One lightweight agent.
One single pane of glass.
Unlimited capabilities.
Predict, Stop, & Investigate Attacks


The New Yardstick for
Endpoint Security
ThreatResponder’s unparalleled innovation is the new yardstick for endpoint protection. Replace traditional and ineffective anti-virus, firewalls, and security products with one lightweight agent (“Rover”) to gain threat visibility into and control of each enterprise endpoint.
Multi-Platform (Windows, macOS, and Linux)
Remote IR and Forensic Investigations
Offensive Capabilities (for Law Enforcement / Intel Communities)
Threats and Vulnerabilities Remediation
One Platform. Many Capabilities: (I) Endpoint Threat, (II) Identity Threat Detection and Response (ITDR), (III) Vulnerability Detection, and (IV) Forensics. Single Pane of Glass.
Common Vulnerability Exposures (CVEs) Detection in Real-Time and without Scanning – BOD 22-01 and KEVs
Identity Threat Detection and Response (ITDR)
Insider Threats, User Behavior, and Analytics
Predict Attacks Before they Occur
Real time CVE detection
Zero-day vulnerabilities
Remediation tracking
Identities creation and usage
User behavior


Neutralize Threats in
Real Time

Machine Learning (ML) & Behavior-Based Algorithms
- ML-based detection
- MITRE ATT@CK techniques
- Attackers’ TTPs
- Malware-less techniques

Signatures + Known Indicators
- Signature of known malware
- Indicators of Compromise (IoCs)
- Policy Enforcement

Threat Intelligence (Internal/External)
- Feeds from Open Source, Government, and Commercial sources
- File Hashes / Name / Paths
- C&C IP Addresses, URLs, Domain Names, Email Addresses
- User Agents, Mutexes, etc.

Core Engine
- Ingests Threat Data
- Combines ML and Behavior-based Algorithms, Signatures, IoCs, and Threat Intelligence
Forensically Investigate at Scale
Incident response
Host isolation or containment
Process and network termination
Deep forensics investigation
Timeline analysis
Deleted file recovery
Threat remediation
Malware analysis


Pinpoint Threats &
Mitigate Risks

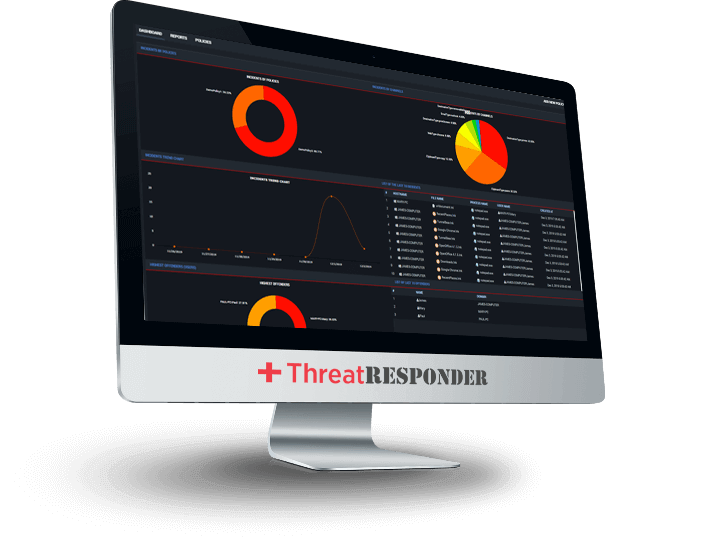
ThreatResponder enables organizations to identify active threats and vulnerabilities
With ThreatResponder deployed to your cloud, virtual machines, and physical systems, you protect these assets from determined adversaries. The product provides threat hunting capabilities, which allow you to sweep thousands of endpoints for vulnerabilities, indication of attacks/threats/compromise, or policy violations. The Platform enables you to pinpoint risky activities and mitigate the risk identified across the enterprise in real time.
Extend Your
Cyber Capabilities
Compromise / Breach Assessment
Ransomware Prevention
Security Health of Your Assets
Continuous Threat Detection, Prevention, and Hunting
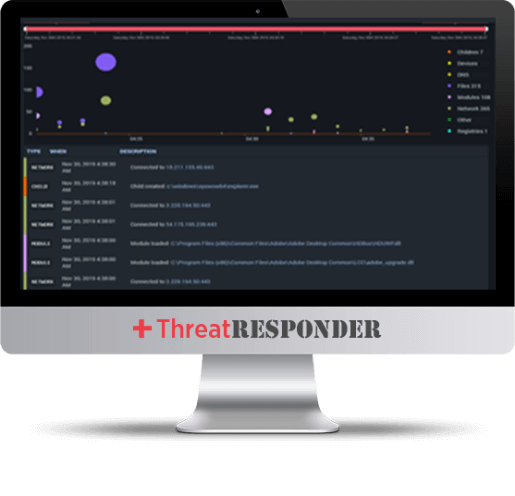
Incident Response & Forensics Investigation
Critical System Hardening & Application Control
Insider Threat, Data Loss, and User Behavior
Threat Intelligence

Why Organizations Choose
ThreatResponder®
-
Save Money
- Prevent Costly Cyber Attacks and Data Breaches
- Eliminate Ineffective Technologies and Gain High ROI
- Reduce/Eliminate Cost of Investigations
- Significantly Reduce the Cost of Security Operations
-
Gain Situational Awareness and Quickly Make Informed Decisions
By deploying ThreatResponder to protect your network, you gain threat visibility and pinpoint adversarial activities so you can quickly make informed decisions to prioritize and mitigate enterprise risks.
-
Protect Your Intellectual Property and Maintain Competitive/Strategic Advantage
Avoid business and operational disruption, protect crucial assets and maintain a competitive and strategic advantage.
-
Boost Efficiency and Productivity of Your Security Team and End Users
Stop employees and users from violating policy and enforce strict security policies at the endpoint. Do you want to prevent users from running specific programs or performing particular operations on certain corporate assets? ThreatResponder enables you to implement granular security controls so that your staff is more productive.
-
Stay Compliant (FISMA, PCI, GDPR, SOX, HIPAA) and Avoid Fines
Not complying with regulatory requirements could mean steep fines and penalties. By deploying ThreatResponder across your enterprise network, you protect your crucial assets and maintain regulatory compliance such as FISMA, PCI, GDPR, SOX, and HIPAA.
-
Improve Shareholders’ Value
Adopting ThreatResponder as your security arsenal eliminates unnecessary security operations costs, thereby increasing your shareholders’ value.
-
Preserve Your Reputation and Image
Deploying ThreatResponder protects you from a successful compromise, ensuring that you avoid unwanted media coverage and maintain or improve your business reputation.


Get Started Now With
ThreatResponder® Platform

Try ThreatResponder for 15 days and see what your current security defenses have been missing
Full enterprise deployment of ThreatResponder® takes minutes. Deploy a 15-day trial today and begin gaining insight into malicious activities that are bypassing your current defenses. Complete the form below to start gaining situational awareness, responding to, and neutralizing cyber attacks across your enterprise.
About Us
Realizing the need to protect corporate vital information and assets, NetSecurity was founded in 2004 as a cybersecurity company. Our company’s name is synonymous to cybersecurity. The company’s vision is “to be the brand of choice in endpoint security.” Our mission is “to predict, stop, and investigate advanced cyber attacks and data breaches.” To realize our vision and mission, we continue to provide innovative, world-class quality, customer-focused, and timely solutions to Defense and Intelligence entities, Government agencies, and private sector organizations.


















