The Imperative of a Unified Security Solution in 2024: NetSecurity’s ThreatResponder
In the digital age, where businesses rely heavily on technology, cybersecurity has emerged as a critical concern. The proliferation of cyber threats, ranging from ransomware attacks to data breaches, underscores the urgency for companies to fortify their defenses. Traditional security measures, while effective to some extent, are no longer sufficient in the face of increasingly sophisticated threats. A Unified Security Solution (USS) offers a holistic approach to cybersecurity, integrating multiple capabilities into a unified framework. In this paper, we explore why a USS is essential for companies to bolster their cyber resilience in 2024.
Evolving Cyber Threat Landscape:
The cyber threat landscape is in a state of constant flux, with threat actors employing diverse tactics to exploit vulnerabilities. From nation-state-sponsored attacks to financially motivated cybercrime, organizations confront a myriad of threats that pose significant risks to their operations and reputation. The rise of remote work and the Internet of Things (IoT) further complicates the security landscape, expanding the attack surface and creating new vectors for exploitation.
Limitations of Siloed Security Tools:
Traditional security approaches often rely on siloed tools and solutions, each addressing specific aspects of cybersecurity. While these tools may be effective in isolation, they lack the interoperability and holistic visibility needed to combat sophisticated threats comprehensively. Siloed security tools result in fragmented security postures, making it difficult for organizations to detect, respond to, and remediate cyber threats in a timely manner.
The Concept of Unified Security Solution (USS):
A Unified Security Solution (USS) integrates various security capabilities within a centralized platform, offering a cohesive and proactive approach to cybersecurity. By consolidating functions such as Endpoint Detection and Response (EDR), threat hunting, forensics, identity threat detection, and vulnerability management, a USS provides organizations with a comprehensive view of their security posture. This unified approach enables faster threat detection, improved incident response, and better resource allocation, enhancing overall cyber resilience.
Benefits of a Unified Security Solution:
- Enhanced Visibility and Control: A USS provides organizations with centralized visibility into their security posture, allowing them to monitor, manage, and control security incidents more effectively. By consolidating security data and insights from multiple sources, organizations can gain a holistic view of their risk landscape and make informed decisions to mitigate threats.
- Improved Threat Detection and Response: By integrating advanced analytics and threat intelligence feeds, a USS enables organizations to detect and respond to cyber threats in real-time. Automated response capabilities streamline incident triage and remediation, reducing mean time to detect (MTTD) and mean time to respond (MTTR) metrics and minimizing the impact of security incidents.
- Streamlined Compliance Management: With regulatory requirements becoming increasingly stringent, organizations must demonstrate compliance with industry standards and data protection regulations. A USS facilitates compliance management by providing audit trails, generating compliance reports, and automating routine compliance tasks, helping organizations maintain regulatory compliance and avoid costly fines or penalties.
- Cost Efficiency and Resource Optimization: By consolidating security functions within a unified platform, organizations can eliminate redundancies, streamline workflows, and optimize resource allocation. A USS reduces the complexity of managing multiple security tools and vendors, lowering operational costs and improving return on investment (ROI) for cybersecurity initiatives.
NetSecurity’s ThreatResponder Platform in a Nutshell
ThreatResponder Platform is an all-in-one cloud-native cyber resilient endpoint platform with unified capabilities enabling endpoint threat detection, prevention, response, analytics, intelligence, investigation, and hunting products. Once lightweight agents (“Rovers”) are deployed, you gain situational awareness and immediate threat visibility into hundreds and thousands of endpoints, respond to nation-state and insider threats, and neutralize cyber attacks quickly. ThreatResponder® allows investigators to conduct incident response and computer forensics investigation on a remote endpoint.
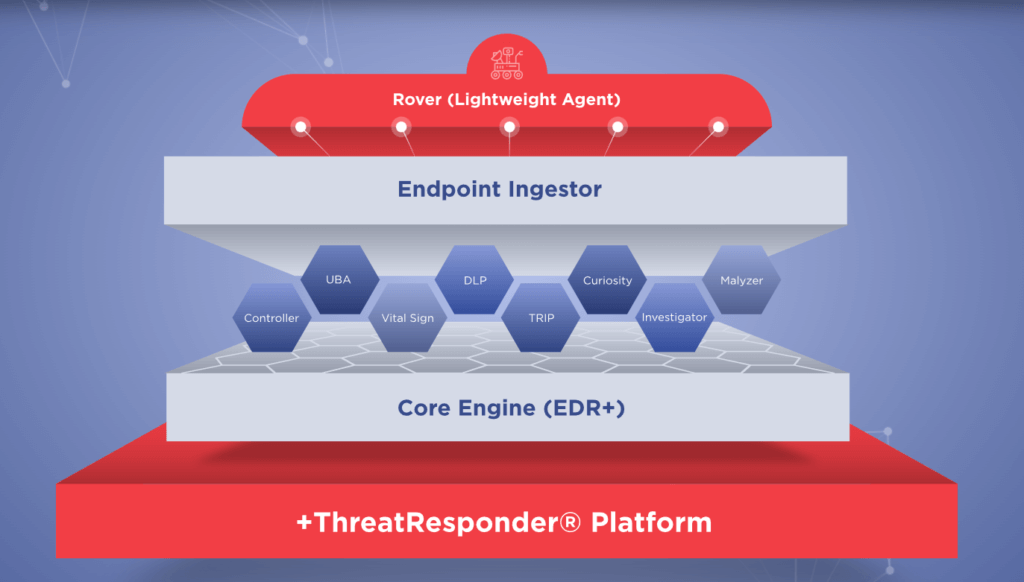
- Endpoint Threat Protection: At the heart of our platform lies robust endpoint threat protection. This critical component ensures that your devices, the entry points for many cyberattacks, are shielded from evolving threats.
