Resolving Cybersecurity Incidents and Simplifying Complex Forensic Investigations with NetSecurity’s ThreatResponder
Cybersecurity incidents are becoming more and more common in today’s digital landscape, with the increasing amount of online activities and dependence on technology. These incidents range from hacking and data breaches to ransomware attacks and social engineering scams. Cybersecurity incidents can have devastating effects on individuals, organizations, and even the society as a whole. When cyber attackers gain unauthorized access to sensitive information, they can steal or compromise it, leading to financial losses, reputational damage, and even legal consequences. In addition, cyber incidents can disrupt critical operations and services, causing significant downtime, lost productivity, and revenue. For instance, a ransomware attack on a hospital can prevent access to critical patient data, leading to life-threatening situations. Therefore, it is essential to detect and respond to cybersecurity incidents promptly and effectively to minimize their impact and prevent further damage.
Detecting, analyzing, and resolving these incidents can be a complex and challenging process, especially when it involves multiple systems and devices. In this regard, NetSecurity’s ThreatResponder is a sophisticated tool that helps security analysts perform complex forensic investigations easily without efforts. In this article, we will discuss the importance of solving cybersecurity incidents and the role of NetSecurity’s ThreatResponder in simplifying complex forensic investigations.
The Challenges of Forensic Investigations
When a cybersecurity incident occurs, it is crucial to investigate and determine its root cause and extent. However, this process can be complex and time-consuming, especially when it involves multiple systems, devices, and data sources. For instance, a data breach might require analysis of network traffic, log files, and user activities to identify the attacker and the affected data. Similarly, a malware infection might require analysis of system memory, file system, and registry to identify the malware’s behavior and impact. In addition, the forensic investigation process must follow strict protocols and standards to ensure the evidence is admissible in court if necessary.
To simplify and expedite the forensic investigation process, security analysts need to have access to advanced tools that can help them analyze and correlate data from different sources. In this regard, NetSecurity’s ThreatResponder is a powerful tool that provides security analysts with a comprehensive set of features and capabilities to perform complex forensic investigations easily and efficiently.
How NetSecurity’s ThreatResponder Simplifies Complex Forensic Investigations
NetSecurity’s ThreatResponder is a versatile tool that provides security analysts with a wide range of features and capabilities to detect, analyze, and resolve cybersecurity incidents. Some of the key features of ThreatResponder include:
-
Collect Relevant Artifacts
The first step in investigating a security incident is to collect relevant information. This information can include data on the affected endpoints, the type of threat, the extent of the damage, and any other information that may be pertinent to the investigation. ThreatResponder Forensics can collect this information from multiple endpoints simultaneously, making the process faster and more efficient.
-
Analyze the Data
Once you have collected the forensic data, the next step is to analyze the data. ThreatResponder Forensics can categorize the evidence and provide an easy-to-understand summary of the data. The tool can detect any presence of threats that have persisted in the network and provide a detailed timeline with chain of events. ThreatResponder makes the data analytics signifiantly easy and by analyzing the data easily with ThreatResponder Forensics, you can gain a better understanding of the scope of the attack and determine the best course of action to remediate the threat.
-
Identify the Root Cause
The next step in investigating a security incident is to identify the root cause. ThreatResponder Forensics with its advanced machine-learning based theat detection engine can provide detailed and accurate information that can allow analysts to identify the source of the attack, the entry point, and any other relevant details that help determine the root cause of an incident. By identifying the root cause, the cyber security team can prevent similar incidents from occurring in the future and improve your overall cybersecurity posture.
-
Remediate the Threat
Once the threat and root cause are identified, the next step is to remediate the threat. ThreatResponder Forensics can help you quickly remediate the threat or infection from hundrends or thousands of endpoints simultaneously with a click. With the help of ThreatResponder’s threat mitigation capabilities, you can not only kill or quarantine, but can also clean the endpoint to effectively bring back to asset to operations. In addition, as ThreatResponder Forensics also provides the detailed list of vulnerabilites present on the endpoints along with the CVSS scores, these recommendations can prioritize the vulnerabilities patching to improve your overall security posture.
