Integrate Mitre Att&CK into Your Incident Response with ThreatResponder
Have you ever wondered how cybersecurity professionals stay one step ahead of the ever-evolving threats that loom over our digital landscape? In a world where malicious actors constantly refine their tactics, staying ahead is not just a challenge; it’s a necessity. NetSecurity’s ThreatResponder, an all-encompassing cloud-native cyber-resilient endpoint platform, has upped the ante in the battle against cyber threats. In this article, we delve into the formidable world of MITRE ATT&CK and its integration into ThreatResponder, deciphering the profound impact it holds for security analysts, incident responders, and forensic investigators.
Understanding MITRE ATT&CK
Before we explore the seamless integration of MITRE ATT&CK into ThreatResponder, let’s establish a foundational understanding of what MITRE ATT&CK is and why it holds immense significance in the realm of cybersecurity.
MITRE ATT&CK, which stands for Adversarial Tactics, Techniques, and Common Knowledge, is a comprehensive knowledge base that maps the actions of threat actors throughout the cyber kill chain. This matrix provides a standardized framework for understanding the tactics and techniques employed by adversaries, making it an invaluable resource for security professionals.
The MITRE ATT&CK matrix is structured into columns representing tactics and rows representing techniques. Tactics encompass the overarching goals of threat actors, such as initial access, execution, persistence, privilege escalation, defense evasion, credential access, discovery, lateral movement, collection, exfiltration, and impact. Techniques, on the other hand, detail the specific methods used to achieve these tactics.
Why MITRE ATT&CK Matters
MITRE ATT&CK serves as a universal language for cybersecurity professionals, fostering a shared understanding of adversary behavior. Here’s why it holds paramount importance:
- Enhanced Threat Intelligence: MITRE ATT&CK provides a comprehensive taxonomy of threat actor behaviors, enabling organizations to better understand the tactics and techniques employed by adversaries. This enhanced threat intelligence is crucial for proactive defense and response strategies.
- Improved Incident Response: By aligning with the MITRE ATT&CK framework, incident responders gain a structured approach to analyzing and mitigating threats. This not only accelerates response times but also ensures a more effective and targeted remediation process.
- Unified Communication: MITRE ATT&CK offers a standardized vocabulary for communicating about cyber threats. This ensures clarity and precision in discussions among security professionals, enabling a more cohesive and collaborative response to incidents.
MITRE ATT&CK in ThreatResponder
Now that we’ve understood the significance of MITRE ATT&CK, let’s explore how its seamless integration into ThreatResponder amplifies the capabilities of security analysts, incident responders, and DFIR investigators.
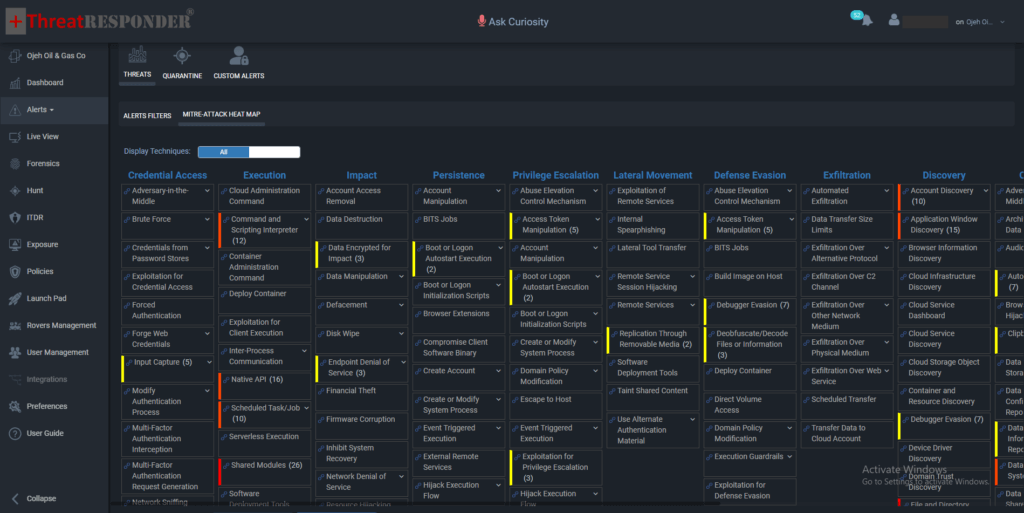
1. Unveiling Potential Threats with MITRE ATT&CK Matrix in Alerts
Imagine a scenario where a malicious code is executed, and it manages to bypass initial security measures or when ThreatResponder is implemented in Detection-only mode. In such cases, the MITRE ATT&CK Techniques matrix becomes a beacon of insight. Within ThreatResponder Alerts, this matrix reveals potential techniques that a threat actor could have leveraged during an incident.
