How to Protect Against Cyber Threats: The Modern Way
Current Threat Landscape
Cyber threats are on the rise. As the world becomes more interconnected, the threat of cyber attacks looms larger. Businesses and individuals alike are at risk of being targeted by cyber criminals. Every day, new methods of attacks are discovered and old ones are improved. This makes it difficult for businesses and individuals alike to protect themselves.
What is Cyber Threat Hunting?
The good news is that there are steps you can take to protect yourself. One of those steps is cyber threat hunting.
Cyber threat hunting is the pro-active searching for signs of potential cyber attacks. It’s a preventative measure that can help you identify threats before they have a chance to do damage. Cyber threat hunting is an active cyber defence activity. It is “the process of proactively and iteratively searching through networks to detect and isolate advanced threats that evade existing security solutions.” This is in contrast to traditional threat management measures, such as firewalls, intrusion detection systems (IDS), malware sandbox (computer security) and SIEM systems, which typically involve an investigation of evidence-based data after there has been a warning of a potential threat. Most companies already have comprehensive endpoint security solutions with automated detection in place. Threat hunting works in addition to these and adds advanced technologies to find anomalies, unusual patterns, and other traces of attackers that shouldn’t be in systems and files.
Different Methods of Cyber Threat Hunting
There are a few different methods of cyber threat hunting.
- One is to manually comb through logs and data to look for suspicious activity. This can be time-consuming, but it’s often worth it to catch something before it becomes a problem.
- Another method is to use specialized software to automate the process. This can help you speed up the process and free up your time for other tasks.
Prerequisites for Threat Hunting
Regardless of the method you use, there are a few things you should keep in mind when you’re threat hunting.
- First, you need to have a good understanding of what normal activity looks like on your network. This will help you identify abnormal activity more easily.
- Second, you need to be patient. Cyber criminals are often very good at hiding their tracks, so it can take some time to find the evidence you’re looking for.
- Third, you need to be thorough. A single missed piece of evidence could be all it takes for a cyber criminal to succeed.
Cyber threat hunting can be a valuable tool in the fight against cybercrime. By taking the time to pro-actively search for signs of potential attacks, you can help keep your business or organization safe. In order for threat hunt to be effective, threat hunting requires a combination of people, process, and technology. New cloud-native endpoint protection platform (EPP)s that leverage big data analytics can capture and analyze large volumes of unfiltered endpoint data, while behavioural analytics and artificial intelligence can provide extensive, high-speed visibility into malicious behaviour that seem normal on the outset.
ThreatResponder – To The Rescue
NetSecurity’s ThreatResponder is an advanced all-in-one endpoint security platform that not only allows you to detect threats in real-time, but also allows you to identify hidden threats by performing cyber threat hunting. It is a modern endpoint protection solution that leverage the latest technologies, such as machine learning, AI, and cloud computing, to provide effective and efficient security for individual devices. Following are some features that ThreatResponder offer you to keep your organization safe from cyber threats:
- Telemetry and Visibility: The most important part of any threat hunting solution is the data. In order to hunt for unknown threats, you need complete visibility into all of your data. This means data from all of your assets, including endpoints, networks, and cloud environments.ThreatResponder’s light weight agent allows you a 360 degree visibility on your assets and data 24×7.
- Threat Intelligence Focused: A good threat hunting solution will also have to leverage data from external sources, such as threat intelligence feeds, in order to give you the most complete picture possible. ThreatResponder is AI and machine learning based cloud-native all-in-one endpoint security platform that leverages threat intel feeds from various sources for effective and efficient detection of most advanced cyber threats.
- Investigation: Another important feature of a good threat hunting solution is the ability to quickly pivot and investigate. This means that when you find an IOC, you should be able to quickly query other data sets to see if there are any related events. This might include looking at endpoint data to see if there are any suspicious processes running or looking at network data to see if there is any unusual activity. NetSecurity’s ThreatResponder’s powerful threat hunting module allows you to search for IOCs and threats across 1000’s of endpoints simultaneous and in fraction of time. This module is a Swiss knife to the cyber threat hunters.
- Automation: Finally, a good threat hunting solution will include some form of automation. This could be something as simple as automatically opening a ticket when an IOC is found or it could be more sophisticated, such as automatically quarantining an endpoint that appears to be compromised. And with ThreatResponder, you can not only detect, hunt, quarantine cyber threats, but also isolate the compromised endpoint and perform automated and comprehensive forensic investigations on any number of endpoints simultaneously.
