How Well Do You Know Your Cyber Threats And Are You Protected?
In today’s digital age, cyber threats have become an ever-present reality for organizations of all sizes. Cyberattacks are growing in frequency and sophistication, posing significant challenges to businesses across the globe. Chief Information Security Officers (CISOs) are at the forefront of the battle against cyber threats, responsible for safeguarding their organization’s critical data, systems, and reputation.
To effectively defend against cyber threats, CISOs require a comprehensive, unified, and advanced cybersecurity solution. In this blog, we’ll explore the evolving landscape of cyber threats and introduce ThreatResponder, a cutting-edge innovation from NetSecurity. ThreatResponder is an all-in-one, unified, cloud-native, machine learning-driven cyber-resilient endpoint security platform designed to equip CISOs and their teams with the tools and knowledge they need to secure their organizations.
Most Common Cyber Threats in 2023
The landscape of cyber threats is constantly evolving, with attackers becoming more sophisticated and innovative. CISOs need to understand the current threat landscape to effectively defend their organizations. Let’s delve into some of the most prominent cyber threats of today.
Ransomware
Ransomware attacks have surged in recent years, causing significant financial and operational damage to businesses. Attackers use ransomware to encrypt an organization’s data and demand a ransom for the decryption key. Ransomware can lead to data loss, business disruption, and reputational damage.
Advanced Persistent Threats (APTs)
APTs are sophisticated and stealthy attacks typically orchestrated by nation-states or highly organized cybercriminal groups. APTs involve a prolonged and targeted effort to infiltrate an organization’s network and remain undetected for an extended period, often for the purpose of espionage or data theft.
Phishing
Phishing attacks remain a common entry point for cybercriminals. Attackers use deceptive emails, websites, or messages to trick individuals into divulging sensitive information, such as login credentials or financial data. Phishing attacks can lead to data breaches and financial losses.
Zero-Day Exploits
Zero-day exploits target vulnerabilities in software that are unknown to the vendor. Attackers exploit these vulnerabilities before the vendor can release a patch, making them highly effective for cyberattacks. Zero-day exploits can lead to system compromise and data breaches.
Insider Threats
Insider threats come from within an organization, whether intentionally or unintentionally. Employees or contractors may misuse their access privileges, leading to data leaks or security breaches. Insider threats can be challenging to detect and prevent.
The Need for a Comprehensive Cyber Resilient Endpoint Security Platform
As the threat landscape continues to evolve, traditional security measures are often insufficient. CISOs need a more comprehensive approach to cybersecurity that goes beyond perimeter defenses. This is where ThreatResponder by NetSecurity comes into play. ThreatResponder is an all-in-one, unified, cloud-native, machine learning-driven cyber-resilient endpoint security platform.
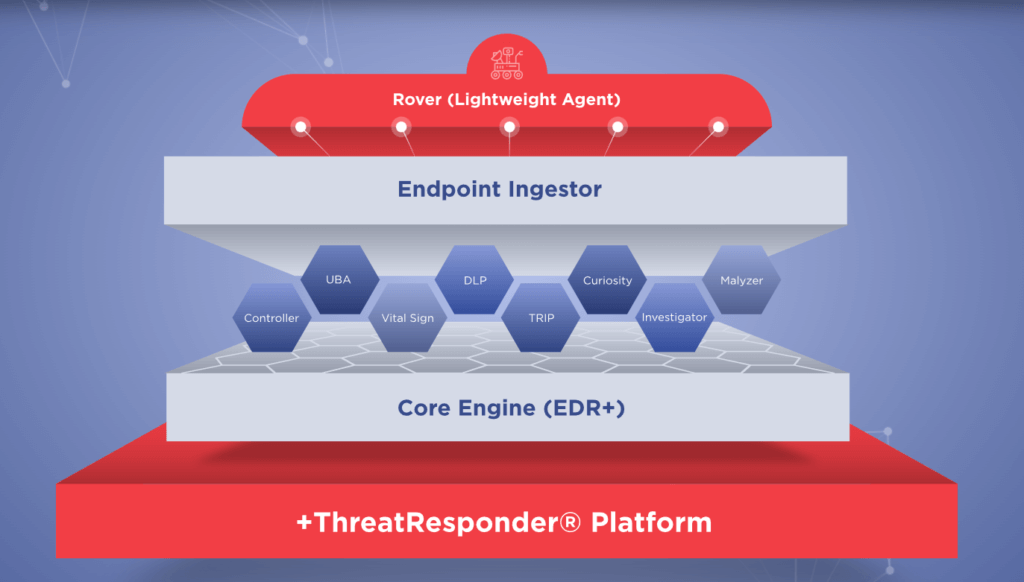
These pillars collectively create a formidable defense system against a wide range of cyber threats. However, in an ever-evolving digital world, there’s always room for improvement and expansion.
