Growing Chinese Threat To U.S. Cyber Security: How to Protect Your Business?
In the ever-expanding realm of cyberspace, a looming shadow has emerged – one that poses an unprecedented challenge to U.S. cybersecurity. Brace yourself for a riveting journey as we peel back the layers and delve into the heart of this growing Chinese threat. From state-sponsored hackers to advanced technological warfare tactics, let’s take an inside look into the very real concerns that keep experts awake at night. Let’s uncover the hidden dangers lurking behind screens and firewalls in our bid to protect America from cyber intrusions like never before!
Chinese Threat to the U.S. and its Impact on Cybersecurity
In recent years, China has emerged as a major threat to the world of cybersecurity. This rise to power has also brought about concerns regarding China’s cyber activities and their impact on international security.
China’s approach to cybersecurity is heavily influenced by its political ideology and national interests. The Chinese government prioritizes maintaining strict control over information flow within its borders, often referred to as the “Great Firewall of China.” This tightly regulated system allows the government to monitor and censor online content that may be deemed politically sensitive or detrimental to national security. However, it is not just domestic surveillance that raises concerns among other nations. China’s state-sponsored hacking activities targeting foreign governments, businesses, and organizations have put them under scrutiny from cybersecurity experts around the world. These attacks range from espionage for economic gain to sabotaging critical infrastructure systems.
Recently, FBI Director Christopher Wray warned of an alarming hacking threat from China. FBI Director Christopher Wray warned about the growing threat of Chinese cyberattacks against U.S. electrical grids and other infrastructure in an appearance Wednesday morning before the House Select Committee on the Chinese Communist Party.
#ICYMI, last week #FBI Director Christopher Wray warned lawmakers the People’s Republic of China has expanded the scope of its cyber activity to target our critical infrastructure. Read more about the threat and about the FBI’s role in combatting it here: https://t.co/3zxNPlr7fb pic.twitter.com/iRpXSRzEOa
— FBI (@FBI) February 6, 2024
In addition, the FBI also expressed concern from a Chinese state-sponsored hacker group called “Volt Typhoon”. Volt Typhoon is identified to be impacting various critical infrastructure organizations across the U.S.
The #FBI and its partners released an additional #CybersecurityAdvisory to help network defenders protect against living off the land (LOTL) techniques, which enable state-sponsored threat actors to camouflage activity with typical network behavior: https://t.co/2btjNOhka6 pic.twitter.com/H4vRNoYQfa
— FBI (@FBI) February 8, 2024
China’s growing military capabilities in cyberspace are also a cause for concern among policymakers in the United States. The country boasts one of the largest armies in terms of personnel dedicated solely to cyber warfare operations. Their focus on developing advanced technologies such as artificial intelligence (AI) and quantum computing only adds more weight to these concerns.
The impact of this growing threat from China extends beyond traditional forms of warfare into cyberspace. As more aspects of our daily lives become intertwined with technology, including financial transactions, communication systems, and critical infrastructure networks –the potential consequences of a successful cyberattack by an adversary like China become increasingly severe.
Furthermore, China’s cyber activities have significant economic implications. The theft of intellectual property and trade secrets through cyber espionage can significantly harm companies’ competitiveness and innovation, both domestically and internationally.
China’s rising threat poses a significant challenge to global security. The country’s aggressive approach towards information control, state-sponsored hacking activities, and military advancements in cyberspace require a thorough understanding and response from the international community.
The current state of U.S. cybersecurity is a topic that has been gaining increasing attention and concern in recent years. With the rise of sophisticated cyber attacks and growing threats from foreign adversaries, it is clear that the United States is facing significant vulnerabilities in cyberspace.
One of the biggest concerns for U.S. cybersecurity is the threat posed by China. According to government officials and cybersecurity experts, Chinese hackers have been responsible for some of the most damaging cyber attacks targeting U.S. companies, government agencies, and critical infrastructure.
Targets of Chinese Cyber Attacks
The Chinese government’s espionage efforts target a wide range of U.S. entities, including:
1. Government Agencies: The Chinese government targets government agencies, including the Department of Defense, Department of State, and intelligence agencies, to obtain sensitive information related to national security, foreign policy, and defense technologies.
2. Defense Contractors: The Chinese government targets defense contractors to obtain classified military technology, blueprints, and defense strategies. This espionage can compromise U.S. capabilities and undermine national security.
3. Private Corporations: The Chinese government also targets private corporations, particularly those involved in advanced technology, to gather trade secrets, intellectual property, and other proprietary information. This espionage can result in the loss of competitive advantage and financial loss for U.S. companies.
