Detecting and Preventing Mimikatz with ThreatResponder: An In-Depth Analysis
In the realm of cybersecurity, the landscape is constantly evolving, and with it, the tools and techniques employed by both defenders and attackers. Mimikatz, a powerful post-exploitation tool, has gained notoriety for its ability to extract sensitive information from Windows systems, particularly credentials and authentication tokens. Developed by French security researcher Benjamin Delpy, Mimikatz has become a weapon of choice for attackers seeking unauthorized access to systems, highlighting the critical need for organizations to understand its workings, detect its presence, and implement effective preventive measures.
What is Mimikatz?
Mimikatz is an open-source tool designed to gather and exploit credentials on Windows operating systems. Its primary function is to extract plaintext passwords, hashes, PIN codes, and kerberos tickets from memory, making it a potent post-exploitation tool. While its initial intent was to showcase vulnerabilities and educate on security issues, Mimikatz has unfortunately found its way into the arsenal of malicious actors.
Mimikatz CLI
Mimikatz Features
Mimikatz’s functionalities can be broadly categorized into the following:
1. Credential Extraction
Mimikatz is adept at extracting various forms of credentials, including:
- Passwords: Retrieving plaintext passwords stored in memory.
- Hashes: Extracting password hashes for offline cracking.
- PIN Codes: Capturing PIN codes used for authentication.
- Kerberos Tickets: Stealing Kerberos tickets to impersonate users.
2. Pass-the-Ticket Attacks
Mimikatz can manipulate Kerberos tickets, allowing attackers to move laterally within a network without needing the actual user’s password. This is known as a “pass-the-ticket” attack, where a compromised ticket-granting ticket (TGT) is used for unauthorized access.
3. Overpass-the-Hash Attacks
In addition to traditional pass-the-hash attacks, Mimikatz introduced the concept of “overpass-the-hash,” which involves injecting malicious code into the LSASS (Local Security Authority Subsystem Service) process to intercept password hashes in real-time.
4. Golden Ticket Attacks
Mimikatz enables the creation of forged Kerberos tickets known as “Golden Tickets.” Attackers can use these tickets to impersonate any user and gain persistent access to a network.
5. DCSync Attacks
Mimikatz can perform DCSync attacks to simulate a Domain Controller (DC) replication request, fetching sensitive account information, including NTLM hashes, without directly interacting with the DC.
How Mimikatz Works
Understanding Mimikatz’s operation involves delving into its interaction with the Windows authentication system and memory structures.
1. Hooking and Patching
Mimikatz relies on hooking and patching techniques to manipulate the LSASS process. LSASS is responsible for enforcing security policies on a Windows system, and it stores credentials in memory for authentication purposes.
Mimikatz injects its code into the LSASS process, allowing it to intercept and extract credentials as they are processed.
2. Credential Extraction
Once injected, Mimikatz scans the memory space of LSASS to locate and extract credentials. It can decrypt or obtain plaintext passwords, hashes, and other sensitive information directly from memory.
3. Token Manipulation
Mimikatz manipulates access tokens and Kerberos tickets to facilitate lateral movement within a network. This includes pass-the-ticket attacks, overpass-the-hash attacks, and the creation of Golden Tickets.
4. DCSync
For DCSync attacks, Mimikatz simulates a DC replication request, tricking the targeted system into providing sensitive account information as if it were a legitimate Domain Controller.
How Threat Actors Exploit Mimikatz
Mimikatz’s capabilities make it a favorite among malicious actors for a variety of attacks:
1. Credential Theft and Unauthorized Access
Attackers use Mimikatz to steal user credentials, granting them unauthorized access to systems and sensitive data. This can lead to data breaches, financial losses, and reputational damage.
2. Lateral Movement
Mimikatz allows attackers to move laterally within a network, escalating privileges and compromising additional systems. This can lead to widespread infiltration and control over critical infrastructure.
3. Persistence
By creating Golden Tickets and other forged authentication tokens, attackers can establish persistent access to a network, evading detection and maintaining control over compromised systems.
4. Espionage and Data Exfiltration
The information extracted by Mimikatz can be used for industrial espionage or sold on the dark web. Additionally, attackers can exfiltrate sensitive data, causing significant harm to organizations.
Detecting and Preventing Mimikatz Execution
ThreatResponder is an all-in-one cloud-native cyber-resilient endpoint platform designed to detect and prevent the execution of sophisticated malware, including Mimikatz. Its comprehensive threat intelligence and behavior-based analysis empower organizations to proactively identify and respond to potential security incidents. Utilizing such advanced protection mechanisms can significantly enhance the detection capabilities against Mimikatz and other advanced cyber threats.
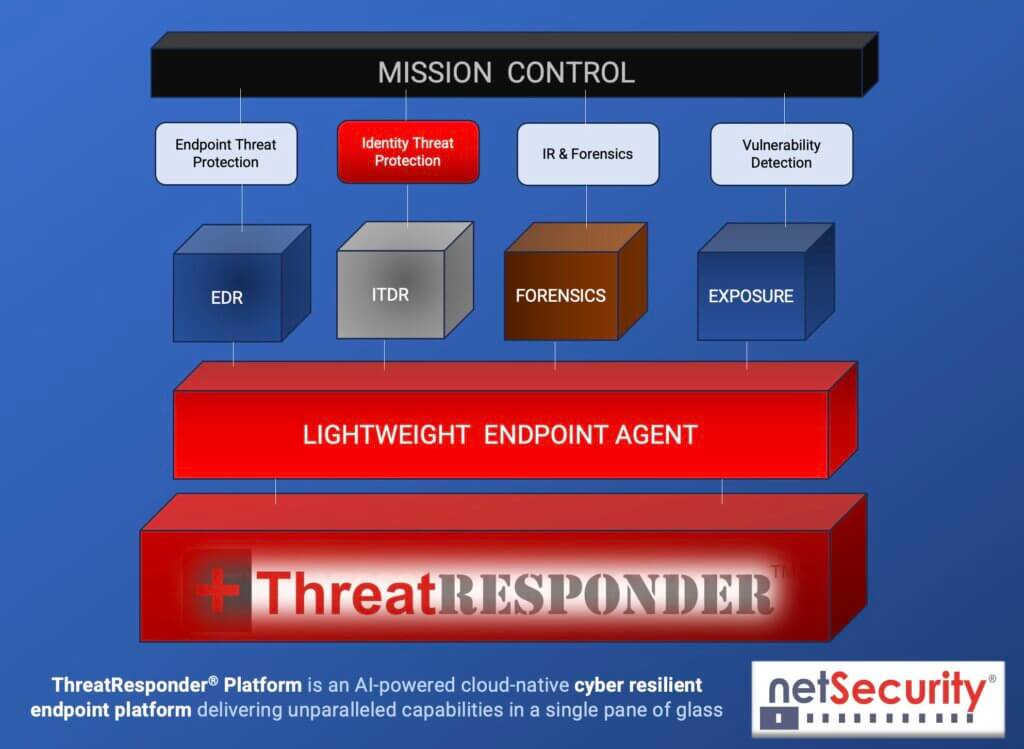
NetSecurity’s ThreatResponder include behavior-based detection mechanisms that can help identify and block Mimikatz execution attempts in your environment. It is designed to provide cybersecurity teams with the necessary tools and insights to defend their organizations effectively. ThreatResponder’s cloud-native architecture ensures rapid and effective response to emerging threats, providing organizations with a robust defense against advanced cyber threats.
Try ThreatResponder for Free!
Are you ready to take the next step in defending your organization against cyber threats? Explore ThreatResponder by NetSecurity today and bolster your organization’s cybersecurity defenses.

Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).