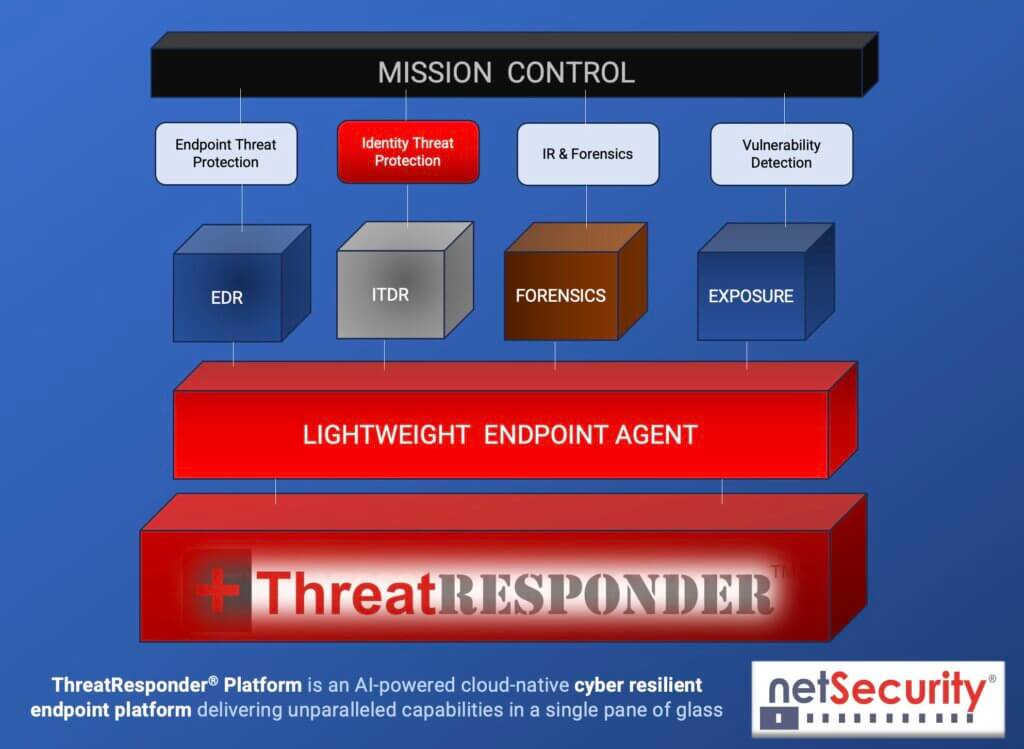
It is designed to provide cybersecurity teams with the necessary tools and insights to defend their organizations effectively. Let’s take a closer look at the core features of ThreatResponder:
Endpoint Detection and Response (EDR)
Endpoint Detection and Response is a critical component of modern cybersecurity. ThreatResponder continuously monitors endpoints (devices and servers) for signs of suspicious activities, such as malware infections or unusual behavior. When a threat is detected, ThreatResponder responds in real-time to mitigate the risk, making it an invaluable asset in threat containment and incident response.
Identity Threat Detection and Response
User identities are a prime target for attackers. ThreatResponder analyzes user behaviors and privileges to identify suspicious activities and potential threats. By understanding user identity and access patterns, it can detect unauthorized access and protect sensitive data from breaches.
Forensics
In the aftermath of a security incident, forensics play a crucial role in understanding the attack and its impact. ThreatResponder provides detailed forensic capabilities, helping CISOs and their teams analyze the scope of an incident, track the attacker’s movements, and collect evidence for potential legal action.
Threat Hunting
Proactive threat hunting is essential for identifying threats before they cause significant damage. ThreatResponder equips CISOs with advanced threat hunting tools, enabling them to search for hidden threats, vulnerabilities, and indicators of compromise within their organization’s network.
Vulnerability Detection
Identifying and patching vulnerabilities is a fundamental part of cybersecurity. ThreatResponder helps CISOs stay on top of vulnerabilities within their organization’s systems and applications, allowing them to prioritize and address weaknesses before they are exploited by attackers.
