
Datasheets and Brochures
Learn more about our offerings

NetSecurity Capability Statement
NetSecurity Capability Statement
NetSecurity Capability Statement

NetSecurity ThreatResponder Capability Brief
NetSecurity ThreatResponder Capability Brief
NetSecurity ThreatResponder Capability Brief

NetSecurity ThreatResponder Datasheet
NetSecurity ThreatResponder Datasheet
NetSecurity ThreatResponder Datasheet

NetSecurity ThreatResponder IR Datasheet
NetSecurity ThreatResponder IR Datasheet
NetSecurity ThreatResponder IR Datasheet

NetSecurity ThreatResponder Use Cases
NetSecurity ThreatResponder Use Cases
NetSecurity ThreatResponder Use Cases

Battle Cards
Learn more about our offerings
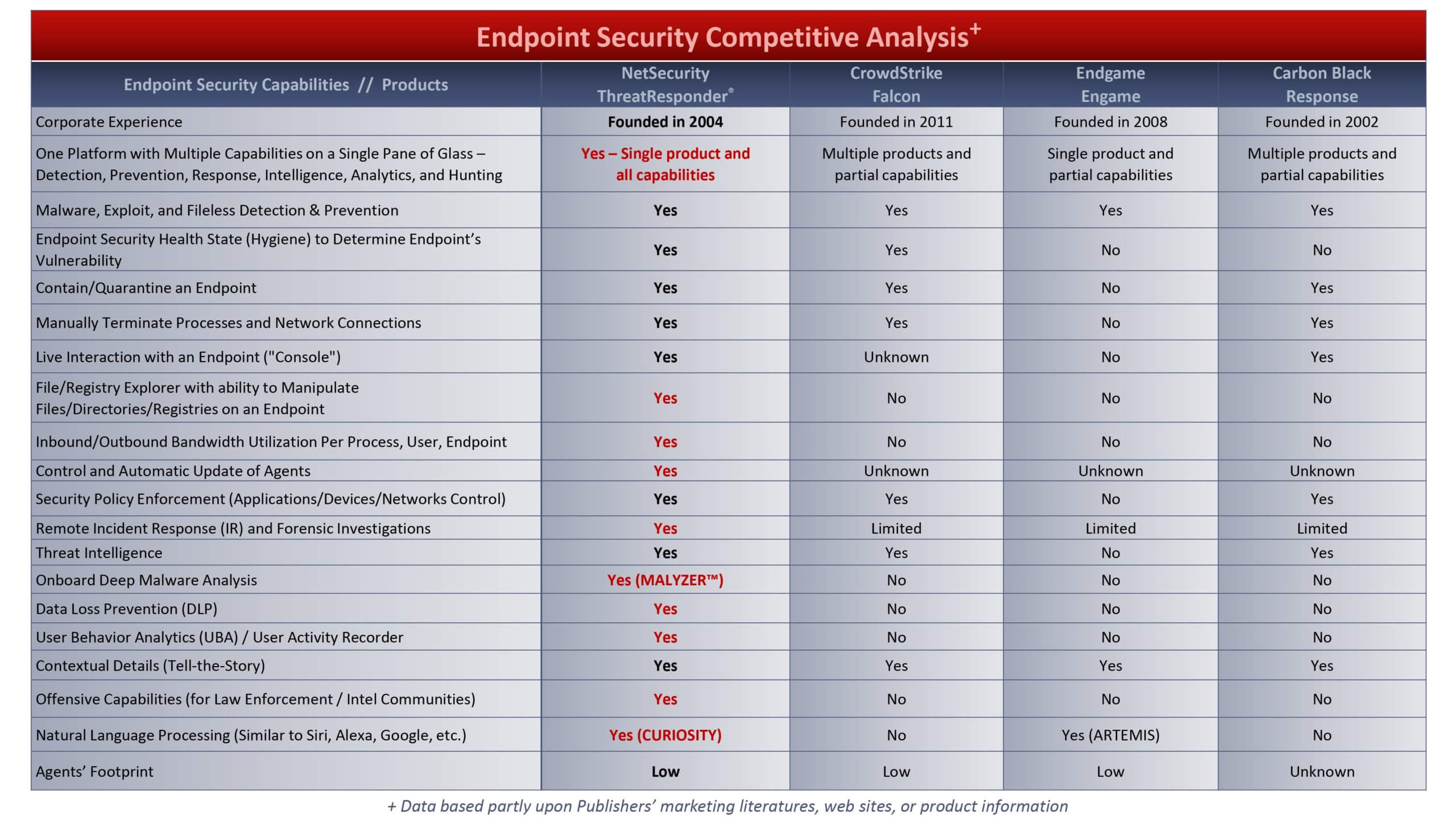
NetSecurity ThreatResponder Competitve Analysis
NetSecurity ThreatResponder Competitve Analysis
NetSecurity ThreatResponder Competitve Analysis

