Top 10 Challenges Redefining the CISO’s Role in 2024
The role of a Chief Information Security Officer (CISO) has evolved dramatically in recent years, reflecting the dynamic nature of cybersecurity threats and technological advancements. As we navigate through 2024, the challenges confronting CISOs have become increasingly complex, demanding a holistic and adaptive approach to safeguarding organizational assets. In this context, understanding the multifaceted challenges is crucial to appreciating the scope and intensity of the responsibilities placed on CISOs.
A CISO’s Life – 2023 Global Chief Information Security Officer Survey:
examines both organizational structure and compensation for this critical enterprise leadership role.
Heidrick & Struggles, a premier market research and leadership advisory firm released 2023 Global Chief Information Security Officer (CISO) Survey report that compiled organizational and compensation data from a survey fielded in early 2023 of 262 CISOs around the world. Most carried the title of chief information security officer, but respondents also included chief security officers and senior information security executives. Among the data included in the report are organizational data from respondents in the United States, Europe, and Asia Pacific, and compensation data from respondents in the United States, Europe, and Australia.
According to the report, “Forty percent of CISOs reported that their company does not have a succession plan for the role; 13% said their company isn’t in the process of developing one.” In addition, Heidrick & Struggles’ research shows that the addition of board members with cybersecurity skills remains low as well. As a result of new Securities and Exchange Commission (SEC) guidance, public companies may soon be obliged to disclose which members of their board have cybersecurity experience, elevating their position even further.
CISO’s Challenges in 2024:
- Sophisticated Cyber Threats: The cybersecurity threat landscape continues to escalate in sophistication and diversity. Threat actors leverage advanced techniques, including AI-driven attacks, ransomware, and zero-day exploits. These sophisticated threats demand continuous monitoring, threat intelligence gathering, and adaptive defense mechanisms to thwart potential breaches.
- Evolving Social Engineering Attacks: Cyber attackers are increasingly leveraging sophisticated social engineering tactics to exploit human vulnerabilities within organizations. Phishing, vishing, and pretexting attacks target employees, aiming to manipulate them into divulging sensitive information or granting unauthorized access. CISOs face the challenge of implementing comprehensive training programs and awareness campaigns to fortify their organization’s human firewall against these evolving social engineering threats.
- Remote Work Challenges: The widespread adoption of remote work has expanded the attack surface for cyber threats. CISOs must ensure that remote workers adhere to stringent security protocols and that appropriate safeguards are in place to protect sensitive data accessed outside secure office environments. Balancing convenience with security remains a constant challenge.
- Regulatory Compliance: Compliance with an evolving landscape of data protection regulations such as GDPR, HIPAA, and CCPA poses a significant challenge. CISOs must navigate complex legal frameworks, ensuring their organization adheres to these regulations to avoid severe financial penalties and legal repercussions.
- Skills Gap in Cybersecurity: The shortage of skilled cybersecurity professionals remains a persistent challenge. CISOs struggle to recruit and retain top talent capable of combating sophisticated cyber threats. This scarcity impedes the building of robust security teams, creating vulnerabilities within organizations.
- Cloud Security Concerns: The migration of infrastructure and services to the cloud necessitates robust cloud security measures. CISOs face challenges in ensuring the security of cloud-based environments, managing shared responsibilities with cloud service providers, and mitigating potential risks associated with cloud adoption.
- Budget Constraints: Despite the critical importance of cybersecurity, organizations often face budget limitations. CISOs must effectively allocate resources while justifying cybersecurity investments amid competing organizational priorities, often needing to do more with limited resources.
- Rapid Technological Changes: Emerging technologies, such as AI, quantum computing, and 5G, introduce both opportunities and vulnerabilities. CISOs need to stay abreast of technological advancements, understand their security implications, and proactively implement measures to mitigate associated risks.
- Vendor Risk Management: Organizations rely on numerous third-party vendors and suppliers, increasing the risk of supply chain attacks. CISOs face the challenge of managing and mitigating risks associated with these external partners, ensuring their security practices align with the organization’s standards.
