5 Cybersecurity Predictions for 2024
Cybersecurity remains a paramount concern as technology advances and cyber threats evolve. Predicting the landscape of cybersecurity for 2024 involves understanding ongoing trends and potential developments that could shape the security landscape. The following predictions highlight key areas that might significantly impact cybersecurity in the coming years.
Key Predictions:
- AI-Driven Attacks and Defense: Artificial intelligence (AI) is set to play a pivotal role in cyber warfare. Cybercriminals are likely to leverage AI to create more sophisticated attacks, including AI-generated malware and automated evasion techniques. Conversely, defenders will harness AI to bolster security measures, using machine learning for threat detection, behavioral analysis, and anomaly identification.
- Ransomware Evolution: Ransomware attacks are expected to become increasingly targeted and multifaceted. Attackers may adopt new strategies such as double extortion, where they steal sensitive data before encrypting it, further incentivizing victims to pay the ransom. Moreover, with the rise of interconnected devices through IoT and the deployment of 5G networks, ransomware threats could expand to exploit these technologies.
- Zero Trust Architecture Adoption: Organizations are shifting towards Zero Trust Architecture, which assumes no implicit trust within or outside the network perimeter. By 2024, a broader implementation of Zero Trust principles is likely, emphasizing strict identity verification, least privilege access, micro-segmentation, and continuous monitoring to enhance security posture.
- Regulatory Impact on Security Practices: Anticipate an evolving regulatory landscape that could significantly affect cybersecurity practices. Governments worldwide might introduce new data protection laws or refine existing ones, compelling organizations to adhere to stringent compliance requirements. These regulations could influence how businesses handle and safeguard sensitive data, emphasizing the need for robust security measures.
- Rise of Quantum-Safe Cryptography: With the progression of quantum computing, the threat to current encryption methods increases. By 2024, there might be a growing emphasis on adopting quantum-safe cryptography to ensure data remains secure against potential quantum-based attacks. Research and development in this area will intensify as organizations seek encryption methods resistant to quantum decryption algorithms.
How Can You Safeguard Your Organization in 2024?
As the threat landscape continues to evolve, traditional security measures are often insufficient. You need a more comprehensive approach to cybersecurity that goes beyond perimeter defenses. This is where ThreatResponder by NetSecurity comes into play. ThreatResponder is an all-in-one, unified, cloud-native, machine learning-driven cyber-resilient endpoint security platform.
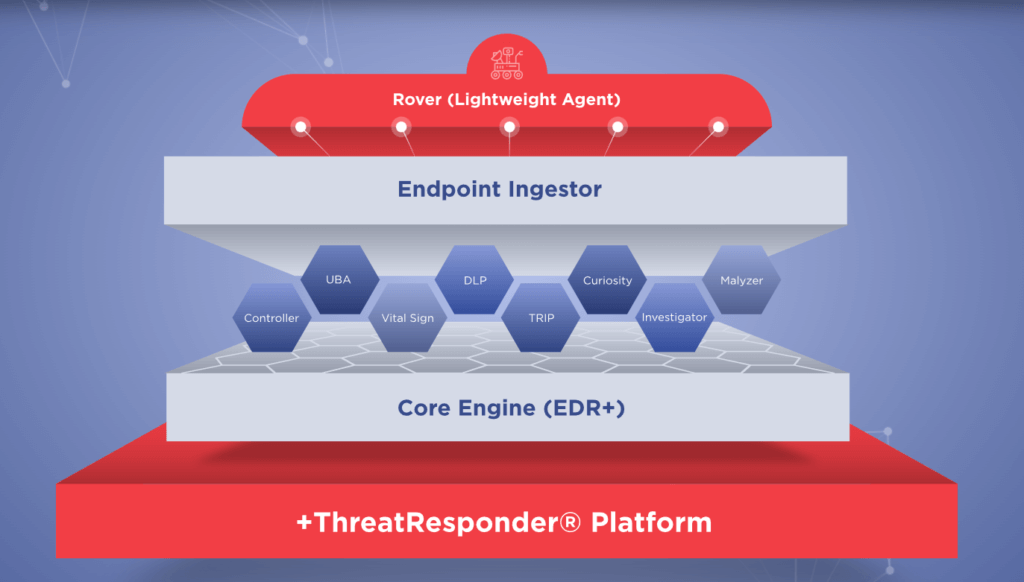
These pillars collectively create a formidable defense system against a wide range of cyber threats. However, in an ever-evolving digital world, there’s always room for improvement and expansion.