Presentations
Learn more about our offerings

Advanced Persistent Threats Sharpening Your Defensive Arsenals
Advanced Persistent Threats Sharpening Your Defensive Arsenals
Advanced Persistent Threats Sharpening Your Defensive Arsenals-FINAL

Man and Machine
Man and Machine
Man and Machine Forming a Perfect Union to Mature Security Programs Keynote Address -- Inno Eroraha (NetSecurity)

Jujitsu for Auditors Conduting Legally Defensible Investigations
Jujitsu for Auditors Conduting Legally Defensible Investigations
NetSecurity Inno Eroraha IIA ISACA Computer Forensics Jujitsu for Auditors Conduting Legally Defensible Investigations

Data Breach Investigations and Readiness
Data Breach Investigations and Readiness
NetSecurity Inno Eroraha ISSA-DC Data Breach Investigations and Readiness

Computer Forensics Jujitsu-Gathering Volatile_Data from the Crime Scene
Computer Forensics Jujitsu-Gathering Volatile_Data from the Crime Scene
NetSecurity-Computer Forensics Jujitsu Gathering Volatile Data from the Crime Scene ISSA Baltimore

ThreatResponder® Videos
Learn more about our offerings

1- ThreatResponder(R) Platform - Phishing Attack - Detection+Prevention - 042018
1- ThreatResponder(R) Platform - Phishing Attack - Detection+Prevention - 042018
ThreatResponder(r) Platform -- A video demonstrating phishing attacks detection and prevention.
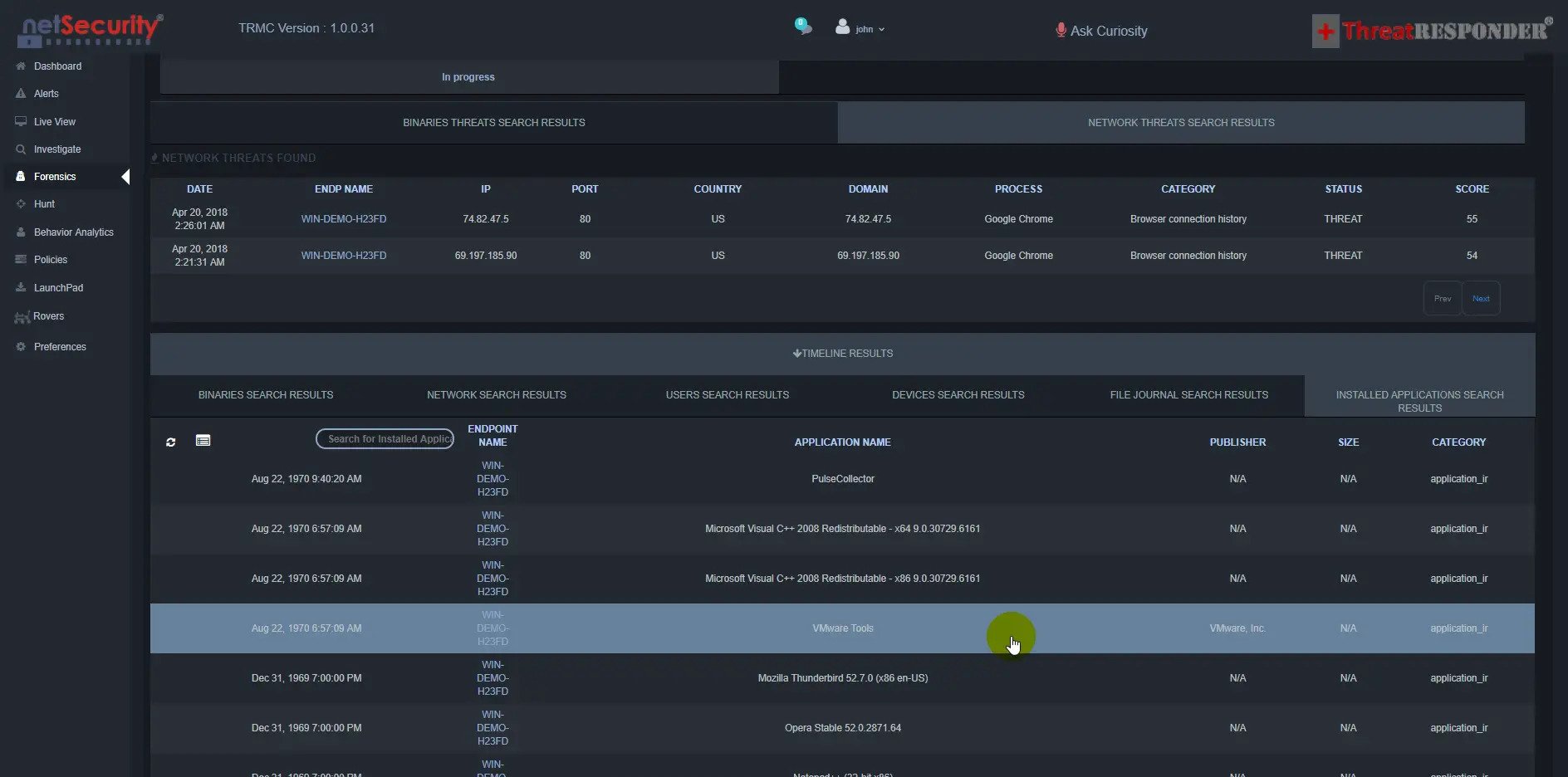
2- ThreatResponder(R) Platform - Incident Response + Forensics - 042018
