Detecting and Neutralizing Cuba Ransomware Attack Using NetSecurity’s ThreatResponder
Cuba Ransomware is a highly sophisticated and dangerous piece of malware that has been used in targeted attacks against a wide range of organizations and individuals. It is believed to be developed by a Russian-based cybercrime group, and it is known for its ability to infiltrate and encrypt systems, making it nearly impossible for victims to regain access to their data without paying a ransom. In December 2022, CISA and FBI released a joint advisory on Cuba ransomware as a part of their #StopRansomware initiative.
In this report, we will provide a detailed analysis of the Cuba Ransomware, including its technical capabilities, its methods of distribution, and the steps that organizations can take to protect themselves from this threat. We will also provide a list of indicators of compromise (IOCs) that can be used to identify and prevent future attacks.
Technical Analysis
The Cuba Ransomware is a variant of the REvil (Sodinokibi) ransomware family, which is known for its advanced capabilities and its ability to cause significant damage to infected systems. It is typically distributed through phishing emails or via exploit kits that take advantage of vulnerabilities in software or operating systems.
Once the malware has been downloaded onto a system, it will begin to encrypt the victim’s files using a strong encryption algorithm, such as AES-256. It will then display a ransom demand on the victim’s screen, instructing them to pay a certain amount of money in exchange for the decryption key.
One of the key features of the Cuba Ransomware is its ability to evade detection by security software. It uses a variety of techniques to evade antivirus programs and other security measures, including the use of code obfuscation, anti-debugging techniques, and the injection of malicious code into legitimate processes.
