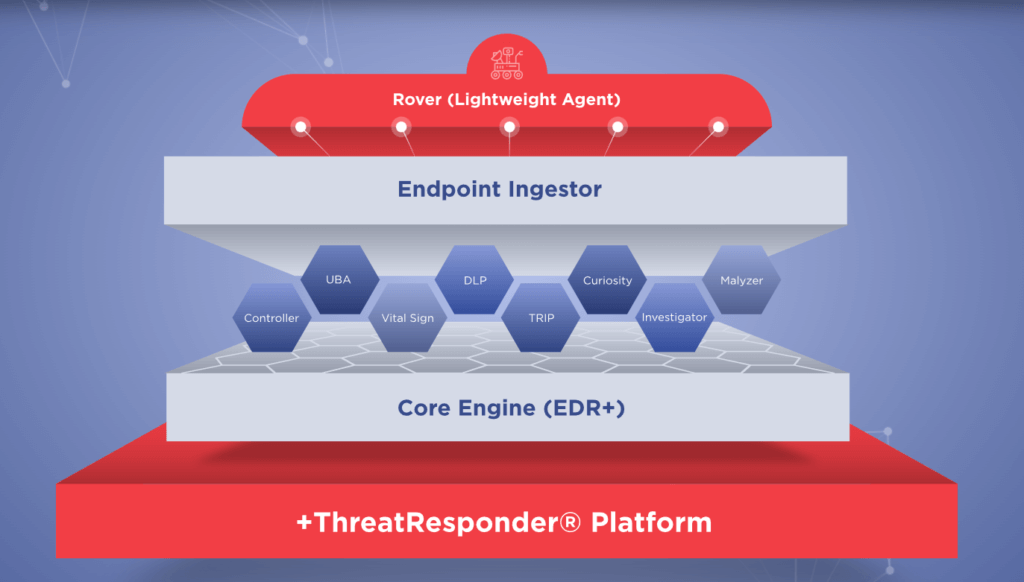
These pillars collectively create a formidable defense system against a wide range of cyber threats. However, in an ever-evolving digital world, there’s always room for improvement and expansion.
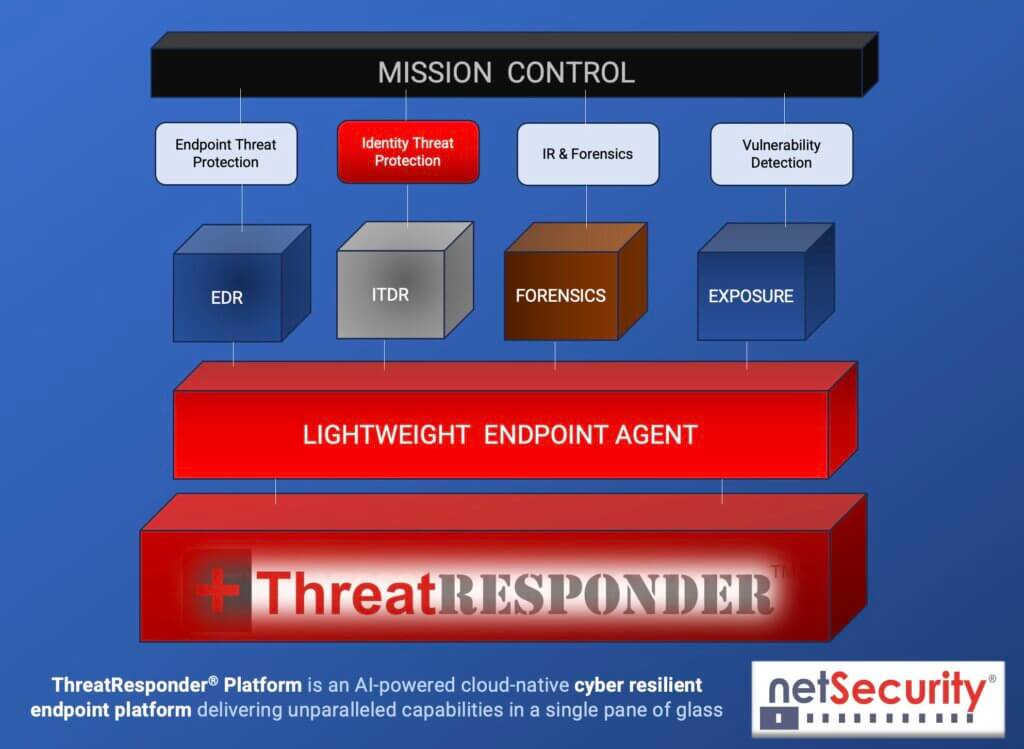
It is designed to provide cybersecurity teams with the necessary tools and insights to defend their organizations effectively. Let’s take a closer look at the core features of ThreatResponder:
- Endpoint Detection and Response (EDR): Endpoint Detection and Response is a critical component of modern cybersecurity. ThreatResponder continuously monitors endpoints (devices and servers) for signs of suspicious activities, such as malware infections or unusual behavior. When a threat is detected, ThreatResponder responds in real-time to mitigate the risk, making it an invaluable asset in threat containment and incident response.
- Identity Threat Detection and Response: User identities are a prime target for attackers. ThreatResponder analyzes user behaviors and privileges to identify suspicious activities and potential threats. By understanding user identity and access patterns, it can detect unauthorized access and protect sensitive data from breaches.
- Forensics: In the aftermath of a security incident, forensics play a crucial role in understanding the attack and its impact. ThreatResponder provides detailed forensic capabilities, helping CISOs and their teams analyze the scope of an incident, track the attacker’s movements, and collect evidence for potential legal action.
- Threat Hunting: Proactive threat hunting is essential for identifying threats before they cause significant damage. ThreatResponder equips CISOs with advanced threat hunting tools, enabling them to search for hidden threats, vulnerabilities, and indicators of compromise within their organization’s network.
- Vulnerability Detection: Identifying and patching vulnerabilities is a fundamental part of cybersecurity. ThreatResponder helps CISOs stay on top of vulnerabilities within their organization’s systems and applications, allowing them to prioritize and address weaknesses before attackers exploit them.
Don’t wait for disaster to strike. Modernize your threat detection capabilities with our ThreatResponder platform today. Contact NetSecurity to learn more and request a free demo.
Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).











