Top 5 Cyber Security Threats to US Critical Infrastructure in 2023
In today’s interconnected world, critical infrastructure plays a pivotal role in the functioning of any nation. The United States, being a global leader, heavily relies on its critical infrastructure organizations to sustain its economy and ensure national security. However, this interconnectedness also exposes the country to a myriad of cyber threats. In this article, we will explore the top five cyber security threats to US critical infrastructure and understand how you can safeguard your organization from these cyber threats.
1. Ransomware
Ransomware has emerged as a pervasive and damaging threat to the critical infrastructure of the United States, affecting a range of sectors, including financial institutions, healthcare, and educational institutions. Ransomware attacks typically involve encrypting an organization’s data or systems and demanding a ransom for the decryption key.
In recent years, attacks on financial institutions have seen an increase in sophistication, causing substantial financial losses. These attacks not only disrupt services but also undermine the trust that clients have in these institutions. Healthcare facilities have been plagued by ransomware, often resulting in the compromise of patient records and the interruption of critical medical services. Additionally, educational institutions have faced significant challenges, with attacks disrupting virtual learning platforms and exposing sensitive student and faculty data.
2. State-sponsored Disruptive and Destructive Threats
Critical infrastructure sectors such as energy and gas, utilities, and government websites have been targeted by state-sponsored threat groups from countries like China and Russia. These attacks range from disruptions of service to destructive operations that can lead to physical damage or prolonged outages. These threat groups often operate with the backing of their respective governments and pose a significant risk to the nation’s security.
For example, attacks on energy and gas sectors can disrupt the supply of power and essential resources, impacting the daily lives of citizens. Utility companies are also vulnerable targets; a successful attack on these organizations can lead to service outages that can affect entire regions. Attacks on government websites can compromise national security and citizen privacy. The destruction or manipulation of data or services within these organizations can have far-reaching consequences.
3. Third-Party Supply Chain Threats
Third-party supply chain threats are intricate challenges that arise from the interconnected nature of modern supply chains. Cybercriminals often exploit vulnerabilities in third-party entities to gain access to more secure critical infrastructure systems. These threats encompass several aspects, such as zero-day vulnerabilities, third-party suffering from cyberattacks, sensitive information exfiltration, and unauthorized remote desktop access.
Zero-day vulnerabilities are flaws in software or hardware that are unknown to the vendor and, therefore, unpatched. Threat actors can exploit these vulnerabilities through third-party entities to compromise critical infrastructure systems. Additionally, attacks on third-party entities themselves, such as ransomware and disruptive DDoS attacks, can have a ripple effect, disrupting the supply chain and, ultimately, critical infrastructure operations. Furthermore, the exfiltration of sensitive information can lead to data breaches, intellectual property theft, and other damaging consequences.
4. Social Engineering
Social engineering is a versatile and persistent threat that leverages psychological manipulation to trick individuals into divulging sensitive information or performing actions that compromise security. Threat actors use various tactics, such as phishing emails, calling help desks for password resets, SMS phishing (smishing), and QR code phishing to exploit human psychology and gain unauthorized access to systems and data.
Phishing emails are one of the most prevalent forms of social engineering. These emails often impersonate trusted entities, tricking recipients into clicking on malicious links or attachments. Calling help desks for password reset attacks involve impersonating employees or users to gain access to accounts. SMS phishing sends fraudulent text messages that lead recipients to malicious websites or reveal personal information. QR code phishing involves manipulating QR codes to redirect users to malicious sites or download malicious apps.
5. Insider Threats
Insider threats are a significant concern for US critical infrastructure, as they involve individuals with authorized access who intentionally or unintentionally pose risks to the organization’s security. These insiders may be negligent, careless, or intentionally malicious in their actions. Insider threats can encompass a range of activities, including data theft, fraud, espionage, or unintentional errors that compromise security.
Negligent insiders may unknowingly create vulnerabilities, such as failing to follow security protocols, sharing passwords, or clicking on malicious links. Careless insiders may mishandle sensitive data, leading to accidental data breaches. Malicious insiders may intentionally steal data, sabotage systems, or conduct espionage on behalf of external threat actors. All these activities can significantly impact critical infrastructure operations and security.
