Why Your Company Need an Effective DFIR Solution in 2023?
In today’s digital landscape, organizations face an ever-growing threat of cyberattacks. It is not a question of “if” but “when” an organization will encounter a security incident. In such a scenario, having a robust and effective Digital Forensics and Incident Response (DFIR) solution is paramount to promptly identify, investigate, and mitigate security breaches. NetSecurity’s ThreatResponder, with its advanced capabilities and comprehensive features, emerges as the ideal choice for organizations seeking a reliable and efficient DFIR solution.
Collecting Comprehensive Artifacts:
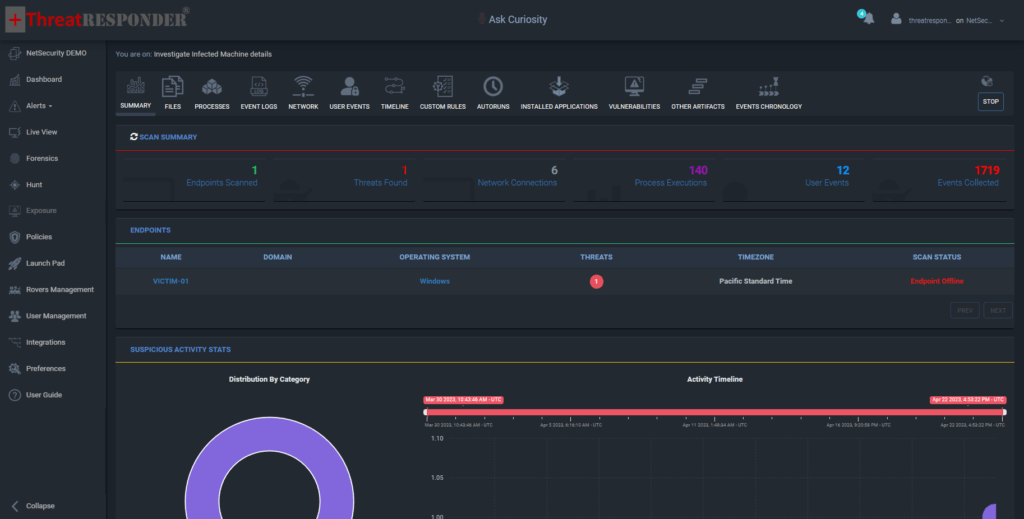
The first step in an effective DFIR process is collecting comprehensive artifacts. ThreatResponder Forensics, an advanced capability of the ThreatResponder tool, allows organizations to collect and categorize evidence from thousands of machines directly from the management console. This feature provides unparalleled convenience and efficiency by eliminating the need for manual collection from each endpoint. By effortlessly gathering versatile information such as processes, registry keys, files, installed applications, startup and scheduled services, ThreatResponder Forensics offers a comprehensive view of the endpoint environment, enabling thorough investigations.
Analyzing Collected Data:
Once the artifacts have been collected, the next crucial step in the DFIR process is analyzing the data to gain actionable insights. ThreatResponder’s intuitive management console provides powerful analysis capabilities, enabling security analysts to delve into the collected data. By examining the information gathered from endpoints, analysts can identify patterns, anomalies, and potential indicators of compromise. This analysis helps understand the extent of the security incident, identify the impacted systems, and prioritize response efforts accordingly. The ability to analyze collected data is vital for effective decision-making during incident response.
Detecting Persistent Threats:
One of the key challenges in modern cybersecurity is identifying threats that persist within the network over an extended period. Traditional security solutions often fail to detect such threats. However, ThreatResponder Forensics fills this critical gap by leveraging advanced detection mechanisms to identify the presence of persistent threats. By continuously monitoring the network and endpoints, the tool highlights any malicious activity that has evaded initial security measures. This capability is essential for organizations as it allows them to effectively respond to threats that may have infiltrated their network, minimizing potential damage and preventing future incidents.