- Incident Threat: In the unfortunate event of a security breach, a swift and effective response is essential. Our platform equips you with the tools needed to investigate incidents, gather forensics data, and take decisive action.
- Proactive Threat Hunting: Waiting for threats to come to you is not an option in today’s cybersecurity landscape. With ThreatResponder, you can proactively seek out vulnerabilities and threats, staying one step ahead of potential attackers.
- Vulnerability Detection: Identifying and patching vulnerabilities is crucial to reducing your attack surface. Our platform automates the process of vulnerability detection, helping you stay secure.
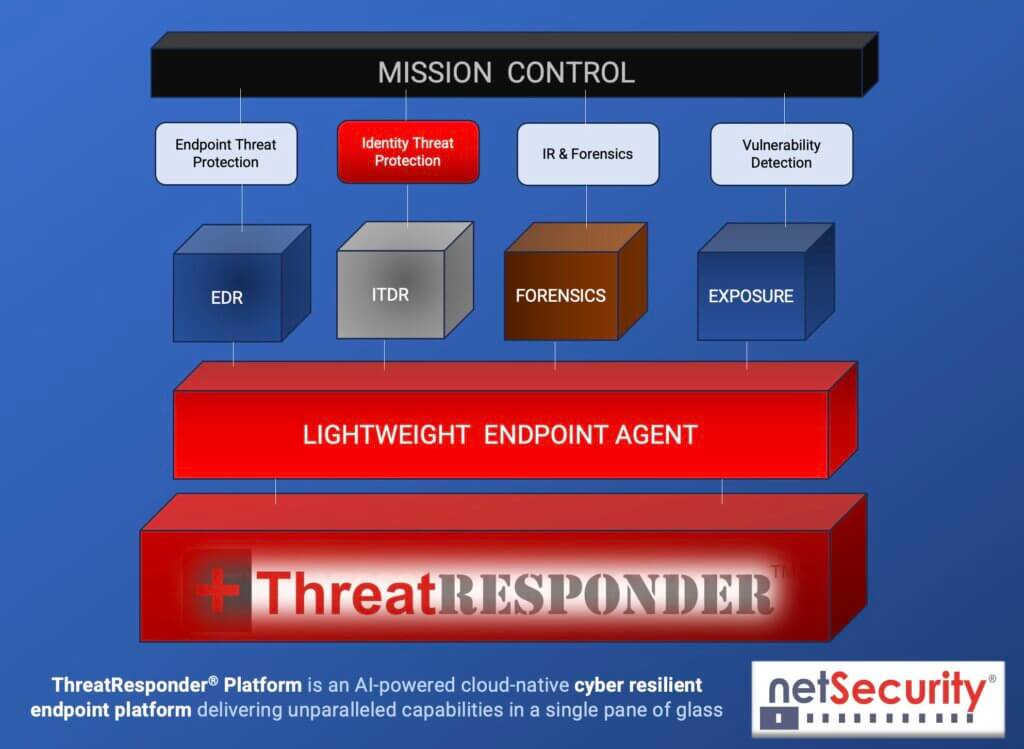
a. Endpoint Detection and Response (EDR): At the heart of our platform lies a robust EDR solution that monitors endpoint devices for suspicious activities, allowing organizations to detect and respond to threats in real-time. By leveraging advanced analytics and machine learning algorithms, ThreatResponder can identify anomalous behavior indicative of potential cyber threats, enabling swift mitigation actions.
b. Identity Threat Detection: ThreatResponder’s identity threat detection focuses on monitoring user activity and identifying suspicious behavior that may indicate unauthorized access or credential compromise. By analyzing user behavior patterns and enforcing least privilege access controls, organizations can mitigate the risk of insider threats and credential-based attacks.
