Introducing ITDR in ThreatResponder: A Game-Changer in Revolutionizing Cybersecurity
In a world where digital threats loom large and cybersecurity breaches are a constant concern, the need for robust and comprehensive security solutions has never been greater. NetSecurity, a name synonymous with cutting-edge cybersecurity solutions, has consistently pushed the boundaries of innovation. Today, we are thrilled to introduce the latest addition to our arsenal: the Identity Threat Detection & Response (ITDR) module for our ThreatResponder Platform.
The ThreatResponder Platform has long been a stalwart in the realm of cybersecurity, offering a suite of tools and capabilities that empower organizations spread across different sectors and industries to defend against threats, respond to incidents, hunt for vulnerabilities, and secure their digital assets. With ITDR, we take our commitment to safeguarding your digital world to the next level. In this comprehensive blog post, we will delve into the world of NetSecurity’s ThreatResponder Platform and explore the transformative power of the ITDR module.
NetSecurity’s ThreatResponder Platform in a Nutshell
Before we dive into the exciting new ITDR module, let’s take a moment to understand the existing pillars of the ThreatResponder Platform.
ThreatResponder Platform is an all-in-one cloud-native endpoint threat detection, prevention, response, analytics, intelligence, investigation, and hunting product. Once lightweight agents (“Rovers”) are deployed, you gain situational awareness and immediate threat visibility into hundreds and thousands of endpoints, respond to nation-state and insider threats, and neutralize cyber attacks quickly. ThreatResponder® allows investigators to conduct incident response and computer forensics investigation on a remote endpoint.
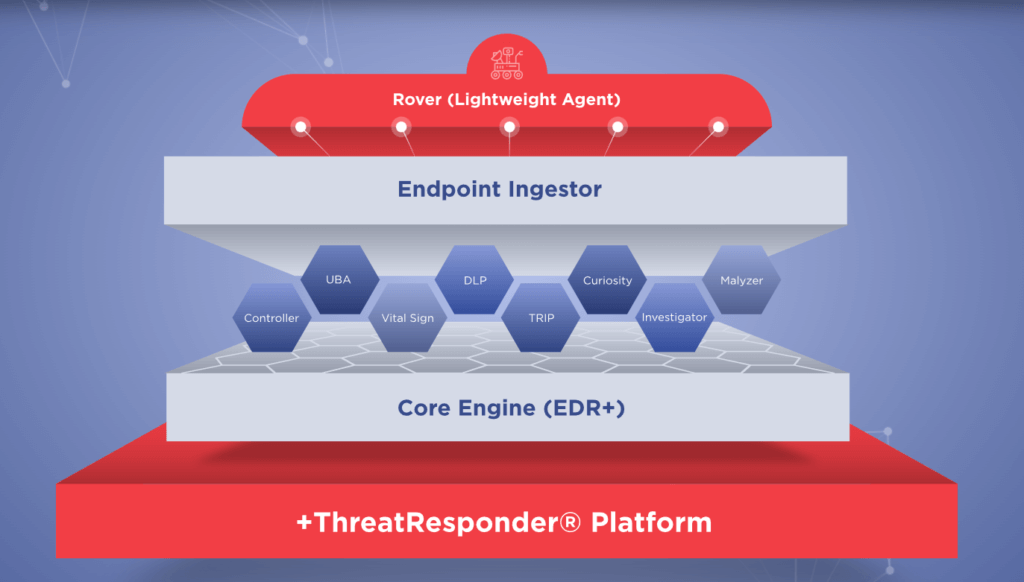
- Endpoint Threat Protection: At the heart of our platform lies robust endpoint threat protection. This critical component ensures that your devices, the entry points for many cyberattacks, are shielded from evolving threats.
- Incident Response & Forensics: In the unfortunate event of a security breach, a swift and effective response is essential. Our platform equips you with the tools needed to investigate incidents, gather forensics data, and take decisive action.
- Proactive Threat Hunting: Waiting for threats to come to you is not an option in today’s cybersecurity landscape. With ThreatResponder, you can proactively seek out vulnerabilities and threats, staying one step ahead of potential attackers.
- Vulnerability Detection: Identifying and patching vulnerabilities is crucial to reducing your attack surface. Our platform automates the process of vulnerability detection, helping you stay secure.
These pillars collectively create a formidable defense system against a wide range of cyber threats. However, in an ever-evolving digital world, there’s always room for improvement and expansion.
Why Organizations Need a Unified Platform?
Cybersecurity is a complex field with a multitude of threats and challenges. Managing various security tools and solutions can be a daunting task. This is where the power of integration comes into play.
A unified platform like ThreatResponder streamlines your cybersecurity operations. Instead of juggling multiple tools from different vendors, you have a single, centralized hub for monitoring, responding to incidents, and managing threats. This integration leads to more efficient workflows, reduced operational overhead, and better visibility into your organization’s security posture.
When it comes to cybersecurity, every second counts. A seamlessly integrated platform ensures that information flows in real-time, enabling faster decision-making and response to potential threats. It’s a game-changer in the race against cybercriminals.
