Beyond the Surface: How ThreatResponder Enhances Your Security Posture
In the current cybersecurity landscape, the importance of endpoint telemetry cannot be overstated. Endpoints, which include devices like computers, laptops, and mobile devices, serve as the front lines in the battle against cyber threats. As organizations increasingly embrace remote work and bring-your-own-device (BYOD) policies, the attack surface has expanded, making endpoint security a critical component of a robust cybersecurity strategy.
One key aspect of effective endpoint security is telemetry. The ability to see and understand what is happening on each endpoint in real-time is crucial for detecting and responding to potential threats. This is where ThreatResponder, the cutting-edge cyber-resilient endpoint platform, an innovation from NetSecurity, comes into play. Let’s understand what is the significance of endpoint telemetry and how ThreatResponder enhances your security posture.
The Challenge of Endpoint Telemetry
Endpoints are often the initial targets of cyber attacks, serving as entry points for malicious actors seeking to infiltrate a network. Whether it’s through phishing emails, malicious downloads, or other means, endpoints are vulnerable to a variety of threats.
One of the significant challenges in endpoint security is the lack of visibility into the activities and behaviors of endpoints. Traditional security measures often provide a binary view — either a file or application is deemed safe, or it’s flagged as malicious. This binary approach falls short in today’s threat landscape, where threats are polymorphic, adapting and changing to evade detection.
Endpoint visibility refers to the ability to monitor and analyze activities on each endpoint in real-time. It involves understanding what applications are running, what processes are taking place, and what network connections are being established. Without adequate visibility, security teams are essentially operating in the dark, unable to detect subtle signs of a potential breach until it’s too late.
Why Endpoint Visibility Matters
- Early Detection of Threats:Endpoint visibility allows security teams to detect threats at an early stage. By monitoring the behavior of processes and applications, anomalies can be identified, indicating a potential security incident. ThreatResponder takes this a step further by employing advanced machine learning based behavior analysis to recognize patterns associated with various types of attacks, including zero-day exploits and fileless malware.
- Reduced Mean Time to Detect (MTTD):The longer it takes to detect a security incident, the greater the potential impact. Endpoint visibility significantly reduces the Mean Time to Detect (MTTD) by providing real-time insights into endpoint activities. ThreatResponder’s continuous monitoring ensures that any suspicious activity is promptly flagged, enabling security teams to respond swiftly and mitigate the risk.
- Enhanced Incident Response:When a security incident occurs, an effective incident response is critical. Endpoint visibility equips security teams with the necessary data to understand the scope and impact of an incident. ThreatResponder goes beyond basic visibility by offering automated response capabilities, allowing it to take predefined actions to contain and remediate threats without manual intervention.
- Identification of Insider Threats:Insider threats, whether intentional or unintentional, pose a significant risk to organizations. Endpoint visibility helps identify unusual user behavior or activities that may indicate insider threats. ThreatResponder’s user behavior analytics play a crucial role in flagging suspicious actions, helping organizations prevent data breaches and unauthorized access.
How ThreatResponder Enhances Endpoint Visibility
As the threat landscape continues to evolve, traditional security measures are often insufficient. You need a more comprehensive approach to cybersecurity that goes beyond perimeter defenses. This is where ThreatResponder by NetSecurity comes into play. ThreatResponder is an all-in-one, unified, cloud-native, machine learning-driven cyber-resilient endpoint security platform.
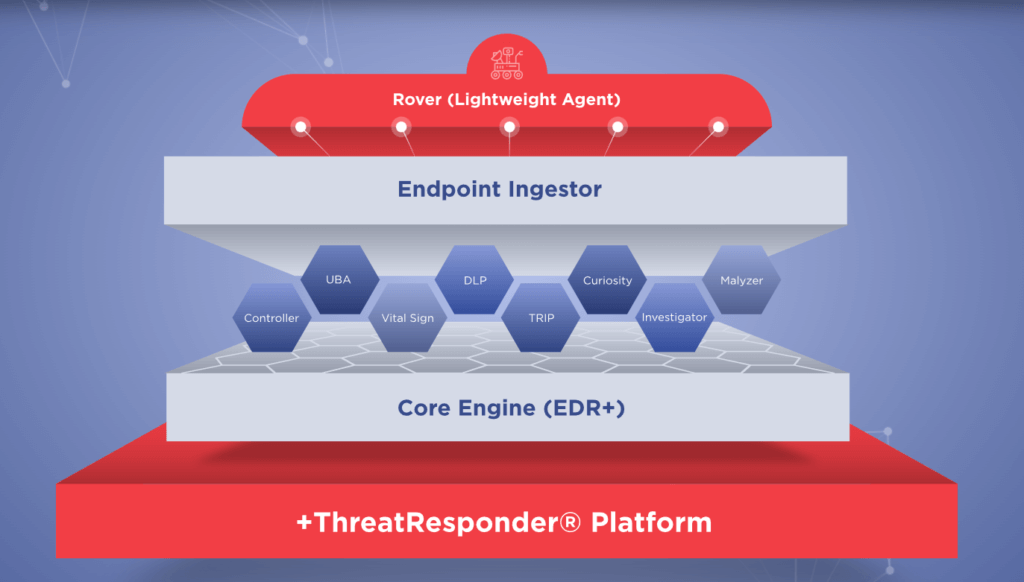
- Behavioral Analytics:ThreatResponder leverages advanced behavioral analytics to establish a baseline of normal behavior on each endpoint. Deviations from this baseline trigger alerts, allowing the system to identify potential threats. This proactive approach ensures that even unknown or zero-day threats can be detected based on their behavior rather than relying solely on signature-based detection.