The matrix is strategically designed to align with the MITRE ATT&CK framework, displaying tactics and techniques relevant to the observed threat. Security analysts can quickly identify the nature of the attack and understand the adversary’s objectives by referring to the matrix within ThreatResponder Alerts.
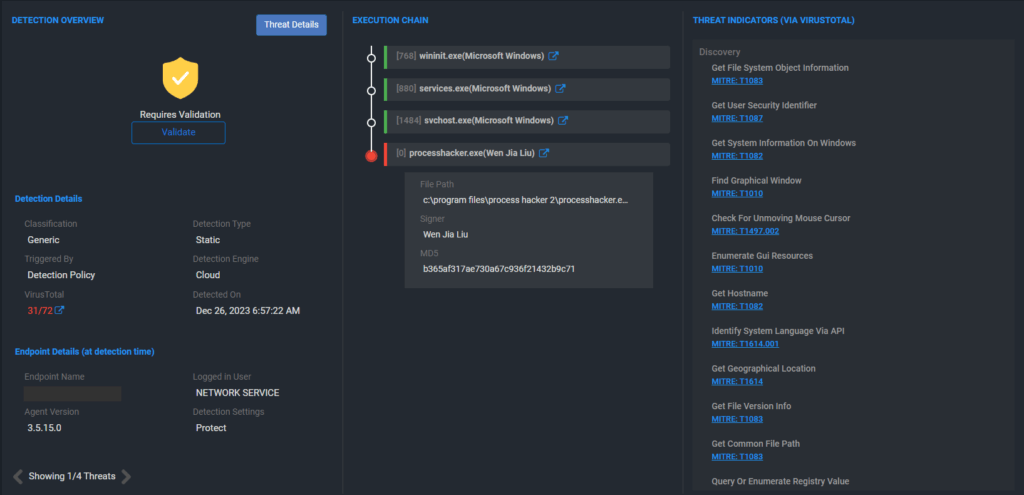
2. Filtering Threats with Precision
One of the standout features of MITRE ATT&CK integration in ThreatResponder Alerts is the ability to apply filters based on specific MITRE ATT&CK techniques. This functionality allows security professionals to focus their investigations on threats that align with a particular technique, streamlining the analysis process.
By clicking on an item in the matrix, users can instantly filter ThreatResponder Alerts to display only those incidents that involve the selected MITRE ATT&CK technique. This level of granularity ensures that security analysts can hone in on the most relevant information, saving valuable time and resources during an investigation.
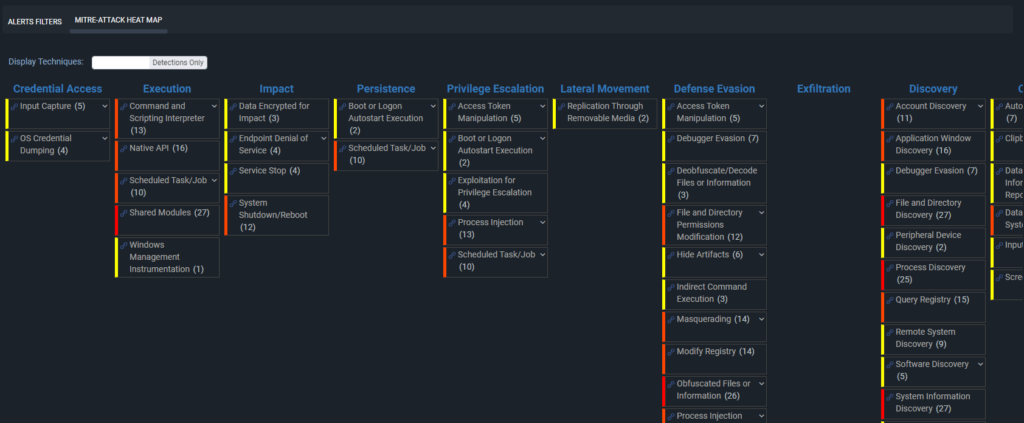
3. Strategic Decision-Making with MITRE ATT&CK Context
In the world of cybersecurity, context is key. MITRE ATT&CK integration in ThreatResponder Alerts enriches incident data with contextual information about the tactics and techniques employed by threat actors. This additional layer of insight equips security professionals with a deeper understanding of the incident, enabling more informed decision-making.
Security incident investigators can leverage the MITRE ATT&CK context to prioritize and respond to incidents based on the severity of the tactics and techniques involved. This strategic approach ensures that resources are allocated efficiently, addressing the most critical threats first.