NetSecurity’s ThreatResponder: An All-In-One Cyber Resilient Endpoint Security Platform
TThreatResponder is an all-in-one, unified, cloud-native, machine learning-driven cyber-resilient endpoint security platform with advanced threat detection, prevention, response, analytics, intelligence, investigation, and hunting capabilities. Once lightweight agents (“Rovers”) are deployed, you gain situational awareness and immediate threat visibility into hundreds and thousands of endpoints, respond to ransomware, nation-state, and insider threats, and neutralize cyber attacks quickly. ThreatResponder® allows investigators to conduct incident response and computer forensics investigation on a remote endpoint.
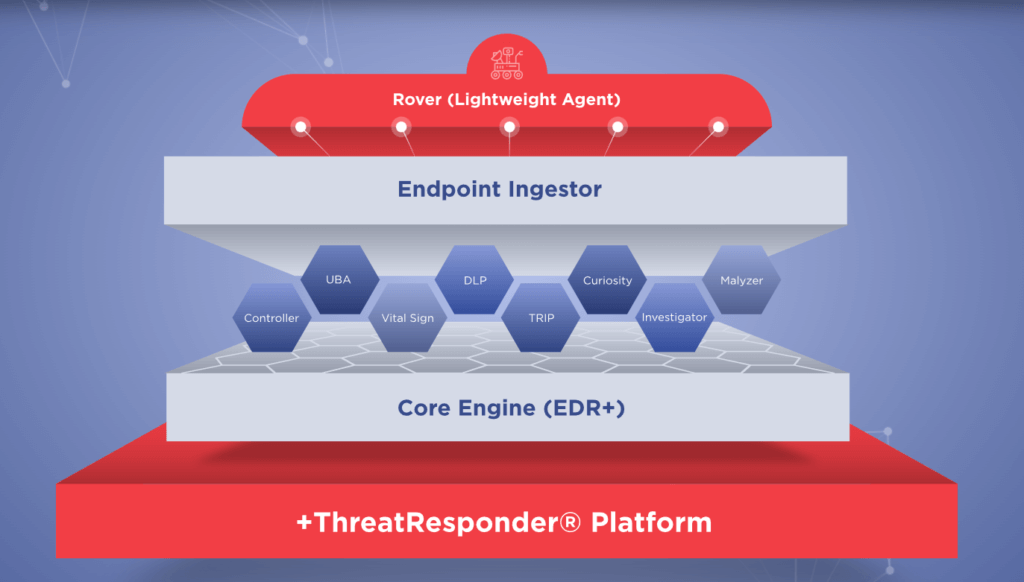
These pillars collectively create a formidable defense system against a wide range of cyber threats. However, in an ever-evolving digital world, there’s always room for improvement and expansion.
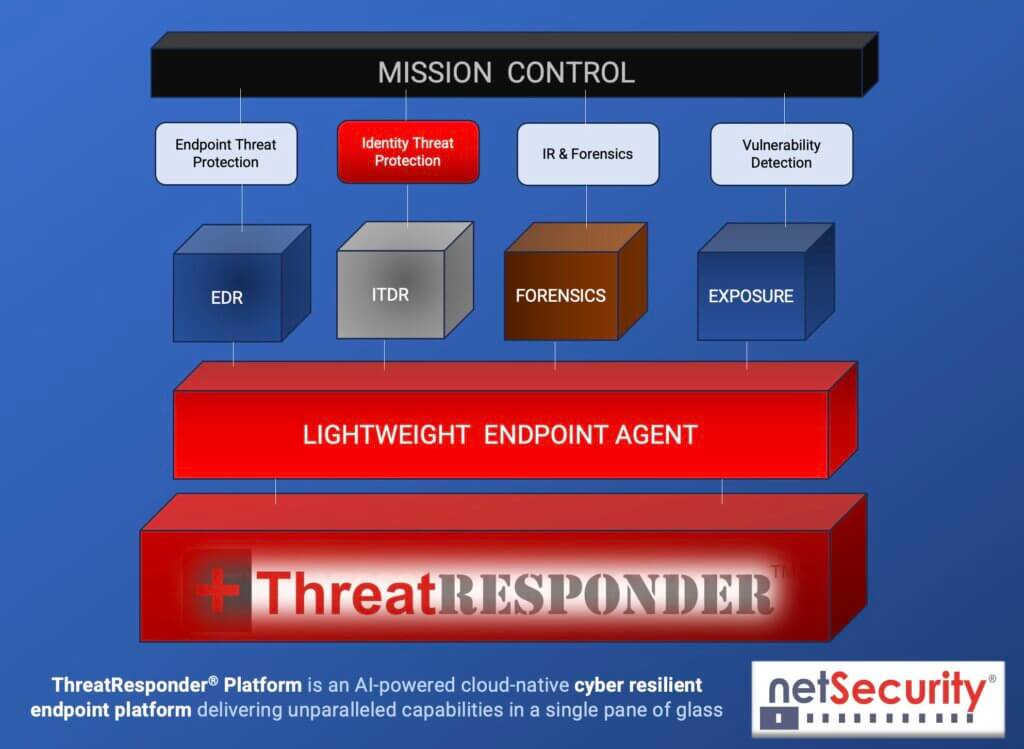
It is designed to provide cybersecurity teams with the necessary tools and insights to defend their organizations effectively. Let’s take a closer look at the core features of ThreatResponder:
Endpoint Detection and Response (EDR)
Endpoint Detection and Response is a critical component of modern cybersecurity. ThreatResponder continuously monitors endpoints (devices and servers) for signs of suspicious activities, such as malware infections or unusual behavior. When a threat is detected, ThreatResponder responds in real-time to mitigate the risk, making it an invaluable asset in threat containment and incident response.
Identity Threat Detection and Response
User identities are a prime target for attackers. ThreatResponder analyzes user behaviors and privileges to identify suspicious activities and potential threats. By understanding user identity and access patterns, it can detect unauthorized access and protect sensitive data from breaches.
Forensics
In the aftermath of a security incident, forensics play a crucial role in understanding the attack and its impact. ThreatResponder provides detailed forensic capabilities, helping CISOs and their teams analyze the scope of an incident, track the attacker’s movements, and collect evidence for potential legal action.