- Real-Time Monitoring:The real-time monitoring capabilities of ThreatResponder provide security teams with instant insights into endpoint activities. From application launches to network connections, every action is monitored and logged. This level of visibility allows for quick detection of malicious activities and enables timely response to prevent further escalation.
- Integration with Threat Intelligence:Threat intelligence is a crucial component of effective cybersecurity. ThreatResponder integrates seamlessly with threat intelligence feeds, enriching endpoint visibility with up-to-date information about known threats and indicators of compromise (IoCs). This integration ensures that organizations are not only aware of current threats but can also proactively defend against them.
- Automated Response Actions:ThreatResponder doesn’t stop at detection; it takes active measures to respond to threats. With automated response actions, the system can isolate compromised endpoints, block malicious processes, or even roll back changes made by an attacker. This not only enhances the effectiveness of incident response but also reduces the burden on security teams, allowing them to focus on more strategic tasks.
Real-World Scenarios: ThreatResponder in Action
To illustrate the practical benefits of ThreatResponder’s enhanced endpoint visibility, let’s explore a few real-world scenarios where organizations have successfully thwarted cyber threats:
Scenario 1: Zero-Day Malware Detection
An employee unknowingly downloads a seemingly harmless file from an external source. Traditional antivirus solutions fail to detect the threat since it’s a zero-day exploit. However, ThreatResponder’s behavioral analytics identify unusual patterns in the file’s execution, flagging it as a potential threat. The system automatically isolates the affected endpoint, preventing the malware from spreading further.
Scenario 2: Anomalous Network Activity
An endpoint within the corporate network starts exhibiting unusual network behavior, attempting to establish connections with known malicious IP addresses. ThreatResponder’s continuous monitoring of network activities raises an alert, and the system automatically blocks the suspicious connections. The security team investigates the incident, discovering and neutralizing a potential command and control server communication attempt.
Scenario 3: Rapid Response to Ransomware
A ransomware attack is launched, attempting to encrypt files across multiple endpoints. ThreatResponder’s real-time monitoring identifies the encryption process and triggers an automated response to halt the attack. The affected endpoints are isolated, and the encryption is rolled back, preventing any data loss.
Scenario 4: Phishing Email Defense
An employee receives a phishing email containing a malicious attachment. The traditional email security system fails to flag it as malicious. However, when the employee opens the attachment, ThreatResponder’s behavioral analysis detects the suspicious behavior, isolates the affected endpoint, and prevents the execution of the malicious payload. The security team is alerted, and a potential phishing attack is thwarted.
Scenario 5: Credential Compromise Prevention
A user unwittingly falls victim to a credential phishing attack, providing their username and password to a fraudulent website. ThreatResponder’s user behavior analytics notice the abnormal login patterns, such as multiple login attempts from different locations in a short period. The system automatically triggers an alert, revokes the compromised credentials, and advises the user to reset their password, preventing unauthorized access.
Scenario 6: Malicious Process Termination
A malicious process attempts to exploit a vulnerability in an outdated application on an endpoint. ThreatResponder’s real-time monitoring identifies the suspicious behavior, and the system automatically terminates the malicious process before it can execute its payload. The endpoint is isolated to prevent further exploitation, and the security team receives an immediate notification, allowing them to investigate and patch the vulnerability.
Scenario 7: Fileless Malware Detection
A sophisticated fileless malware variant attempts to execute malicious code in the memory of an endpoint, bypassing traditional signature-based detection. ThreatResponder’s behavioral analytics recognize the anomalous behavior associated with fileless attacks, triggering an alert. The system responds by isolating the affected endpoint, preventing the malware from spreading and causing any damage.
Try ThreatResponder for Free!
Are you ready to take the next step in defending your organization against cyber threats? Explore ThreatResponder by NetSecurity today and bolster your organization’s cybersecurity defenses.

Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).