4. Research Institutions: Research institutions are of particular interest to the Chinese government, as they often possess valuable scientific and technological information. The Chinese government seeks to exploit this research for its own gain and suppress U.S. innovation.
5. Technology Companies: China is particularly focused on technology companies, infiltrating their networks, stealing valuable source code, and reverse engineering intellectual property. This espionage enables China to develop its own competing technologies and industries.
6. Pharmaceutical Companies: The Chinese government targets pharmaceutical companies, both domestically and internationally, to obtain confidential research data, clinical trial information, and proprietary drug formulas. This espionage threatens U.S. pharmaceutical companies’ intellectual property rights and market dominance.
7. Financial Institutions: Financial institutions are also targeted by the Chinese government to obtain sensitive financial information, including trade secrets, customer data, and transaction records. This espionage can facilitate economic espionage, money laundering, and fraud.
Types of Cyber Attacks By Chinese Threat Actors
There are several types of cyber attacks that have been initiated by China, each with their own unique tactics and targets. In this section, we will delve into some of the most common types of cyber attacks launched by China.
1. Advanced Persistent Threat (APT)
APT attacks are one of the most commonly used methods by China to gain access to sensitive information from U.S. organizations. APTs are sophisticated and targeted attacks that involve using malware or other malicious tools to infiltrate a network and steal valuable data over an extended period of time without being detected. These attacks often require extensive planning and resources, making them difficult to defend against.
2. Distributed Denial-of-Service (DDoS) Attacks
China has also been known to launch DDoS attacks on a large scale against various targets such as government websites or critical infrastructure systems in order to disrupt their operations. These attacks involve flooding a website or server with an overwhelming amount of traffic until it becomes overloaded and crashes, rendering it inaccessible.
3. Spear Phishing
Spear phishing is another tactic commonly used by Chinese hackers to gain access to sensitive information from specific individuals or organizations. This type of attack involves sending personalized emails that appear legitimate in order to trick users into clicking on malicious links or attachments that can infect their system with malware.
4. Espionage
Espionage refers to the theft of confidential information through unauthorized access or surveillance on electronic devices or networks. This type of attack is often carried out by Chinese hackers targeting U.S. government agencies and corporations with advanced technologies like remote access trojans (RATs) or keyloggers to gather sensitive data.
5. Supply Chain Attacks
China has also been known to exploit vulnerabilities in the supply chain of U.S. companies, such as installing compromised hardware or software in products that can be used for cyber espionage or sabotage. These attacks can have serious consequences, as they can affect a large number of organizations and individuals who use these products.
These are just some of the many types of cyber attacks initiated by China that pose a significant threat to U.S. cybersecurity.
How ThreatResponder Enhances Endpoint Visibility and Protects Your Organization From Advanced Cyber Attacks
As the threat landscape continues to evolve, traditional security measures are often insufficient. You need a more comprehensive approach to cybersecurity that goes beyond perimeter defenses. This is where ThreatResponder by NetSecurity comes into play. ThreatResponder is an all-in-one, unified, cloud-native, machine learning-driven cyber-resilient endpoint security platform.
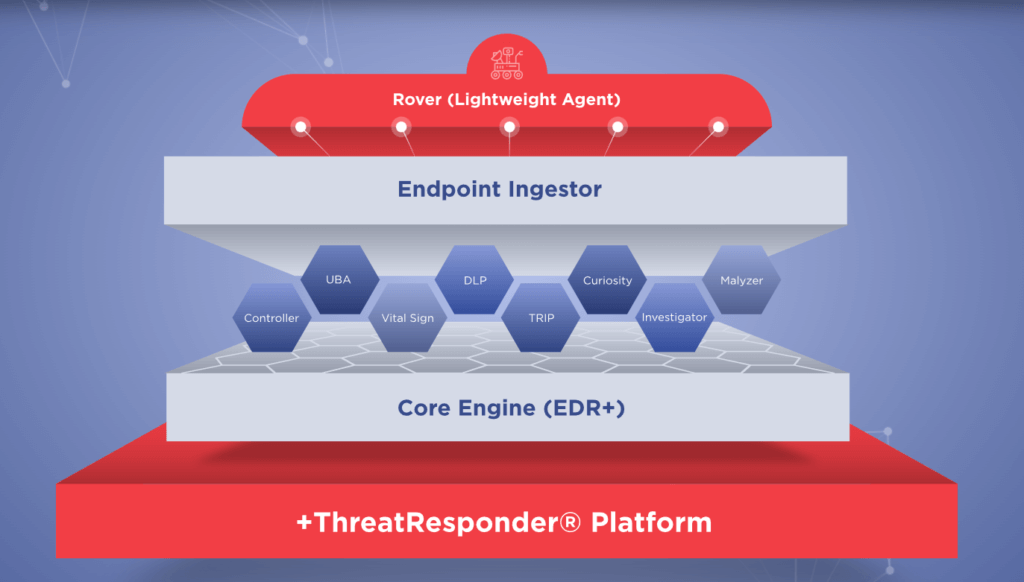
- Behavioral Analytics:ThreatResponder leverages advanced behavioral analytics to establish a baseline of normal behavior on each endpoint. Deviations from this baseline trigger alerts, allowing the system to identify potential threats. This proactive approach ensures that even unknown or zero-day threats can be detected based on their behavior rather than relying solely on signature-based detection.