Identifying Existing Vulnerabilities:
In addition to addressing ongoing threats, it is crucial for organizations to proactively identify and mitigate potential vulnerabilities. ThreatResponder Forensics excels in this regard by providing existing vulnerability assessments along with Common Vulnerability Scoring System (CVSS) scores. By leveraging this information, security analysts can gain deep insights into the threat landscape, prioritize remediation efforts, and enhance the overall security posture of the organization. Identifying and patching vulnerabilities before they are exploited by attackers significantly strengthens an organization’s defense against potential breaches.
Identify the Root Cause:
When a security incident occurs, it is essential to identify the root cause to prevent similar incidents from recurring. ThreatResponder Forensics offers advanced capabilities to trace the origins of an attack and determine how it infiltrated the network. By analyzing the collected artifacts, identifying the attack vectors, and understanding the chain of events, security analysts can pinpoint the root cause with accuracy. This knowledge empowers organizations to strengthen their defenses, close security gaps, and implement effective preventive measures. Identifying the root cause is not only critical for incident response but also for ongoing security improvement efforts.
Generating Detailed Forensic Reports:
Detailed and accurate documentation is crucial for effective forensic investigations. ThreatResponder Forensics enables the generation of comprehensive reports that provide a detailed timeline and chain of events. These reports offer deep visibility into the incident, allowing analysts to reconstruct the attack, identify the root cause, and take appropriate remedial actions.
By generating detailed forensic reports, ThreatResponder Forensics expedites incident response efforts, reduces downtime, and strengthens an organization’s overall cybersecurity resilience. These reports serve as a valuable resource for internal investigations, legal proceedings, and regulatory compliance requirements.
Automating Incident Response:
In addition to its robust forensics capabilities, ThreatResponder offers automation features to streamline the incident response process. The tool allows organizations to define and execute automated response actions based on predefined rules and policies. This automation not only accelerates response times but also ensures consistent and standardized actions, minimizing human error and increasing overall efficiency. By automating repetitive tasks, security teams can focus their efforts on critical analysis and decision-making, enabling faster containment and remediation of security incidents.
Enhancing Collaboration and Communication:
Effective DFIR requires seamless collaboration and communication among various stakeholders, including security analysts, IT teams, management, and external parties such as law enforcement or incident response consultants. ThreatResponder provides a centralized platform that facilitates collaboration and information sharing. Through its management console, authorized users can collaborate in real-time, share findings, document actions, and communicate securely. This streamlined collaboration ensures a coordinated response and enables stakeholders to work together efficiently, mitigating the impact of security incidents.
Adapting to Evolving Threat Landscape:
The threat landscape is constantly evolving, with new attack techniques and vulnerabilities emerging regularly. ThreatResponder is designed to adapt to these changes and stay ahead of emerging threats. NetSecurity, the provider of ThreatResponder, invests in continuous research and development to update the tool with the latest threat intelligence, detection mechanisms, and mitigation strategies. Regular software updates and enhancements ensure that ThreatResponder remains at the forefront of the fight against cyber threats, providing organizations with ongoing protection and resilience.
Try ThreatResponder For Free!
ThreatResponder offers a comprehensive range of capabilities to help cybersecurity analysts during computer and Windows forensic investigations. It is essential for DFIR professionals who need to investigate, analyze, and remediate security incidents quickly and efficiently. Its ability to investigate at scale, remotely, and with legally defensible results makes it a valuable asset for any organization that takes cybersecurity seriously. By using ThreatResponder, DFIR professionals can stay ahead of emerging threats, identify and analyze malicious activity, and communicate their findings effectively. With its evidence collecting and analyzing capabilities, and easy-to-use interface, ThreatResponder is an invaluable platform for any cybersecurity analyst looking to conduct forensic investigations in a fast, efficient, and legally defensible way.
Try our ThreatResponder, cutting-edge Endpoint Detection & Response (EDR), and ThreatResponder FORENSICS, the Swiss knife for forensic investigators in action? Click on the below button to request a free demo of our NetSecurity’s ThreatResponder platform.
Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).