LockBit Ransomware Group Formally Apologized For The Attack On The SickKids Pediatric Hospital
LockBit ransomware gang has apologized for its attack on the SickKids Pediatric Hospital which is a Toronto based hospital for Sick Children and released a decryptor for free.
The group’s members are prohibited from attacking healthcare organizations under its role. According to its policy, encrypting systems of organizations where damage may cause death is prohibited.
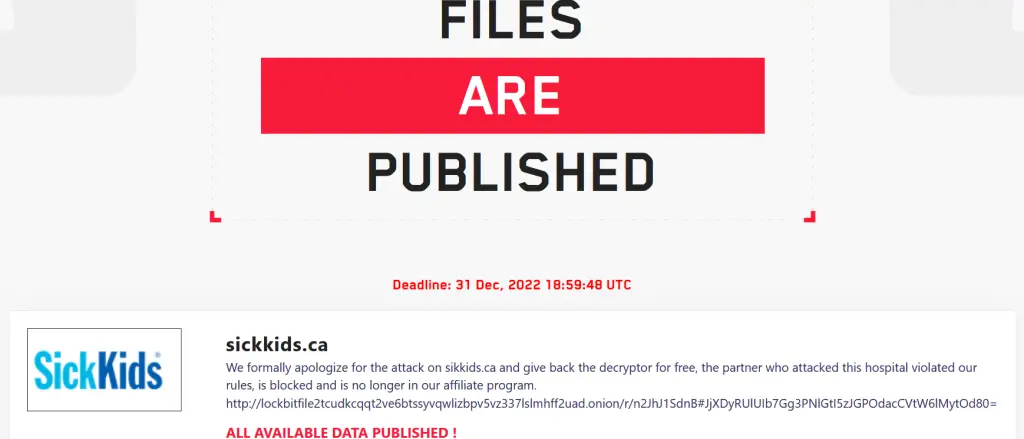
According to the gang, one of its partners had attacked SickKids violating its rules, so it blocked the affiliate.
“We formally apologize for the attack on sikkids.ca and give back the decryptor for free, the partner who attacked this hospital violated our rules, is blocked and is no longer in our affiliate program.” reads the message published by Lockbit on its Tor leak site.

Formal Apology from LockBit Ransomware Gang

Decryptor Shared for Free
History:
SickKids is a teaching and research hospital in Toronto that focuses on providing healthcare to sick children. On December 18th, the hospital suffered a ransomware attack that impacted internal and corporate systems, hospital phone lines, and the website. While the attack only encrypted a few systems, SickKids stated that the incident caused delays in receiving lab and imaging results and resulted in longer patient wait times. On December 29th, SickKids announced that it had restored 50% of its priority systems, including those causing diagnostic or treatment delays.
LockBit’s Background:
The LockBit operation runs as a Ransomware-as-a-Service, where the operators maintain the encryptors and websites, and the operation’s affiliates, or members, breach victims’ networks, steal data, and encrypt devices. As part of this arrangement, the LockBit operators keep approximately 20% of all ransom payments and the rest goes to the affiliate.
While the ransomware operation allows its affiliates to encrypt pharmaceutical companies, dentists, and plastic surgeons, it prohibits its affiliates from encrypting “medical institutions” where attacks could lead to death.
“It is forbidden to encrypt institutions where damage to the files could lead to death, such as cardiology centers, neurosurgical departments, maternity hospitals and the like, that is, those institutions where surgical procedures on high-tech equipment using computers may be performed,” explains the ransomware operation’s policies.
The stealing of data from any medical institution is allowed per the policies.
According to the ransomware gang, as one of its affiliates encrypted the hospital’s devices, they were removed from the operation, and a decryptor was offered for free.
However, this does not explain why LockBit did not provide a decryptor sooner, with patient care being impacted and SickKids working to restore operations since the 18th.
Furthermore, LockBit has a history of encrypting hospitals and not providing encryptors, as was seen in its attack against the Center Hospitalier Sud Francilien (CHSF) in France, where a $10 million ransom was demanded, and patient data eventually leaked.
In addition, Health Sector Cybersecurity Coordination Center has released several warnings regarding the increasing threat from LockBit to the health sector.
How to Prevent Ransomware Attacks on Your Networks
ThreatResponder can also help your cyber security analysts and incident responders to investigate and detect cyber security threats more quickly and effectively. ThreatResponder, with its cloud-based machine learning threat detection engine and its diverse capabilities, can help your team detect the most advanced cyber threats, including APTs, zero-day attacks, and ransomware attacks. It can also help automate incident response actions across millions of endpoints, making it easy, fast, and hassle-free. Want to try our ThreatResponder, cutting-edge Endpoint Detection & Response (EDR), and ThreatResponder FORENSICS, the Swiss knife for forensic investigators in action? Click on the below button to request a free demo of our NetSecurity’s ThreatResponder platform.
Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).