The Stealthy Threat: Defending Organizations from Infostealers with ThreatResponder
Information-stealing malware, or infostealers, have emerged as a formidable threat to many organizations globally. These malicious programs burrow into devices with the sole purpose of siphoning sensitive data like login credentials, financial information, and even cryptocurrency wallets. Fueled by a lucrative black market for stolen data and armed with ever-increasing sophistication, infostealers pose a significant risk to individuals and organizations alike.
Famous Infostealers in Recent Times:
1. Redline Stealer:
Redline Stealer is a potent malware designed to exfiltrate sensitive information from compromised systems. It stealthily collects data such as login credentials, credit card details, and cryptocurrency wallets, posing a significant threat to individuals and organizations alike.
2. Racoon Stealer:
Racoon Stealer is a versatile malware tool used by cybercriminals to infiltrate systems and harvest valuable data. It is notorious for its ability to evade detection and extract a wide range of information, including browser cookies, saved passwords, and cryptocurrency wallets.
3. Rhadamanthys Stealer:
Rhadamanthys Stealer is a sophisticated malware strain known for its advanced information theft capabilities. It infiltrates systems, silently collects sensitive data, and transmits it to remote servers controlled by cybercriminals, posing a serious risk to cybersecurity.
4. Vidar Stealer:
Vidar Stealer is a malicious software designed to infiltrate systems and steal sensitive information, including personal and financial data. It operates covertly, often evading detection by security software, making it a significant threat to individuals and organizations worldwide.
5. Agent Tesla Stealer:
Agent Tesla Stealer is a dangerous malware variant used by cybercriminals to steal sensitive information from compromised systems. It can capture keystrokes, take screenshots, and extract credentials from various applications, presenting a substantial risk to cybersecurity and privacy.
Unveiling the Infostealer’s Arsenal: Techniques and Targets
Infostealers aren’t a monolithic entity. They encompass a diverse range of malware, each with its own set of functionalities and target data. Here’s a glimpse into their malicious toolkit:
- Keylogging: This classic technique captures every keystroke entered on the infected device, potentially revealing usernames, passwords, and other sensitive information.
- Form Grabbing: Infostealers can lurk within a website’s code, siphoning data entered into login forms, credit card details, and other online transactions.
- Browser Hooking: This more sophisticated method intercepts communication between the browser and the web server, allowing the infostealer to steal data before it’s encrypted.
- Credential Snatching: Many infostealers target cached login credentials stored within web browsers or password management applications.
- Cookie Theft: Cookies, which store website preferences and browsing history, can also be pilfered by infostealers. This information can be valuable for crafting targeted attacks or piecing together a user’s online identity.
- System Information Gathering: Beyond user data, some infostealers scrape system information like hardware specifications, software versions, and network configurations. This intel can be used to identify vulnerabilities for further exploitation or sold on the black market.
The information gleaned by infostealers is a goldmine for cybercriminals. Login credentials can be used to hijack email accounts, social media profiles, or even bank accounts. Financial information like credit card details can be used for fraudulent purchases, while stolen cryptocurrency wallets can drain a user’s digital assets
Tactics Used by Infostealers to Spread
Infostealers utilize a multitude of tactics to infiltrate devices and establish a foothold within a system. Here are some common distribution channels:
- Phishing Campaigns: Deceptive emails or messages disguised as legitimate sources often contain malicious attachments or links that, when clicked, download the infostealer.
- Drive-by Downloads: Visiting compromised websites can inadvertently trigger the download of an infostealer through hidden scripts or vulnerabilities within the site itself.
- Malicious Software Bundles: Free software downloads, particularly from untrusted sources, may be bundled with infostealers that piggyback on the installation process.
- Watering Hole Attacks: Cybercriminals may target legitimate websites frequented by a specific user group (e.g., online banking customers) and inject malicious code to infect visitors with infostealers.
- Exploiting Software Vulnerabilities: Unpatched vulnerabilities within operating systems or applications can be exploited by infostealers to gain unauthorized access to a device.