2- ThreatResponder(R) Platform - Incident Response + Forensics - 042018
2- ThreatResponder(R) Platform - Incident Response + Forensics - 042018
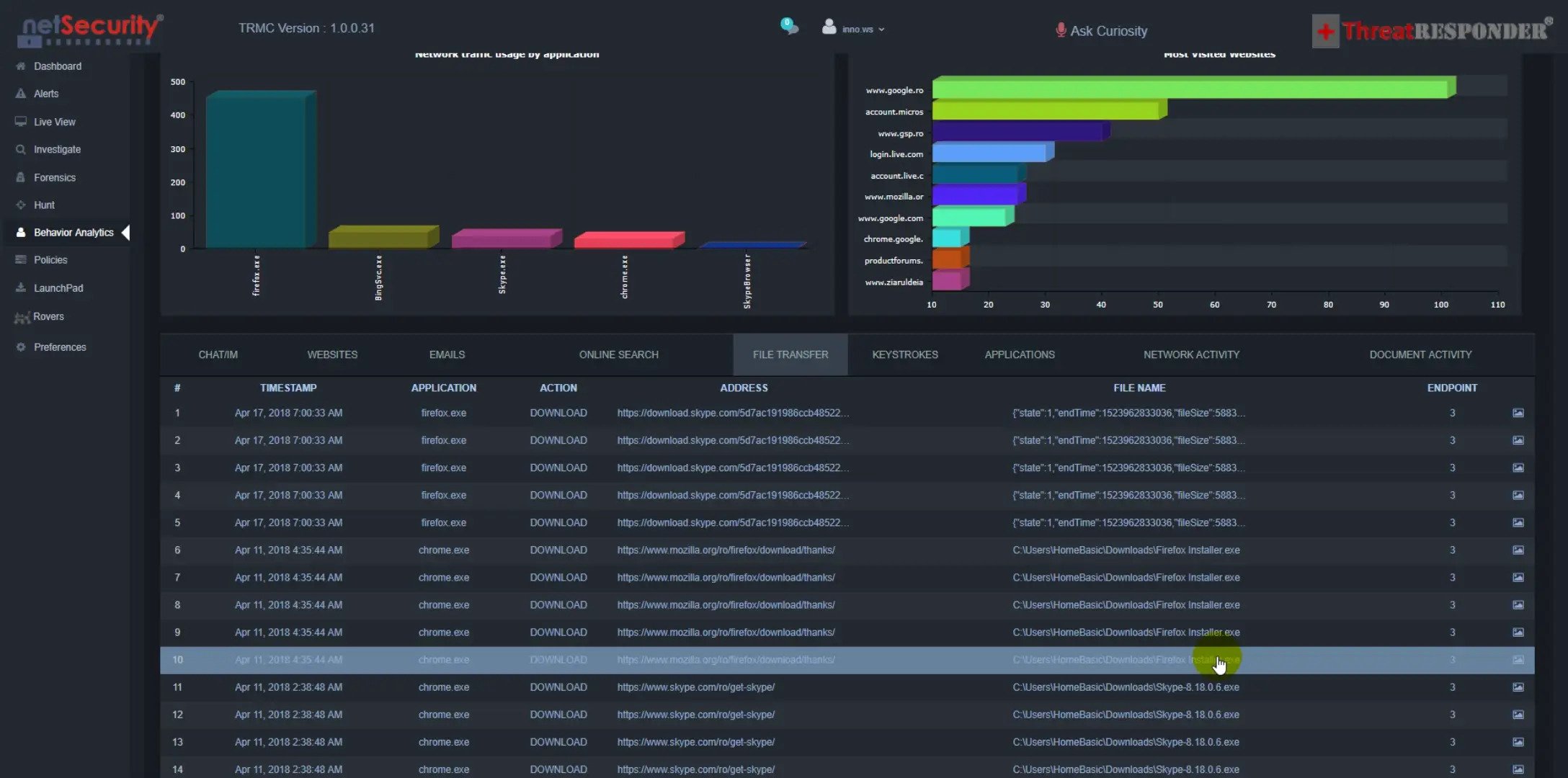
3- ThreatResponder(R) Platform - Insider Threat - User Behavior Analytics (UBA) - 042018
3- ThreatResponder(R) Platform - Insider Threat - User Behavior Analytics (UBA) - 042018
3- ThreatResponder(R) Platform - Insider Threat - User Behavior Analytics (UBA) - 042018
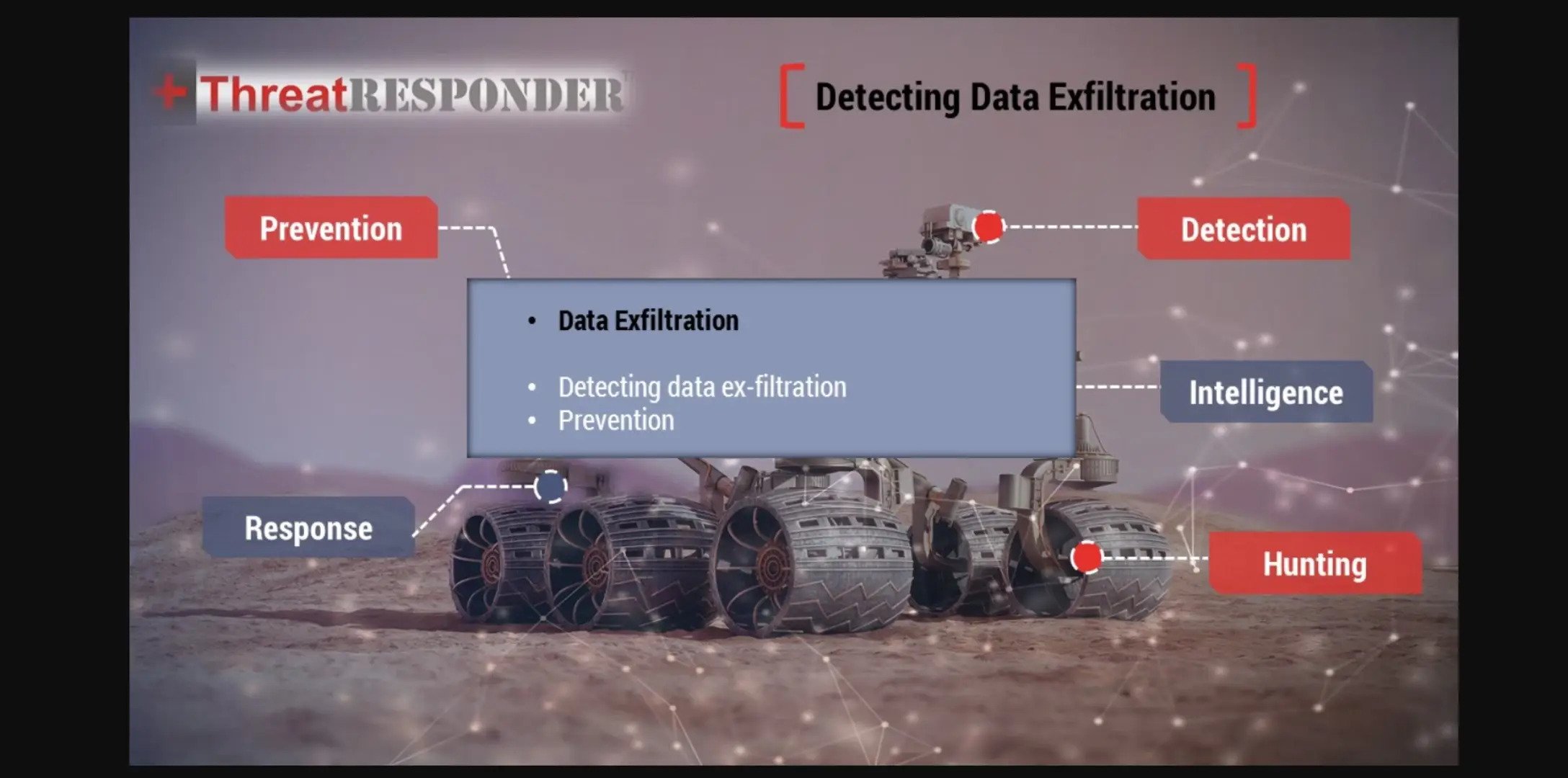
