Unconventional Threats Mandate Unconventional Solutions: How to Improve Security Investigations with ThreatResponder Forensics
Cybersecurity is becoming an increasingly critical concern for organizations worldwide. The frequency and sophistication of cyberattacks continue to increase, leading to the need for more advanced and comprehensive security measures. In this regard, threat detection, prevention, response, analytics, intelligence, investigation, and hunting products have become a vital part of organizations’ security architecture. One such tool is ThreatResponder, an all-in-one cloud-native endpoint threat detection, prevention, response, analytics, intelligence, investigation, and hunting product. ThreatResponder Forensics is an essential component of this tool that helps organizations investigate security incidents and effectively respond to them.
Understanding ThreatResponder Forensics Capabilities:
ThreatResponder Forensics is an advanced capability of the ThreatResponder tool that allows organizations to collect artifacts and categorize evidence from thousands of machines directly from the management console. It can collect versatile information from an endpoint, including a list of processes, registry keys, files, installed applications, startup and scheduled services, etc. Additionally, ThreatResponder Forensics can also provide existing vulnerabilities along with the CVSS score to help analysts understand the threat landscape. The tool can detect any presence of threats that have persisted in the network and provide a detailed timeline and chain of events that can be downloaded as a report. These advanced and unconventional features make ThreatResponder Forensics the best cybersecurity resilience tool and enable effective forensic investigations of security incidents.
ThreatResponder Forensics is also an effective tool for tackling unconventional and unknown malware. The tool’s advanced and unconventional features enable organizations to detect and respond to new and emerging threats quickly. This capability is essential in today’s cybersecurity landscape, where threats are constantly evolving and becoming more sophisticated.
Furthermore, ThreatResponder Forensics provides organizations with a comprehensive understanding of their threat landscape. The tool can provide information on vulnerabilities, threats, and attack vectors, allowing organizations to prioritize their cybersecurity efforts and allocate resources effectively. This capability is particularly important for organizations with limited resources and budgets, as it enables them to focus on the most critical threats and vulnerabilities.
How to Improve Your Security Incident Investigation Capability with ThreatResponder Forensics:
-
Collect Relevant Artifacts
The first step in investigating a security incident is to collect relevant information. This information can include data on the affected endpoints, the type of threat, the extent of the damage, and any other information that may be pertinent to the investigation. ThreatResponder Forensics can collect this information from multiple endpoints simultaneously, making the process faster and more efficient.
-
Analyze the Data
Once you have collected the forensic data, the next step is to analyze the data. ThreatResponder Forensics can categorize the evidence and provide an easy-to-understand summary of the data. The tool can detect any presence of threats that have persisted in the network and provide a detailed timeline with chain of events. ThreatResponder makes the data analytics signifiantly easy and by analyzing the data easily with ThreatResponder Forensics, you can gain a better understanding of the scope of the attack and determine the best course of action to remediate the threat.
-
Identify the Root Cause
The next step in investigating a security incident is to identify the root cause. ThreatResponder Forensics with its advanced machine-learning based theat detection engine can provide detailed and accurate information that can allow analysts to identify the source of the attack, the entry point, and any other relevant details that help determine the root cause of an incident. By identifying the root cause, the cyber security team can prevent similar incidents from occurring in the future and improve your overall cybersecurity posture.
-
Remediate the Threat
Once the threat and root cause are identified, the next step is to remediate the threat. ThreatResponder Forensics can help you quickly remediate the threat or infection from hundrends or thousands of endpoints simultaneously with a click. With the help of ThreatResponder’s threat mitigation capabilities, you can not only kill or quarantine, but can also clean the endpoint to effectively bring back to asset to operations. In addition, as ThreatResponder Forensics also provides the detailed list of vulnerabilites present on the endpoints along with the CVSS scores, these recommendations can prioritize the vulnerabilities patching to improve your overall security posture.
-
Monitor for Future Incidents
In addition, ThreatResponder is well known for its threat monitoring and prevention capabilties. ThreatResponder can provide real-time monitoring and alerting, allowing you to quickly detect and respond to any future threats or cyber attacks. By continuously monitoring for threats and improving your Mean-Time-To-Detect (MTTD) and Mean-Time-To-Respond (MTTR) with ThreatResponder, you can stay one step ahead of cybercriminals and prevent any cyber threats to your organization. The solution is designed to be easy to use, allowing organizations to quickly implement and start using it to prevent cyber attacks.
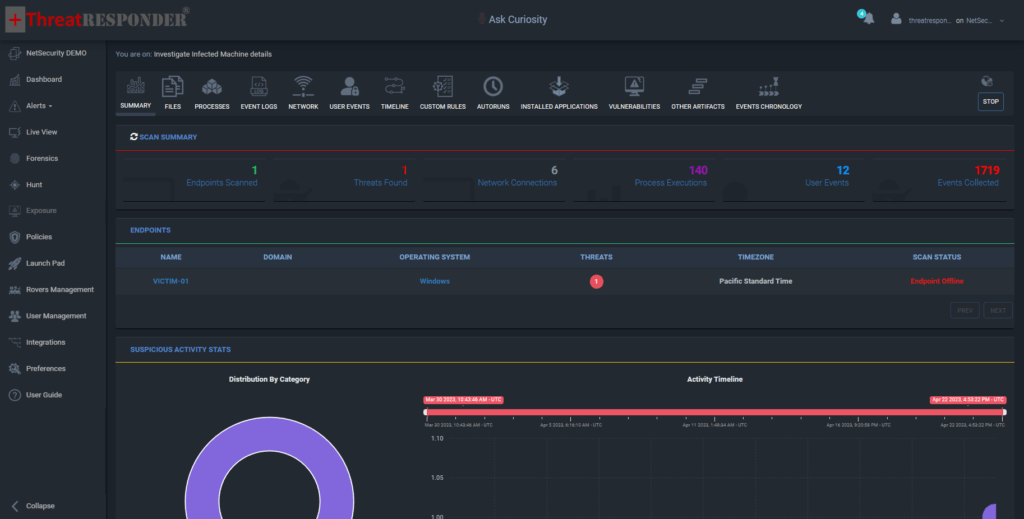
ThreatResponder Forensics
Want to try our ThreatResponder, cutting-edge Endpoint Detection & Response (EDR), and ThreatResponder FORENSICS, the Swiss knife for forensic investigators in action? Click on the below button to request a free demo of our NetSecurity’s ThreatResponder platform.
Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).