Why Cyber Attacks are Increasing in 2024? How Can You Stay Protected
The internet has become an essential part of our lives, driving communication, commerce, and even critical infrastructure. However, this interconnectedness has also created a vast attack surface for cybercriminals. In 2024, cyber attacks are on the rise, posing a significant threat to individuals, businesses, and national security.
Top Cyber Threats to the US in 2024
The methods and targets of cyberattacks are constantly evolving. Comparing 2023 and 2024, we see a shift towards:
- Geopolitical and Nation-State Sponsored Attacks: This growing threat involves cyberattacks launched by foreign governments for espionage, disruption, or influencing political outcomes.
- Ransomware: This tactic continues to be a significant threat, with attackers targeting not just businesses but also critical infrastructure like hospitals.
- AI-powered attacks: Cybercriminals are increasingly using artificial intelligence (AI) to automate tasks, personalize phishing scams, and develop more sophisticated malware.
- Supply chain attacks: Exploiting vulnerabilities in third-party vendors remains a popular tactic, allowing attackers to gain access to a wider range of targets.
- Phishing Attacks: These deceptive emails and messages continue to trick users into revealing sensitive information or clicking malicious links.
The Grim Reality of Increasing Cyber Attacks
Cyber attacks have been on the rise globally, with the US being a prime target. In 2023, the US was the target of 46 percent of cyber attacks. In Q1 2024, there was a 28% increase in the average number of cyber attacks per organization from the last quarter of 2023. Cybercrime rates have increased by 300% since the beginning of the COVID-19 pandemic. Organizations lose more than $17,000 every minute due to phishing.
Top 5 Reasons for the Increase in Cyber Attacks in 2024
Several factors are contributing to the surge in cyber attacks:
-
Evolving Attack Techniques: Cybercriminals are constantly refining their methods. AI-powered automation allows them to launch large-scale attacks with minimal effort. Techniques like social engineering are becoming more sophisticated, making it harder for individuals to identify and avoid them.
-
Exploitable Vulnerabilities: The rapid adoption of new technologies, particularly in the Internet of Things (IoT) and cloud computing, introduces new vulnerabilities that attackers can exploit. Legacy systems with unpatched software remain a major target.
-
Increased Financial Rewards: The potential financial rewards from cyber attacks continue to grow. Businesses rely heavily on digital data, making them more willing to pay ransoms to avoid disruption and reputational damage. This motivates cybercriminals to invest time and resources in developing new attack methods.
-
Remote Work Vulnerabilities: The shift to remote work due to the pandemic has created new security challenges. Employees working outside traditional office environments may use less secure networks and personal devices, increasing the attack surface.
-
Ineffective Protection Tools: Many organizations still rely on outdated or under-resourced cybersecurity tools for threat detection, monitoring, and protection, leaving them vulnerable to attack.
Stay Protected with NetSecurity’s ThreatResponder: Your Modernized Defense System
As the threat landscape continues to evolve, traditional security measures are often insufficient. CISOs need a more comprehensive approach to cybersecurity that goes beyond perimeter defenses. This is where ThreatResponder by NetSecurity comes into play. ThreatResponder is an all-in-one, unified, cloud-native, machine learning-driven cyber-resilient endpoint security platform.
ThreatResponder, designed and developed by NetSecurity, is an all-in-one cloud-native cyber-resilient endpoint platform that embodies these very principles. Packed with cutting-edge technology, ThreatResponder empowers you to consolidate security, harness the power of AI, automate digital forensics and incident response, gain real-time insights, enhance threat hunting, and simplify threat and vulnerability management
ThreatResponder is more than just a product; it’s a paradigm shift in how you approach cyber security. It equips you with the tools and intelligence to proactively anticipate threats, swiftly respond to incidents, and ultimately, fortify your defenses and keep your digital assets safe and protected.
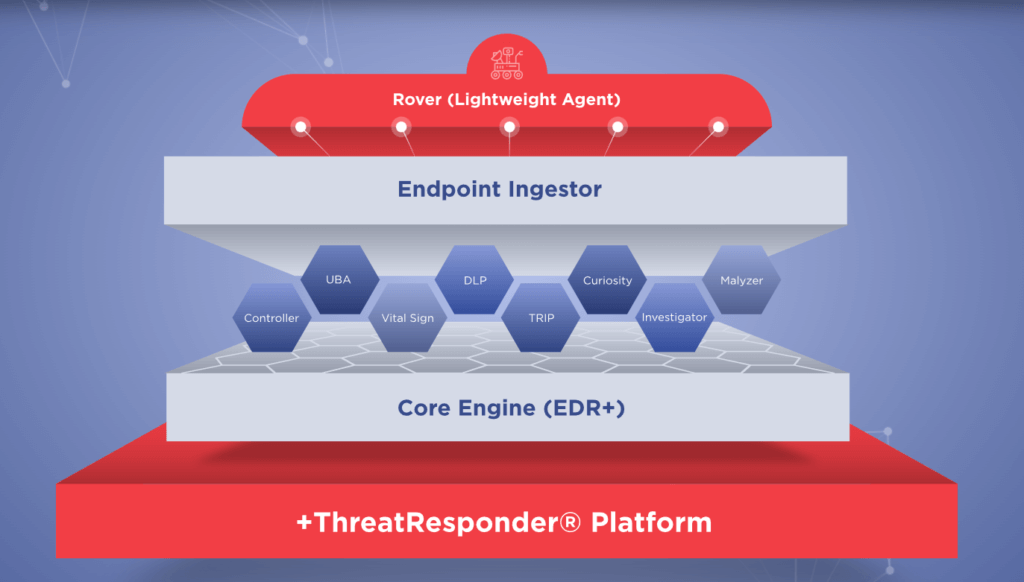
These pillars collectively create a formidable defense system against a wide range of cyber threats. However, in an ever-evolving digital world, there’s always room for improvement and expansion.