The Cuba Ransomware is also known for its ability to spread quickly within a network. It can propagate itself via remote desktop protocol (RDP) connections and through the use of network shares. This allows it to quickly infect multiple systems within an organization, making it especially difficult to contain and remove.
Methods of Distribution
The Cuba Ransomware is typically distributed through phishing emails that contain malicious attachments or links. These emails are designed to appear legitimate and often contain urgent or threatening language in an attempt to persuade the victim to open the attachment or click on the link.
The emails may contain a variety of different types of attachments, including Word documents, PDFs, or Excel spreadsheets. When the victim opens the attachment, the malware is downloaded and installed onto their system.
Another method of distribution for the Cuba Ransomware is through the use of exploit kits. These kits take advantage of vulnerabilities in software or operating systems and can be delivered through a variety of means, including malicious ads or compromised websites.
Cuba Ransomware Ransom Note

Cuba Ransomware Leak Site in Dark Web

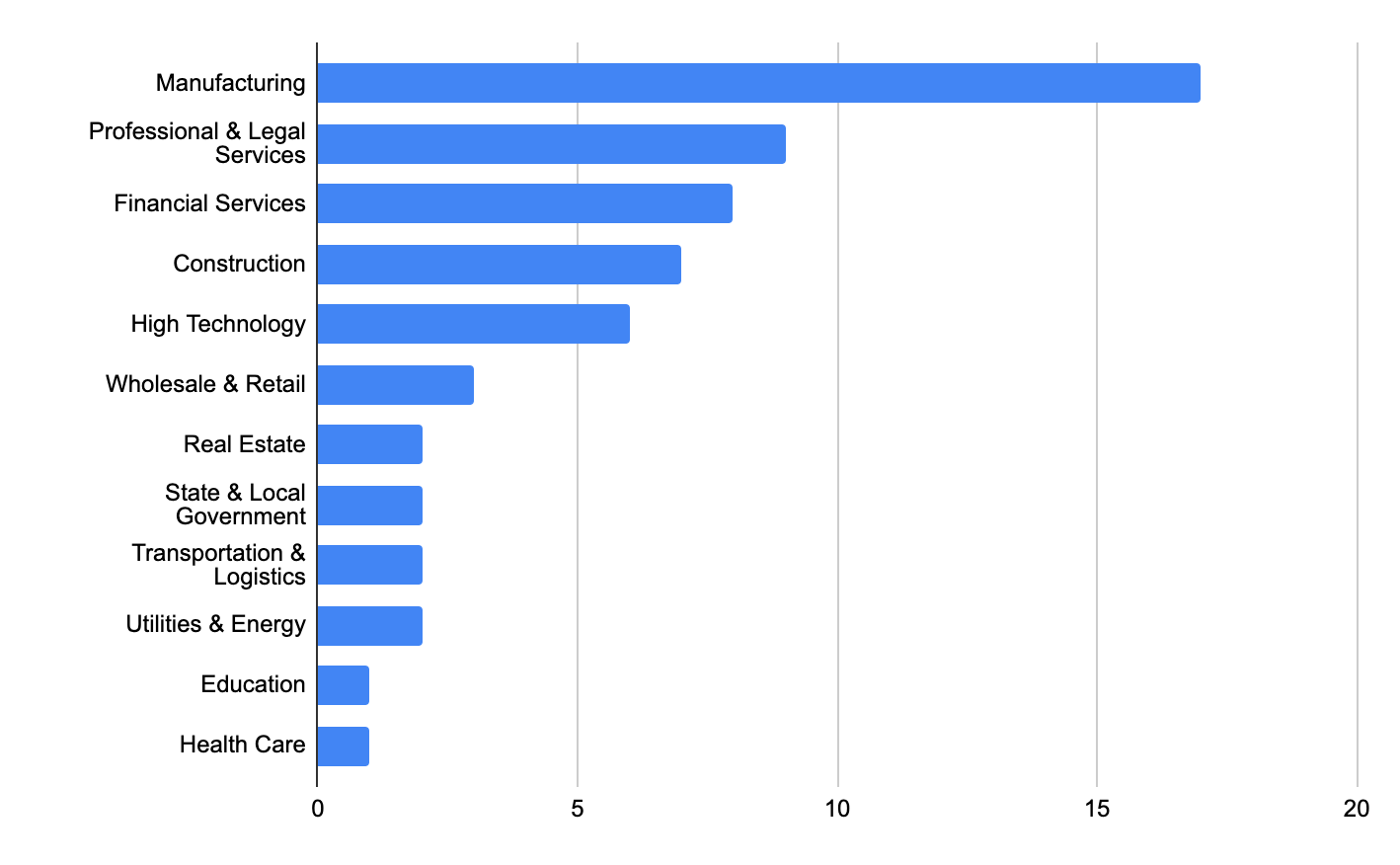
Cuba Ransomware Victims – Source Palo Alto
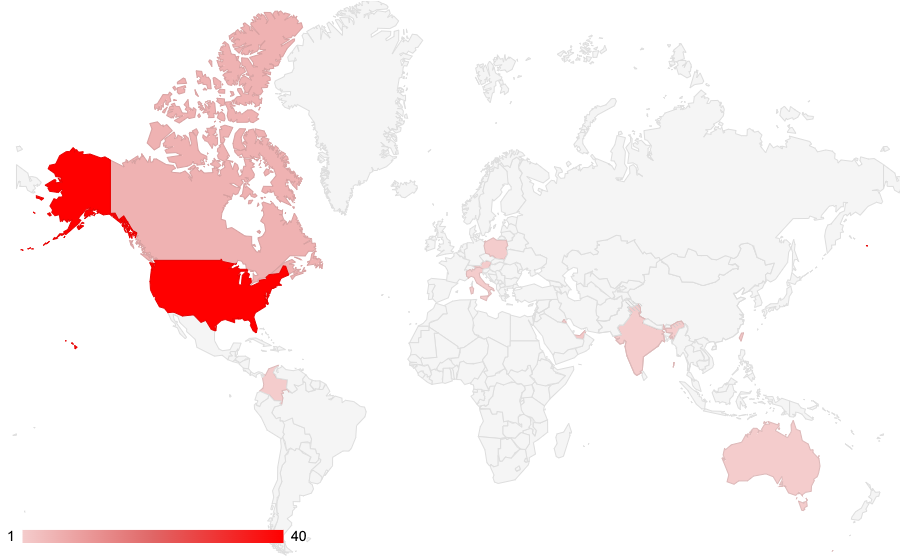
Geographic distributions of organizations targeted by Cuba Ransomware – Source PaloAlto
Protection and Prevention
There are several steps that organizations can take to protect themselves from the Cuba Ransomware and other similar threats. These include:
- Implementing strong security measures: This includes installing and maintaining up-to-date antivirus software and firewall protection, as well as implementing proper password management practices.