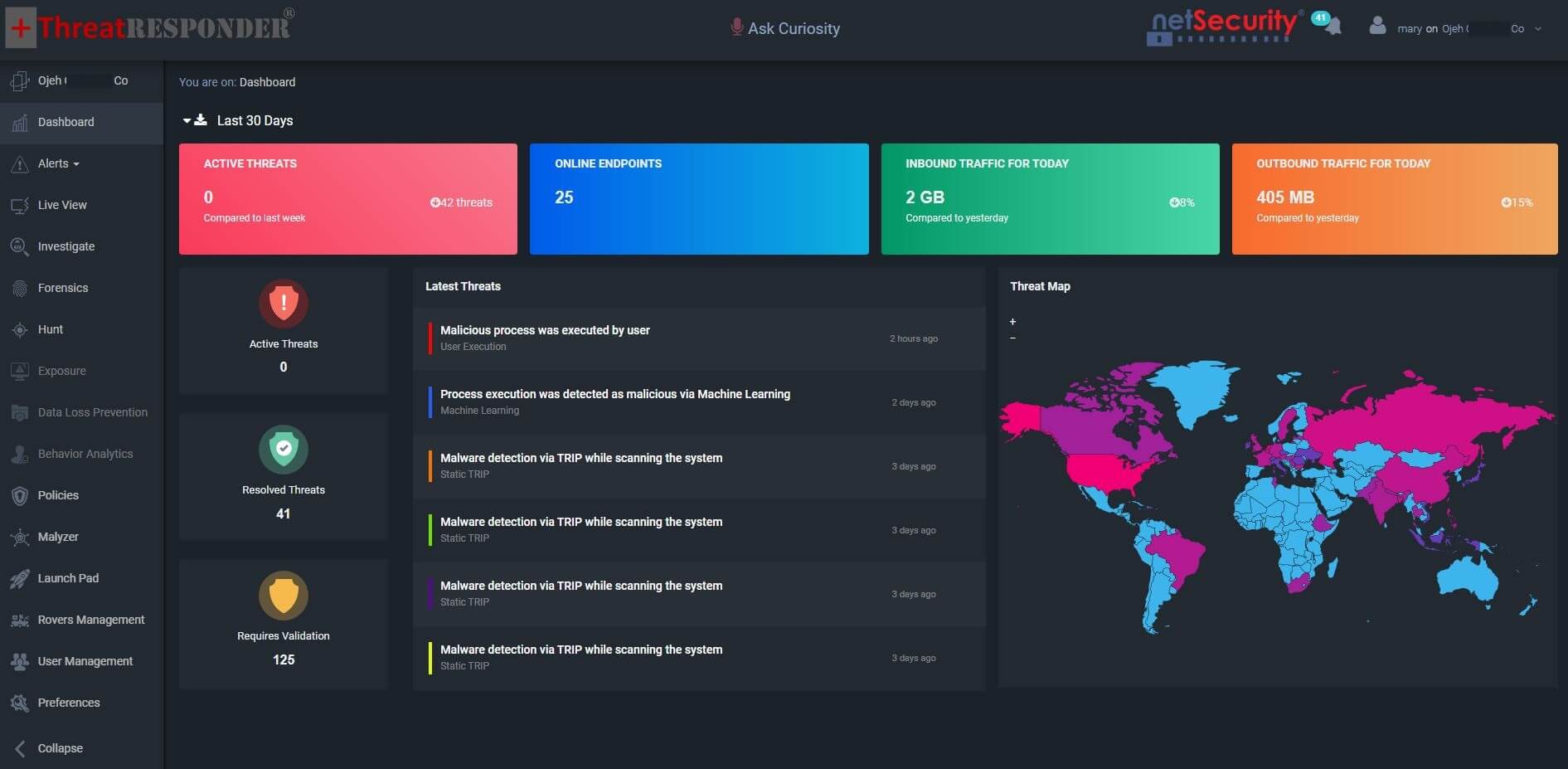
ThreatResponder can also help your cyber security analysts and incident responders to investigate and detect cyber security threats more quickly and effectively. ThreatResponder, with its cloud-based machine learning threat detection engine and its diverse capabilities, can help your team detect the most advanced cyber threats, including APTs, zero-day attacks, and ransomware attacks. It can also help automate incident response actions across millions of endpoints, making it easy, fast, and hassle-free. Want to try our ThreatResponder, cutting-edge Endpoint Detection & Response (EDR), and ThreatResponder FORENSICS, the Swiss knife for forensic investigators in action? Click on the below button to request a free demo of our NetSecurity’s ThreatResponder platform.
Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).