Threat Hunting
Proactive threat hunting is essential for identifying threats before they cause significant damage. ThreatResponder equips CISOs with advanced threat hunting tools, enabling them to search for hidden threats, vulnerabilities, and indicators of compromise within their organization’s network.
Vulnerability Detection
Identifying and patching vulnerabilities is a fundamental part of cybersecurity. ThreatResponder helps CISOs stay on top of vulnerabilities within their organization’s systems and applications, allowing them to prioritize and address weaknesses before they are exploited by attackers.
Why Organizations Need a Unified Platform?
Cybersecurity is a complex field with a multitude of threats and challenges. Managing various security tools and solutions can be a daunting task. This is where the power of integration comes into play.
A unified platform like ThreatResponder streamlines your cybersecurity operations. Instead of juggling multiple tools from different vendors, you have a single, centralized hub for monitoring, responding to incidents, and managing threats. This integration leads to more efficient workflows, reduced operational overhead, and better visibility into your organization’s security posture.
When it comes to cybersecurity, every second counts. A seamlessly integrated platform ensures that information flows in real-time, enabling faster decision-making and response to potential threats. It’s a game-changer in the race against cybercriminals.
With its advanced features and capabilities, ThreatResponder equips organizations to fortify their defenses, respond effectively to incidents, and adapt to emerging threats. By embracing the capabilities of ThreatResponder, organizations can enhance their cyber resilience and ensure a robust security posture in the face of evolving cyber threats.
Try ThreatResponder for Free
Want to try our ThreatResponder, cutting-edge Endpoint Detection & Response (EDR), and ThreatResponder FORENSICS, the Swiss knife for forensic investigators in action? Click on the below button to request a free demo of our NetSecurity’s ThreatResponder platform.

Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).