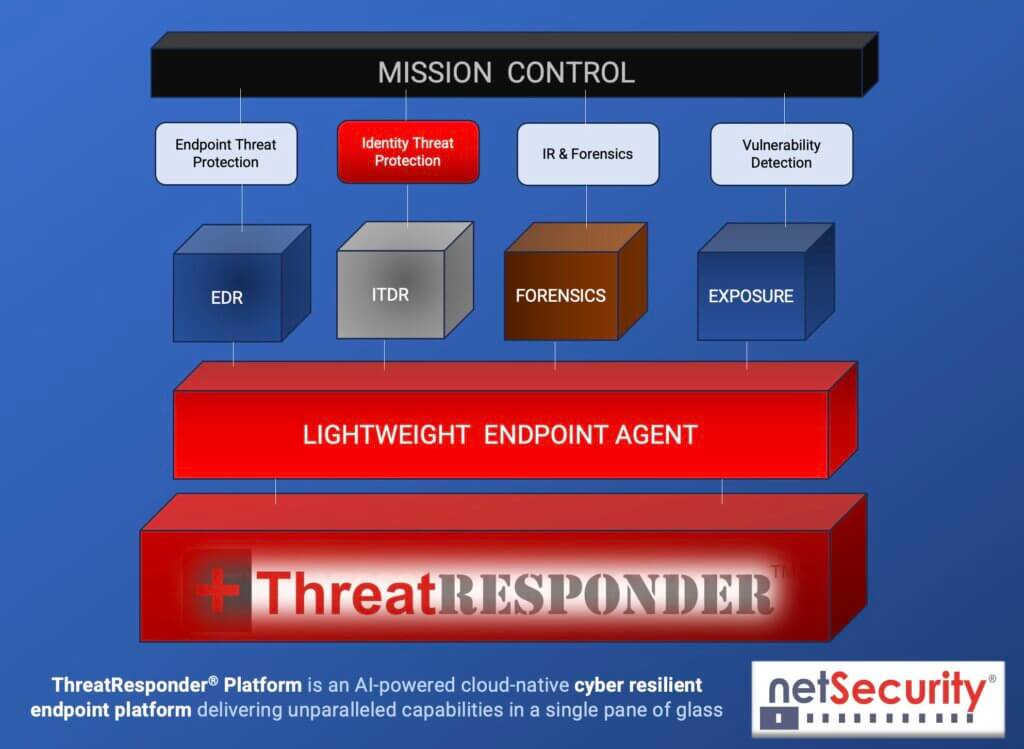
It is designed to provide cybersecurity teams with the necessary tools and insights to defend their organizations effectively. Let’s take a closer look at the core features of ThreatResponder:
- Endpoint Detection and Response (EDR): Endpoint Detection and Response is a critical component of modern cybersecurity. ThreatResponder continuously monitors endpoints (devices and servers) for signs of suspicious activities, such as malware infections or unusual behavior. When a threat is detected, ThreatResponder responds in real-time to mitigate the risk, making it an invaluable asset in threat containment and incident response.
- Identity Threat Detection and Response: User identities are a prime target for attackers. ThreatResponder analyzes user behaviors and privileges to identify suspicious activities and potential threats. By understanding user identity and access patterns, it can detect unauthorized access and protect sensitive data from breaches.
- Forensics: In the aftermath of a security incident, forensics play a crucial role in understanding the attack and its impact. ThreatResponder provides detailed forensic capabilities, helping CISOs and their teams analyze the scope of an incident, track the attacker’s movements, and collect evidence for potential legal action.
- Threat Hunting: Proactive threat hunting is essential for identifying threats before they cause significant damage. ThreatResponder equips CISOs with advanced threat hunting tools, enabling them to search for hidden threats, vulnerabilities, and indicators of compromise within their organization’s network.
- Vulnerability Detection: Identifying and patching vulnerabilities is a fundamental part of cybersecurity. ThreatResponder helps CISOs stay on top of vulnerabilities within their organization’s systems and applications, allowing them to prioritize and address weaknesses before attackers exploit them.
Don’t wait for disaster to strike. Modernize your threat detection capabilities with our ThreatResponder platform today. Contact NetSecurity to learn more and request a free demo.
Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).