- Board and Executive-Level Engagement: Communicating complex cybersecurity risks effectively to non-technical stakeholders, such as the board and executives, remains a significant challenge. CISOs must articulate the importance of cybersecurity investments in business terms, garnering support and resources for robust security strategies.
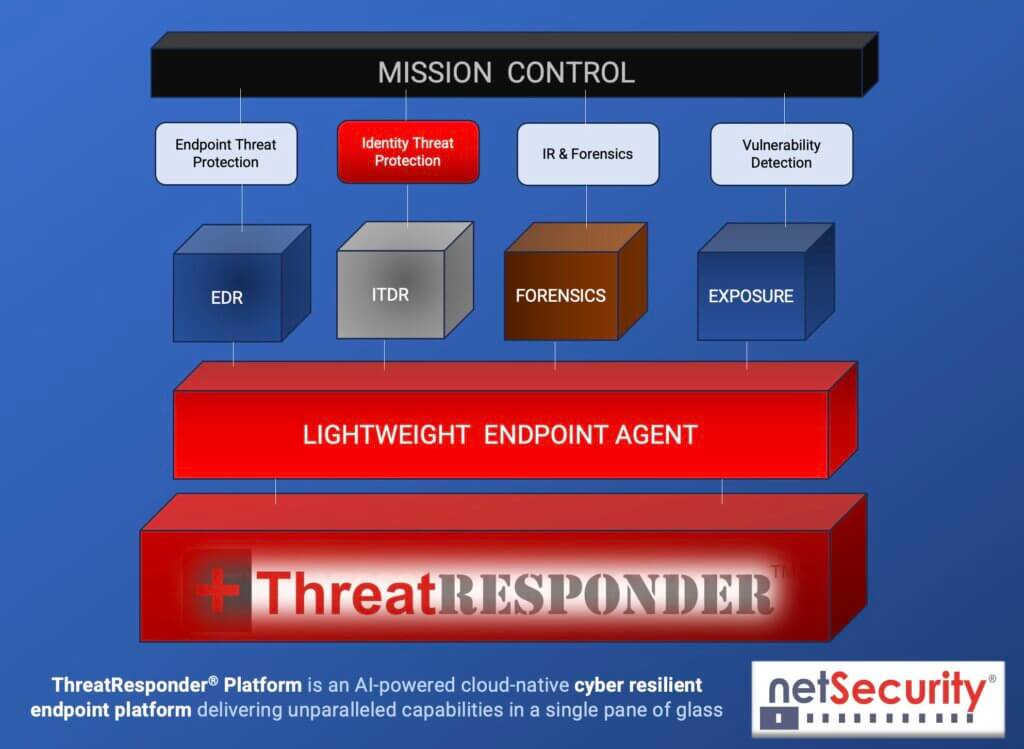
NetSecurity’s ThreatResponder – CISO’s Best Friend
As the threat landscape continues to evolve, traditional security measures are often insufficient. As a CISO, you need a more comprehensive approach to cybersecurity that goes beyond perimeter defenses. This is where ThreatResponder by NetSecurity comes into play. NetSecurity’s ThreatResponder is a game-changer and the CISO’s ultimate ally in combating the evolving cyber menace. This AI-powered unified cloud-native cyber-resilient endpoint platform redefines cybersecurity, offering unmatched capabilities within a single, intuitive interface. ThreatResponder is a strategic imperative in the arsenal of every forward-thinking CISO, providing an edge in an ever-escalating cyber arms race.
In an era where adaptability and resilience are paramount, ThreatResponder stands as the beacon of protection, empowering CISOs to proactively defend their organization’s assets. Embrace the future of cybersecurity with ThreatResponder by NetSecurity – your CISO’s best friend in navigating the complexities of the digital frontier.
Try ThreatResponder for Free
Want to try our ThreatResponder, cutting-edge Endpoint Detection & Response (EDR), and ThreatResponder FORENSICS, the Swiss knife for forensic investigators in action? Click on the below button to request a free demo of our NetSecurity’s ThreatResponder platform.
Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).











