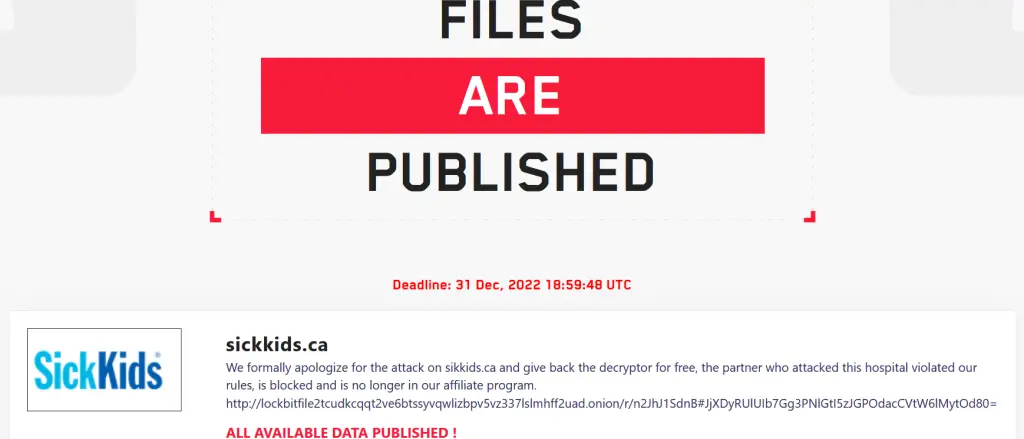
How to Identify the Motive Behind Your Cyber Threat Adversary?
In today’s digital age, the threat of cyber attacks is ever-present, and it is crucial to be able to identify the motives behind these attacks. Understanding the motivations of cyber adversaries can be the key to effectively protecting your systems and data. In this article, we will discuss the different types of adversaries, their motives, and how to identify the motives behind cyber threats. We will also explore how NetSecurity’s...