4- ThreatResponder(R) Platform - Data Exfiltration - 042018
4- ThreatResponder(R) Platform - Data Exfiltration - 042018
4- ThreatResponder(R) Platform - Data Exfiltration - 042018
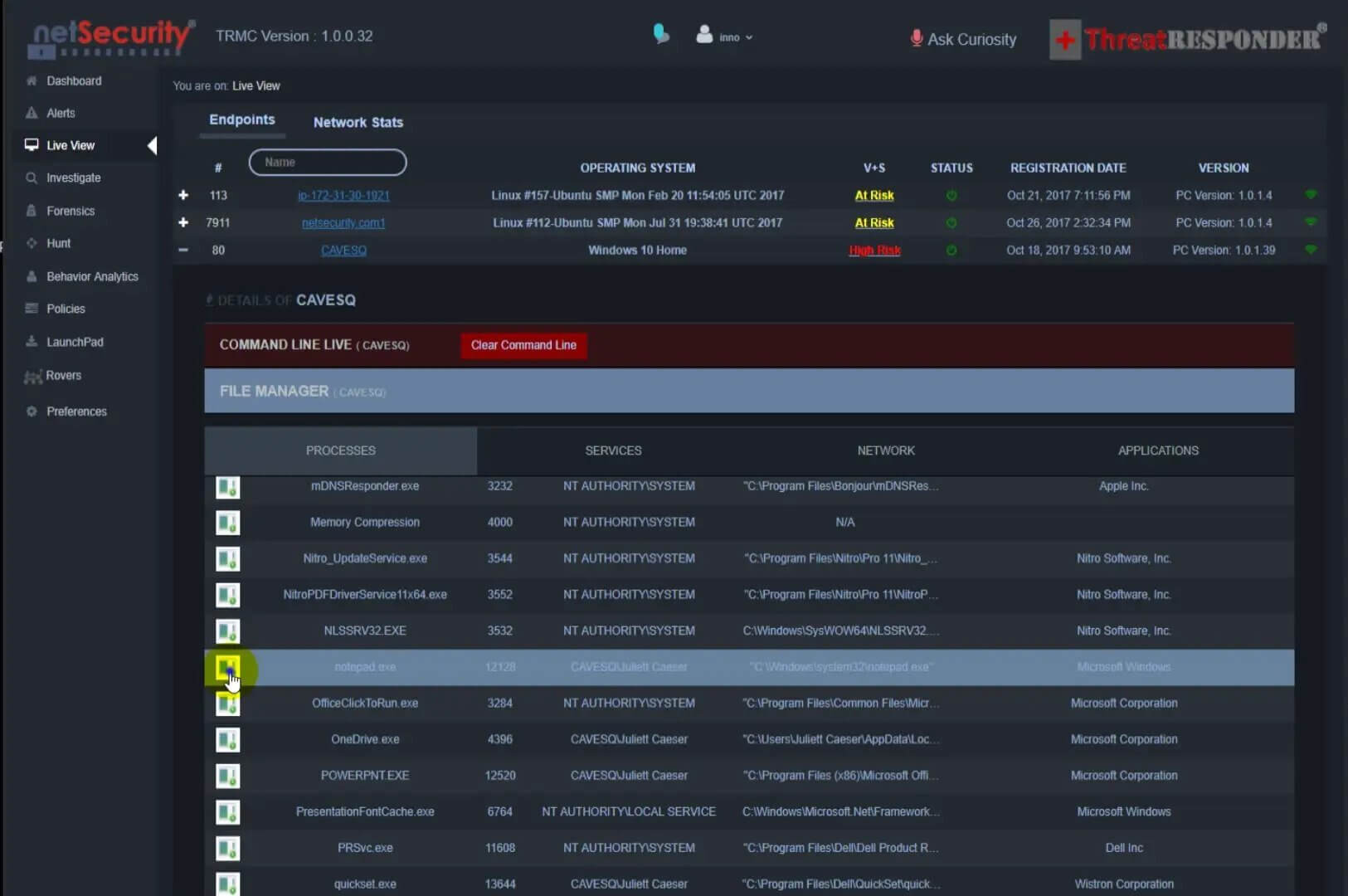
5- ThreatResponder(R) Platform - Disrupting the Adversary - Interacting with the Endpoint - 042018
5- ThreatResponder(R) Platform - Disrupting the Adversary - Interacting with the Endpoint - 042018
5- ThreatResponder(R) Platform - Disrupting the Adversary - Interacting with the Endpoint - 042018