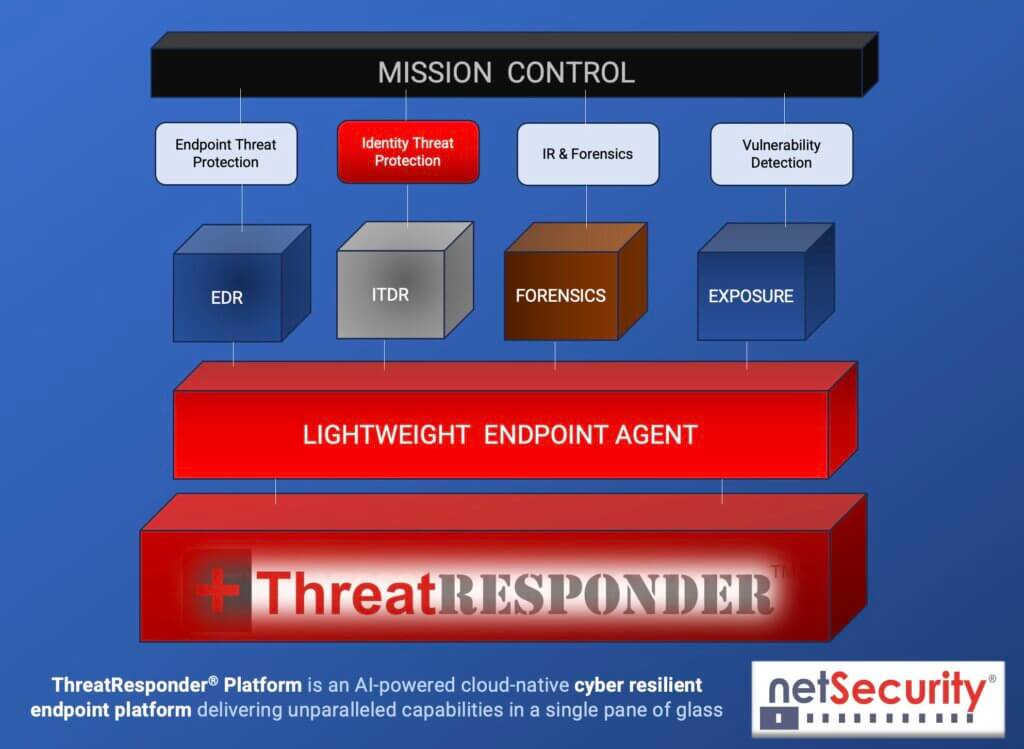
It is designed to provide cybersecurity teams with the necessary tools and insights to defend their organizations effectively. Let’s take a closer look at the core features of ThreatResponder:
Endpoint Detection and Response (EDR)
Endpoint Detection and Response is a critical component of modern cybersecurity. ThreatResponder continuously monitors endpoints (devices and servers) for signs of suspicious activities, such as malware infections or unusual behavior. When a threat is detected, ThreatResponder responds in real-time to mitigate the risk, making it an invaluable asset in threat containment and incident response.
Identity Threat Detection and Response
User identities are a prime target for attackers. ThreatResponder analyzes user behaviors and privileges to identify suspicious activities and potential threats. By understanding user identity and access patterns, it can detect unauthorized access and protect sensitive data from breaches.
Forensics
In the aftermath of a security incident, forensics play a crucial role in understanding the attack and its impact. ThreatResponder provides detailed forensic capabilities, helping CISOs and their teams analyze the scope of an incident, track the attacker’s movements, and collect evidence for potential legal action.
Threat Hunting
Proactive threat hunting is essential for identifying threats before they cause significant damage. ThreatResponder equips CISOs with advanced threat-hunting tools, enabling them to search for hidden threats, vulnerabilities, and indicators of compromise within their organization’s network.
Vulnerability Detection
Identifying and patching vulnerabilities is a fundamental part of cybersecurity. ThreatResponder helps CISOs stay on top of vulnerabilities within their organization’s systems and applications, allowing them to prioritize and address weaknesses before they are exploited by attackers.
Try ThreatResponder for Free!
Are you ready to take the next step in defending your organization against cyber threats? Explore ThreatResponder by NetSecurity today and bolster your organization’s cybersecurity defenses.

Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).