Prevent Infostealer attacks with ThreatResponder
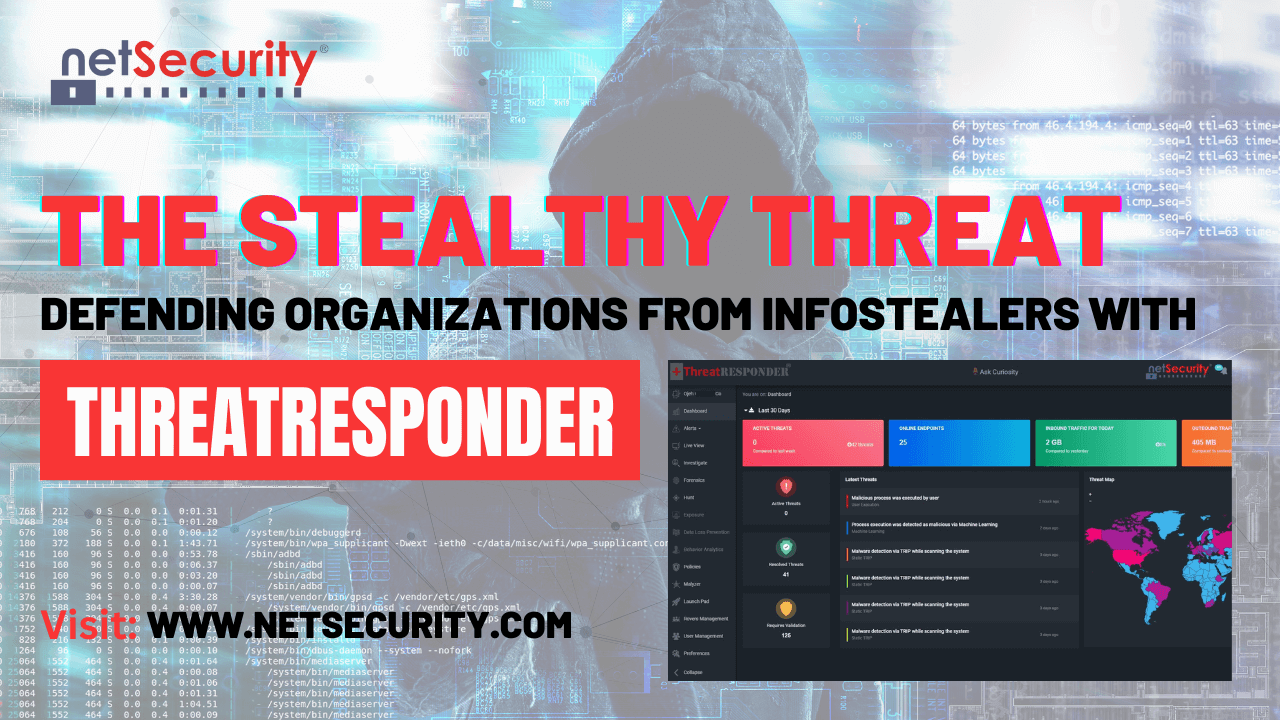
NetSecurity’s ThreatResponder® Platform is a comprehensive, cloud-native endpoint threat detection, prevention, response, analytics, intelligence, investigation, and hunting solution that can help businesses stay ahead of the latest cyber threats.
With ThreatResponder®, organizations gain situational awareness and immediate threat visibility into thousands of endpoints, allowing them to respond to and neutralize cyber attacks across their enterprise. The platform provides 361° threat visibility of enterprise assets, regardless of their location, and is capable of detecting and preventing a wide range of attacks, including exploit, fileless, malware, and ransomware attacks.
The platform is also designed to provide powerful tools for incident response and forensics investigation on remote endpoints, as well as insider threat and data loss prevention capabilities. Furthermore, ThreatResponder® can ingest data from millions of endpoints, providing organizations with valuable insights into users’ activities and network bandwidth utilization. The platform offers a comprehensive threat intelligence module, allowing organizations to consume threat intel from various sources, produce their own threat intelligence, and perform malware analysis using MaLyzer™.
NetSecurity’s ThreatResponder® Platform can help organizations stay ahead of the latest cyber threats. With its comprehensive features, ThreatResponder® provides organizations with the tools they need to detect, prevent, respond to, and investigate cyber attacks, all in one place.
Want to try our ThreatResponder, cutting-edge Endpoint Detection & Response (EDR), and ThreatResponder FORENSICS, the Swiss knife for forensic investigators in action? Click on the below button to request a free demo of our NetSecurity’s ThreatResponder platform.
Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).