c. Incident Response: Incident response is a critical component of ThreatResponder aimed at effectively managing and mitigating security incidents. ThreatResponder allows for identifying, assessing, and responding promptly to security breaches or cyber-attacks.
d. Forensics: ThreatResponder’s Forensic capabilities enable organizations to investigate security incidents, gather evidence, and understand the root causes of breaches or security incidents. By conducting thorough forensic analysis, organizations can enhance their incident response capabilities and strengthen their defenses against future attacks.
e. Threat Hunting: ThreatResponder’s Threat hunting module involves proactively searching for indicators of compromise (IOCs) within an organization’s network environment. This proactive approach helps identify hidden threats that may evade traditional security measures, allowing organizations to neutralize them before they cause harm preemptively.
f. Vulnerability Management: Vulnerability management involves identifying, prioritizing, and remedying security vulnerabilities within an organization’s IT infrastructure. ThreatResponder’s Exposure module enables regular scanning for vulnerabilities, assessing their severity, and helping in prioritizing vulnerabilities for applying patches or mitigations; organizations can reduce the likelihood of exploitation by malicious actors.
These pillars collectively create a formidable defense system against a wide range of cyber threats.
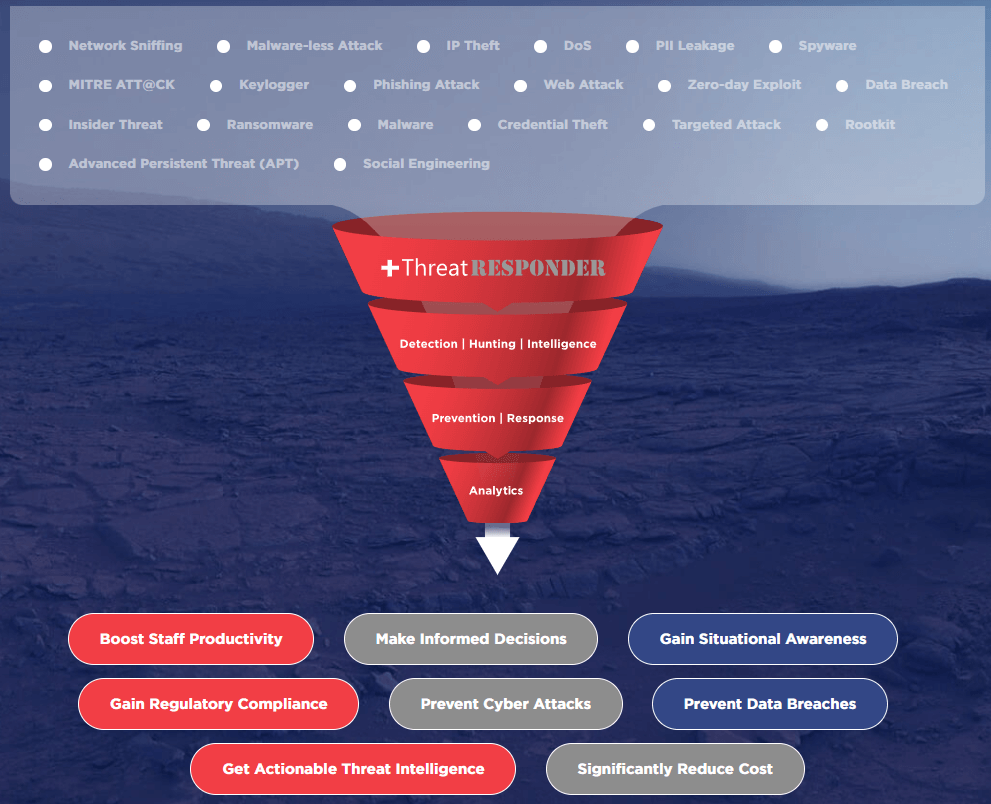
Cybersecurity is a complex field with a multitude of threats and challenges. Managing various security tools and solutions can be a daunting task. This is where the power of integration comes into play. A unified platform like ThreatResponder streamlines your cybersecurity operations. Instead of juggling multiple tools from different vendors, you have a single, centralized hub for monitoring, responding to incidents, and managing threats. This integration leads to more efficient workflows, reduced operational overhead, and better visibility into your organization’s security posture.
When it comes to cybersecurity, every second counts. A seamlessly integrated platform ensures that information flows in real-time, enabling faster decision-making and response to potential threats. It’s a game-changer in the race against cybercriminals.
Try ThreatResponder for Free
Want to try our ThreatResponder, cutting-edge Endpoint Detection & Response (EDR), and ThreatResponder FORENSICS, the Swiss knife for forensic investigators in action? Click on the below button to request a free demo of our NetSecurity’s ThreatResponder platform.
Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).