- Training employees on cybersecurity best practices: This includes educating employees on the importance of not opening suspicious emails or clicking on unknown links, and teaching them how to recognize and report potential threats.
- Regularly patching and updating systems: It is important to keep all software and operating systems up to date with the latest patches and updates to reduce the risk of vulnerabilities being exploited.
- Backing up important data: Regularly backing up important data can help ensure that it is not lost in the event of a ransomware attack. It is also important to store backups in a separate, secure location.
How To Know If You’re Infected?
There are several indicators that organizations can look for to detect and prevent future attacks by the Cuba Ransomware. Some of these include:
- Suspicious emails: Look for emails with urgent or threatening language, or emails that contain attachments or links that you were not expecting to receive.
- Network activity: Monitor network activity for signs of unauthorized access or unusual patterns of activity that could indicate the presence of malware.
- File encryption: If you notice that files on your system are being encrypted, this could be a sign of a ransomware attack.
- Ransom demands: If you receive a ransom demand on your screen, it is likely that your system has been infected with the Cuba Ransomware.
- Malicious processes: Keep an eye out for any suspicious or unknown processes running on your system, as these could be indicators of malware activity.
Cuba Ransomware Indicators of Compromise (IOCs)
Driver Dropper:
07905de4b4be02665e280a56678c7de67652aee318487a44055700396d37ecd0
af6561ad848aa1ba53c62a323de230b18cfd30d8795d4af36bf1ce6c28e3fd4e
24e018c8614c70c940c3b5fa8783cb2f67cb13f08112430a4d10013e0a324eaa
ZeroLogon Hacktool:
ab5a3bbad1c4298bc287d0ac8c27790d68608393822da2365556ba99d52c5dfb
6866e82d0f6f6d8cf5a43d02ad523f377bb0b374d644d2f536ec7ec18fdaf576
3febf726ffb4f4a4186571d05359d2851e52d5612c5818b2b167160d367f722c
3a8b7c1fe9bd9451c0a51e4122605efc98e7e4e13ed117139a13e4749e211ed0
36bc32becf287402bf0e9c918de22d886a74c501a33aa08dcb9be2f222fa6e24
1450f7c85bfec4f5ba97bcec4249ae234158a0bf9a63310e3801a00d30d9abcc
Cuba Ransomware:
0a3517d8d382a0a45334009f71e48114d395a22483b01f171f2c3d4a9cfdbfbf
0eff3e8fd31f553c45ab82cc5d88d0105626d0597afa5897e78ee5a7e34f71b3
Privilege Escalation Tool:
a4665231bad14a2ac9f2e20a6385e1477c299d97768048cb3e9df6b45ae54eb8
KerberCache Hacktool:
cfe7b462a8224b2fbf2b246f05973662bdabc2c4e8f4728c9a1b977fac010c15
ROMCOM RAT:
B5978cf7d0c275d09bedf09f07667e139ad7fed8f9e47742e08c914c5cf44a53
324ccd4bf70a66cc14b1c3746162b908a688b2b124ad9db029e5bd42197cfe99
Infrastructure:
CombinedResidency[.]org
optasko[.]com
For additional IOCs related to Cuba Ransomware are here.
How to Detect & Remediate Cuba Ransomware Attack on your Network?
Cyber security threats and ransomware attacks are increasing at a tremendous pace. It is extremely difficult for cyber security analysts and incident responders to investigate and detect cyber security threats using conventional tools and techniques. NetSecurity’s ThreatResponder, with its cloud-based machine learning threat detection engine and its diverse capabilities, can help your team detect the most advanced cyber threats, including APTs, zero-day attacks, and ransomware attacks. It can also help automate incident response actions across millions of endpoints, making it easy, fast, and hassle-free.
Want to try our ThreatResponder, cutting-edge Endpoint Detection & Response (EDR), and ThreatResponder FORENSICS, the Swiss knife for forensic investigators in action? Click on the below button to request a free demo of our NetSecurity’s ThreatResponder platform.
Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).