ThreatResponder(R) Platform Phishing Attack Detection and Prevention
ThreatResponder(R) Platform Phishing Attack Detection and Prevention
ThreatResponder(R) detects and prevents advanced cyber attacks and data breaches in real-time at the endpoint. This video shows how ThreatResponder(R) detects and prevents phishing attacks.
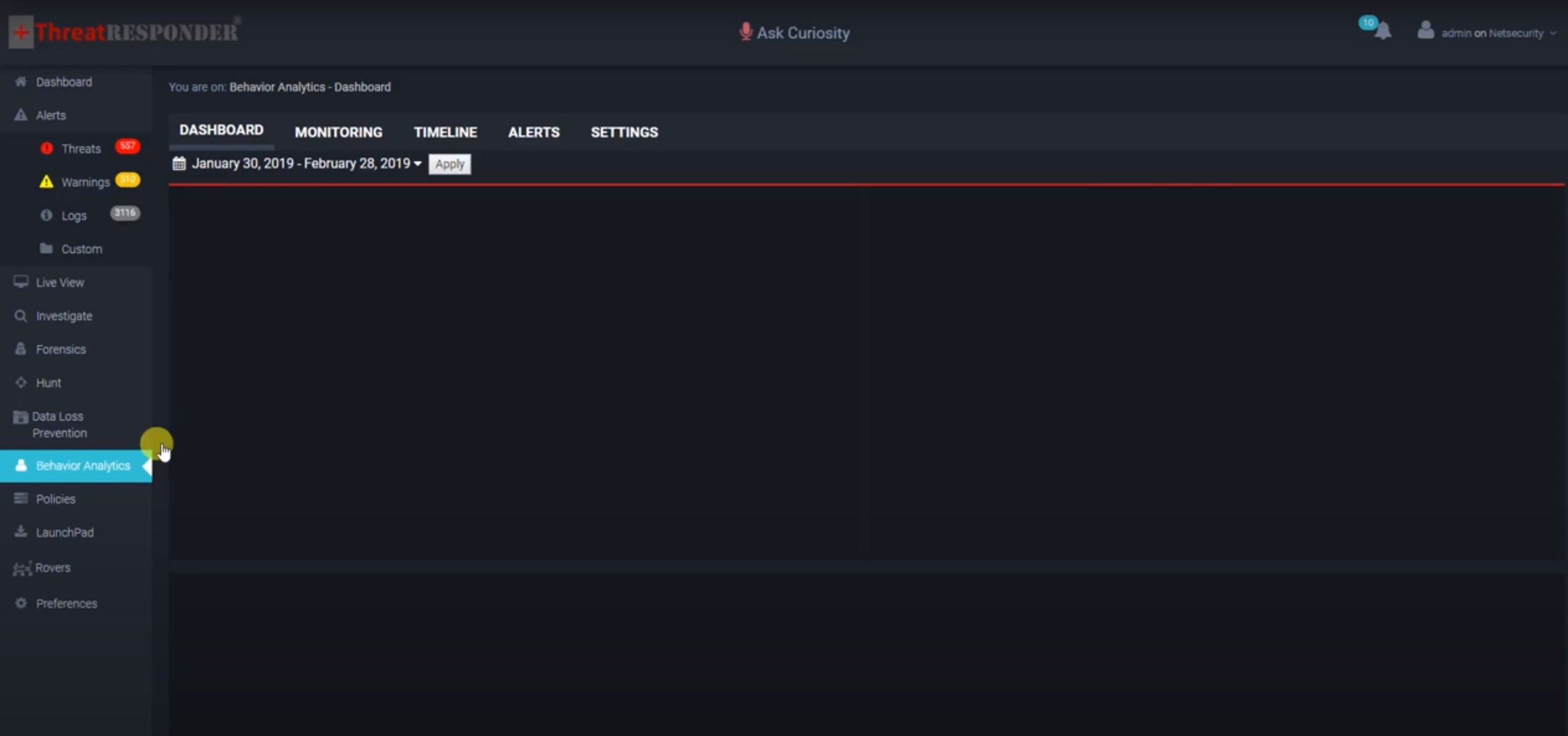
+ThreatResponder(r) Platform: User Behavior Analytics (UBA) Module in Action
+ThreatResponder(r) Platform: User Behavior Analytics (UBA) Module in Action
ThreatResponder(r) Platform:: User Behavior Analytics (UBA) module highlighting users' activities on the endpoint.