-
Monitor for Future Incidents
In addition, ThreatResponder is well known for its threat monitoring and prevention capabilties. ThreatResponder can provide real-time monitoring and alerting, allowing you to quickly detect and respond to any future threats or cyber attacks. By continuously monitoring for threats and improving your Mean-Time-To-Detect (MTTD) and Mean-Time-To-Respond (MTTR) with ThreatResponder, you can stay one step ahead of cybercriminals and prevent any cyber threats to your organization. The solution is designed to be easy to use, allowing organizations to quickly implement and start using it to prevent cyber attacks.
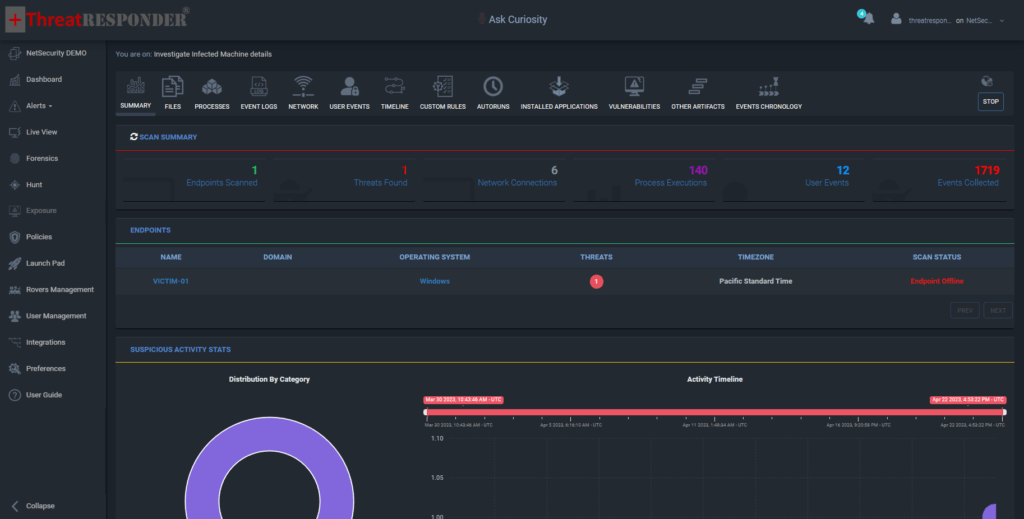
ThreatResponder Forensics
Some Use Cases of NetSecurity’s ThreatResponder Forensics:
NetSecurity’s ThreatResponder has been used successfully in various industries to detect and resolve cybersecurity incidents. Let’s take a look at some of the use cases of ThreatResponder:
- Financial services: The financial services industry is a prime target for cyber attackers due to the sensitive nature of the data they handle. NetSecurity’s ThreatResponder has been used by financial institutions to detect and respond to cyber incidents quickly, ensuring the integrity of their systems and data.
- Healthcare: Healthcare organizations store vast amounts of sensitive patient data, making them a prime target for cyber attackers. ThreatResponder has been used by healthcare organizations to detect and respond to cyber incidents, ensuring patient data remains secure and confidential.
- Manufacturing: Manufacturing companies rely heavily on technology to manage their operations, making them vulnerable to cyber threats. NetSecurity’s ThreatResponder has been used by manufacturing companies to detect and respond to cyber incidents, ensuring their systems and data remain secure.
- Government: Government agencies handle a vast amount of sensitive data, making them a prime target for cyber attackers. ThreatResponder has been used by government agencies to detect and respond to cyber incidents, ensuring the security and confidentiality of the data they handle.
Get Free Trial Access to the Powerful Tool:
Want to try our ThreatResponder, cutting-edge Endpoint Detection & Response (EDR), and ThreatResponder FORENSICS, the Swiss knife for forensic investigators in action? Click on the below button to request a free demo of our NetSecurity’s ThreatResponder platform.
Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).