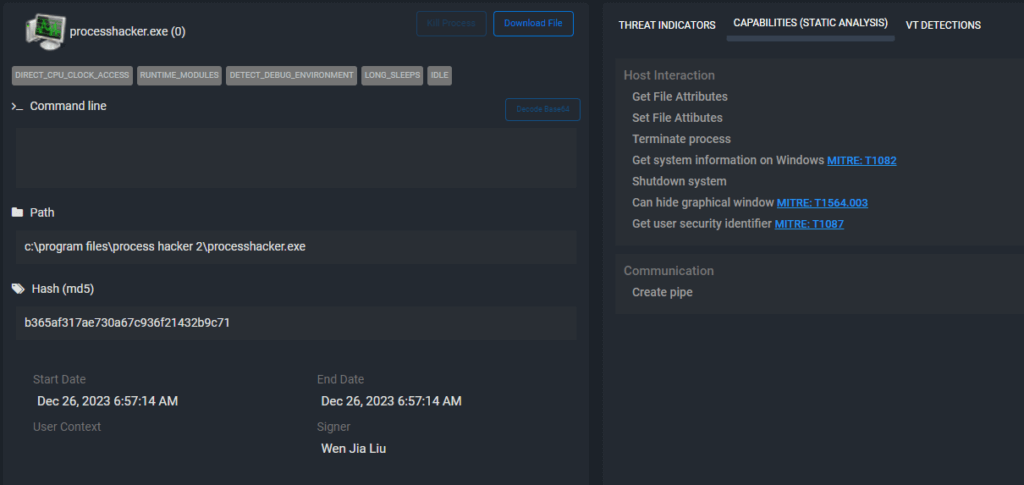
4. Training and Skill Development Opportunities
MITRE ATT&CK integration in ThreatResponder not only enhances incident response but also serves as a valuable training tool. Security teams can use real-world incidents recorded in ThreatResponder Alerts to simulate and practice responses based on MITRE ATT&CK techniques.
This hands-on approach to training allows security professionals to refine their skills and deepen their understanding of adversarial behaviors. It also facilitates continuous improvement in security postures by identifying areas that may require additional attention or enhancement.
By seamlessly incorporating MITRE ATT&CK into ThreatResponder Alerts, organizations can elevate their incident response capabilities, enhance threat intelligence, and build a more resilient cybersecurity strategy. The ability to quickly identify and filter threats based on MITRE ATT&CK techniques ensures that security teams can focus their efforts where they matter most, ultimately fortifying defenses and safeguarding against evolving cyber threats.
How Can You Safeguard Your Organization in 2024?
As the threat landscape continues to evolve, traditional security measures are often insufficient. You need a more comprehensive approach to cybersecurity that goes beyond perimeter defenses. This is where ThreatResponder by NetSecurity comes into play. ThreatResponder is an all-in-one, unified, cloud-native, machine learning-driven cyber-resilient endpoint security platform.
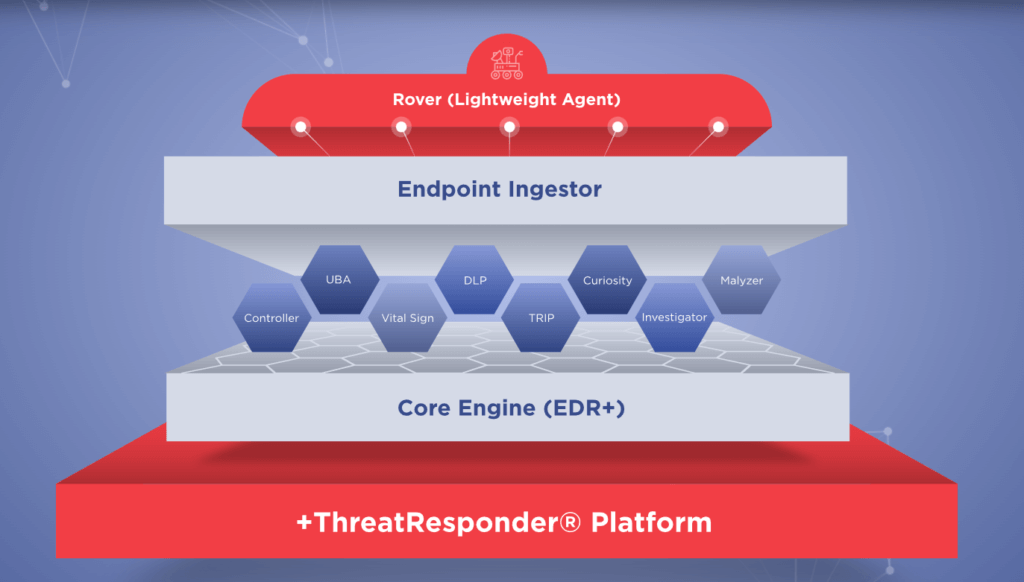
These pillars collectively create a formidable defense system against a wide range of cyber threats. However, in an ever-evolving digital world, there’s always room for improvement and expansion.