- Real-Time Monitoring:The real-time monitoring capabilities of ThreatResponder provide security teams with instant insights into endpoint activities. From application launches to network connections, every action is monitored and logged. This level of visibility allows for quick detection of malicious activities and enables timely response to prevent further escalation.
- Integration with Threat Intelligence:Threat intelligence is a crucial component of effective cybersecurity. ThreatResponder integrates seamlessly with threat intelligence feeds, enriching endpoint visibility with up-to-date information about known threats and indicators of compromise (IoCs). This integration ensures that organizations are not only aware of current threats but can also proactively defend against them.
- Automated Response Actions:ThreatResponder doesn’t stop at detection; it takes active measures to respond to threats. With automated response actions, the system can isolate compromised endpoints, block malicious processes, or even roll back changes made by an attacker. This not only enhances the effectiveness of incident response but also reduces the burden on security teams, allowing them to focus on more strategic tasks.
Real-World Scenarios: ThreatResponder in Action
To illustrate the practical benefits of ThreatResponder’s enhanced endpoint visibility, let’s explore a few real-world scenarios where organizations have successfully thwarted cyber threats:
Scenario 1: Zero-Day Malware Detection
An employee unknowingly downloads a seemingly harmless file from an external source. Traditional antivirus solutions fail to detect the threat since it’s a zero-day exploit. However, ThreatResponder’s behavioral analytics identify unusual patterns in the file’s execution, flagging it as a potential threat. The system automatically isolates the affected endpoint, preventing the malware from spreading further.
Scenario 2: Anomalous Network Activity
An endpoint within the corporate network starts exhibiting unusual network behavior, attempting to establish connections with known malicious IP addresses. ThreatResponder’s continuous monitoring of network activities raises an alert, and the system automatically blocks the suspicious connections. The security team investigates the incident, discovering and neutralizing a potential command and control server communication attempt.
Scenario 3: Rapid Response to Ransomware
A ransomware attack is launched, attempting to encrypt files across multiple endpoints. ThreatResponder’s real-time monitoring identifies the encryption process and triggers an automated response to halt the attack. The affected endpoints are isolated, and the encryption is rolled back, preventing any data loss.
Scenario 4: Phishing Email Defense
An employee receives a phishing email containing a malicious attachment. The traditional email security system fails to flag it as malicious. However, when the employee opens the attachment, ThreatResponder’s behavioral analysis detects the suspicious behavior, isolates the affected endpoint, and prevents the execution of the malicious payload. The security team is alerted, and a potential phishing attack is thwarted.
Scenario 5: Credential Compromise Prevention
A user unwittingly falls victim to a credential phishing attack, providing their username and password to a fraudulent website. ThreatResponder’s user behavior analytics notice the abnormal login patterns, such as multiple login attempts from different locations in a short period. The system automatically triggers an alert, revokes the compromised credentials, and advises the user to reset their password, preventing unauthorized access.
Scenario 6: Malicious Process Termination
A malicious process attempts to exploit a vulnerability in an outdated application on an endpoint. ThreatResponder’s real-time monitoring identifies the suspicious behavior, and the system automatically terminates the malicious process before it can execute its payload. The endpoint is isolated to prevent further exploitation, and the security team receives an immediate notification, allowing them to investigate and patch the vulnerability.
Scenario 7: Fileless Malware Detection
A sophisticated fileless malware variant attempts to execute malicious code in the memory of an endpoint, bypassing traditional signature-based detection. ThreatResponder’s behavioral analytics recognize the anomalous behavior associated with fileless attacks, triggering an alert. The system responds by isolating the affected endpoint, preventing the malware from spreading and causing any damage.
Try ThreatResponder for Free!
Are you ready to take the next step in defending your organization against cyber threats? Explore ThreatResponder by NetSecurity today and bolster your organization’s cybersecurity defenses.

Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).