The Advantages of a Unified Approach
One of the key strengths of ThreatResponder is its unified approach to cybersecurity. By consolidating multiple security functions into a single platform, CISOs can benefit from the following advantages:
Simplified Management: Managing multiple cybersecurity solutions can be complex and time-consuming. ThreatResponder streamlines management, reducing the overhead associated with disparate security tools.
Enhanced Visibility: A unified platform provides a holistic view of an organization’s security posture, allowing CISOs to better understand their threat landscape and take proactive measures.
Improved Collaboration: ThreatResponder encourages cross-functional collaboration between security teams. It allows for the sharing of threat intelligence and coordinated incident response efforts.
Cost Efficiency: Investing in a single platform that encompasses multiple security functions can be more cost-effective than purchasing and maintaining numerous individual solutions.
Machine Learning-Driven Security
Machine learning is a key component of ThreatResponder’s effectiveness. This technology allows the platform to analyze vast amounts of data in real-time and detect complex threats that may go unnoticed by traditional security measures. Here are some ways machine learning enhances cybersecurity:
Threat Detection
Machine learning algorithms can identify patterns and anomalies in network traffic, user behavior, and file activity. This enables ThreatResponder to detect emerging threats and zero-day attacks that may not have known signatures.
Behavioral Analysis
Machine learning models can establish a baseline of normal behavior for an organization’s network and users. Deviations from this baseline can trigger alerts, allowing for the early detection of unusual activities.
Automation
Machine learning can automate threat response actions, such as isolating infected endpoints or blocking malicious network traffic, reducing the time it takes to contain threats.
Continuous Improvement
Machine learning models in ThreatResponder are continuously trained on new data, allowing them to adapt and improve their threat detection capabilities over time.
The Role of ThreatResponder in Cyber Resilience
Cyber resilience is the ability of an organization to withstand and recover from cyber threats while maintaining critical business operations. ThreatResponder plays a crucial role in building cyber resilience by providing real-time threat detection, response, and recovery capabilities.
Real-time Threat Detection
The ability to detect threats in real-time is a cornerstone of cyber resilience. ThreatResponder’s EDR and behavioral analysis capabilities allow CISOs to identify threats as they emerge, preventing them from causing significant harm.
Rapid Incident Response
In the event of a security incident, time is of the essence. ThreatResponder’s automation and orchestration features facilitate a swift and coordinated response, reducing the impact of an attack and helping the organization recover more quickly.
ThreatResponder in Action
To understand how ThreatResponder can be applied to defend against real-world cyber threats, let’s consider a hypothetical scenario:
Scenario: Ransomware Attack
Imagine that your organization has fallen victim to a ransomware attack. This type of attack can be devastating, but ThreatResponder is there to help.
- Early Detection: ThreatResponder’s EDR capabilities detect the ransomware infection as it attempts to encrypt files on multiple endpoints.
- Rapid Containment: ThreatResponder’s endpoint containment capabilities help isolate the infected workstation from the corporate network and block the spread of infection of ransomware attack.
- Automated Response: In response to the threat, ThreatResponder automatically isolates the infected endpoints to prevent further spread and damage.
- Behavioral Analysis: ThreatResponder analyzes user behavior and network traffic to trace the origin of the ransomware and identify potential weaknesses in the organization’s security.
- Forensic Investigation: CISOs use ThreatResponder’s forensic tools to investigate the attack further, collecting evidence for potential legal action against the attackers.
- Threat Hunting: The security team uses ThreatResponder’s threat hunting features to search for any residual threats or indicators of compromise.
By employing ThreatResponder in this scenario, organizations are not only able to contain the attack but also to gain valuable insights and strengthen their organization’s security posture for the future.
Try ThreatResponder
In the ever-evolving landscape of cyber threats, CISOs face the formidable task of defending their organizations from a myriad of risks. Traditional security measures are no longer sufficient to protect against advanced threats like ransomware, APTs, and zero-day exploits. To meet this challenge head-on, CISOs need advanced, unified, and machine learning-driven solutions like ThreatResponder by NetSecurity. This all-in-one platform equips CISOs and their teams with the tools and insights required to defend against cyber threats effectively and enhance their organization’s cyber resilience. As cyber threats continue to evolve, the role of CISOs in safeguarding their organizations becomes increasingly complex. With the right tools and strategies in place, CISOs can lead the charge in building a robust defense against cyber threats and ensuring the security and continuity of their organizations in an increasingly digital world. ThreatResponder is here to help them on that journey.
Are you ready to take the next step in defending your organization against cyber threats? Explore ThreatResponder by NetSecurity today and bolster your organization’s cybersecurity defenses.

Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).