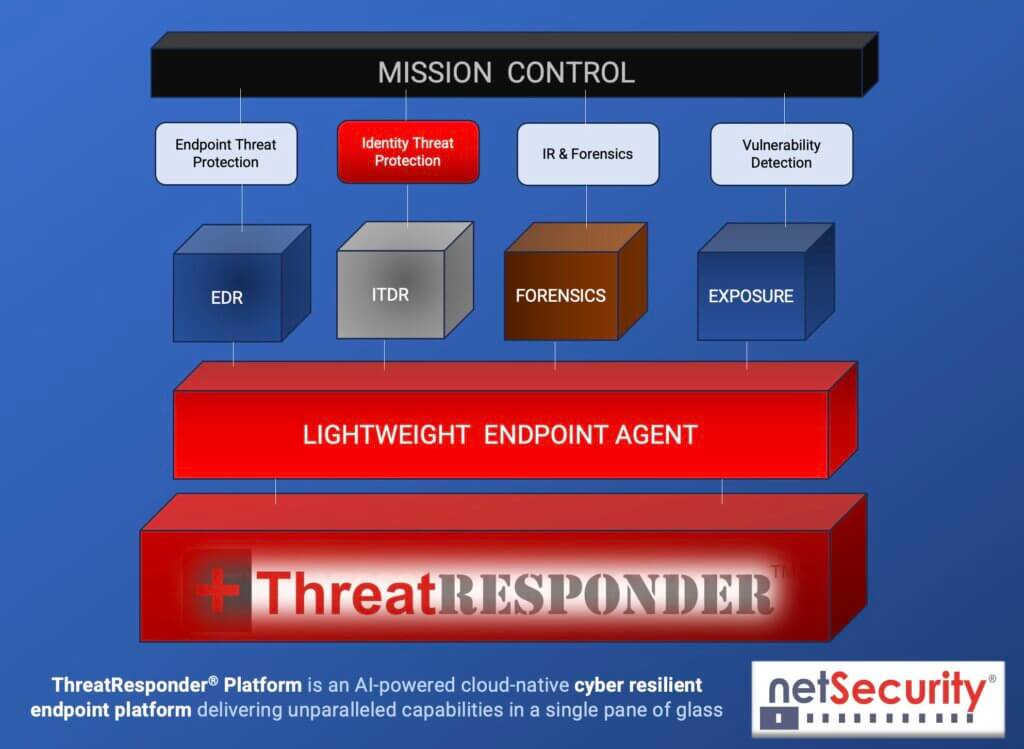
It is designed to provide cybersecurity teams with the necessary tools and insights to defend their organizations effectively. Let’s take a closer look at the core features of ThreatResponder:
Endpoint Detection and Response (EDR)
Endpoint Detection and Response is a critical component of modern cybersecurity. ThreatResponder continuously monitors endpoints (devices and servers) for signs of suspicious activities, such as malware infections or unusual behavior. When a threat is detected, ThreatResponder responds in real-time to mitigate the risk, making it an invaluable asset in threat containment and incident response.
Identity Threat Detection and Response
User identities are a prime target for attackers. ThreatResponder analyzes user behaviors and privileges to identify suspicious activities and potential threats. By understanding user identity and access patterns, it can detect unauthorized access and protect sensitive data from breaches.
Forensics
In the aftermath of a security incident, forensics play a crucial role in understanding the attack and its impact. ThreatResponder provides detailed forensic capabilities, helping CISOs and their teams analyze the scope of an incident, track the attacker’s movements, and collect evidence for potential legal action.
Threat Hunting
Proactive threat hunting is essential for identifying threats before they cause significant damage. ThreatResponder equips CISOs with advanced threat-hunting tools, enabling them to search for hidden threats, vulnerabilities, and indicators of compromise within their organization’s network.
Vulnerability Detection
Identifying and patching vulnerabilities is a fundamental part of cybersecurity. ThreatResponder helps CISOs stay on top of vulnerabilities within their organization’s systems and applications, allowing them to prioritize and address weaknesses before they are exploited by attackers.
Try ThreatResponder for Free!
Are you ready to take the next step in defending your organization against cyber threats? Explore ThreatResponder by NetSecurity today and bolster your organization’s cybersecurity defenses.

Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).