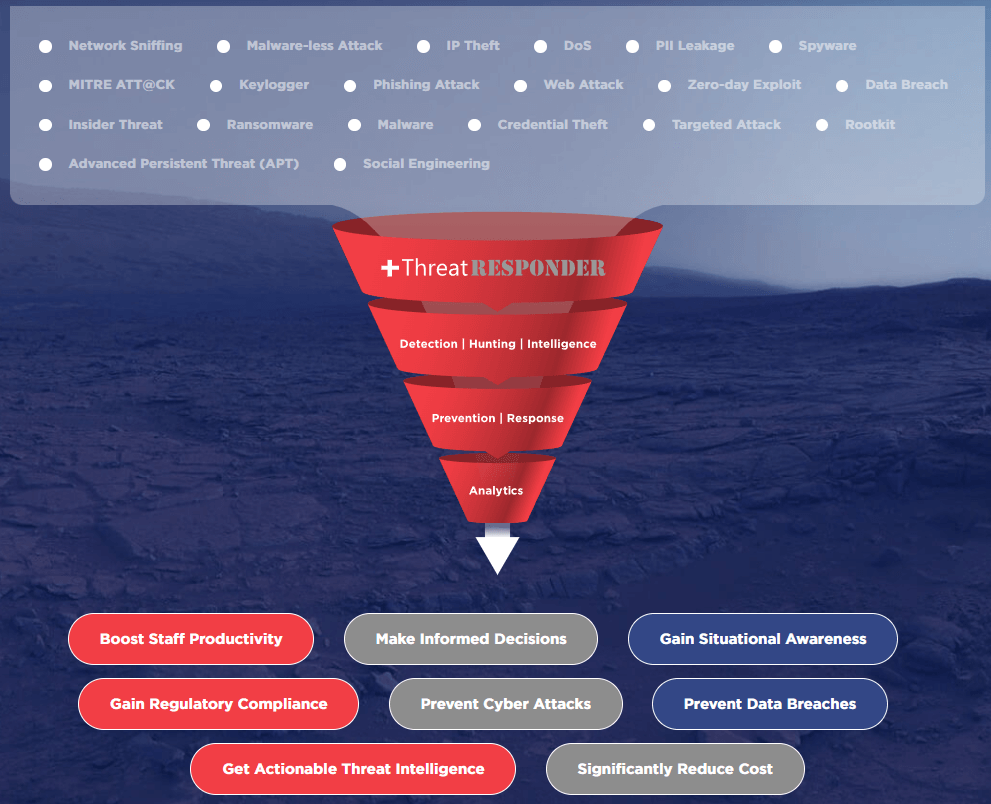
Introducing the Identity Threat Detection & Response (ITDR) Module
Now, let’s turn our attention to the star of the show: the Identity Threat Detection & Response (ITDR) module. ITDR represents a significant leap forward in cybersecurity, offering advanced threat detection and response capabilities poised to redefine how organizations safeguard their digital identities. Cyber threats are becoming increasingly sophisticated. Attackers are constantly devising new ways to infiltrate networks, compromise identities, and execute malicious actions from within organizations. To combat these evolving threats, we need a new approach—one that combines the power of technology and human intelligence.
This is where ITDR comes in. It leverages on-premises Active Directory events, a valuable source of security-related data, to ascertain, detect, and explore advanced threats, compromised identities, and malicious insider actions within your organization.
Unveiling ITDR’s Features
Let’s take a closer look at the key features that make ITDR a game-changer in the world of cybersecurity.
- ITDR: A Rule-Driven Approach: At the core of ITDR’s capabilities is a rule-driven approach. We have designed a set of rules for threat detection that you can enable or disable based on your organization’s unique security needs. This flexibility ensures that ITDR aligns seamlessly with your existing security protocols and policies. But we didn’t stop there. We understand that every organization is different, and threats can take various forms. That’s why ITDR allows you to define your own rules. This level of customization empowers you to tailor threat detection to your specific requirements, adapting to the ever-changing threat landscape.
- Leveraging On-Premises Active Directory Events: Active Directory is the backbone of user management in most organizations. ITDR harnesses the power of Active Directory events to gain deep insights into user activities, permissions, and potential anomalies.
- Advanced Threat Detection: ITDR employs advanced algorithms and machine learning to identify threats that might otherwise go unnoticed. It continuously analyzes Active Directory events to detect patterns indicative of potential threats.
- Compromised Identity Identification: One of the most challenging aspects of cybersecurity is identifying when user identities have been compromised. ITDR excels in this area, providing early warnings and actionable insights when it detects signs of identity compromise.
- Uncovering Malicious Insider Actions: Malicious insiders can pose a significant threat to organizations. ITDR keeps a vigilant eye on user activities, flagging suspicious actions that could indicate insider threats.
The Beauty of ITDR: Real-Time Network Insights
What sets ITDR apart is its ability to deliver real-time network insights that go beyond expectations. Imagine having a comprehensive view of what’s happening within your organization’s network, with the ability to detect and respond to threats as they unfold. That’s the beauty of ITDR.
By continuously monitoring Active Directory events and applying advanced analytics, ITDR provides a level of visibility that was previously elusive. It’s like having a digital guardian that never sleeps, tirelessly watching over your network and alerting you to potential dangers.
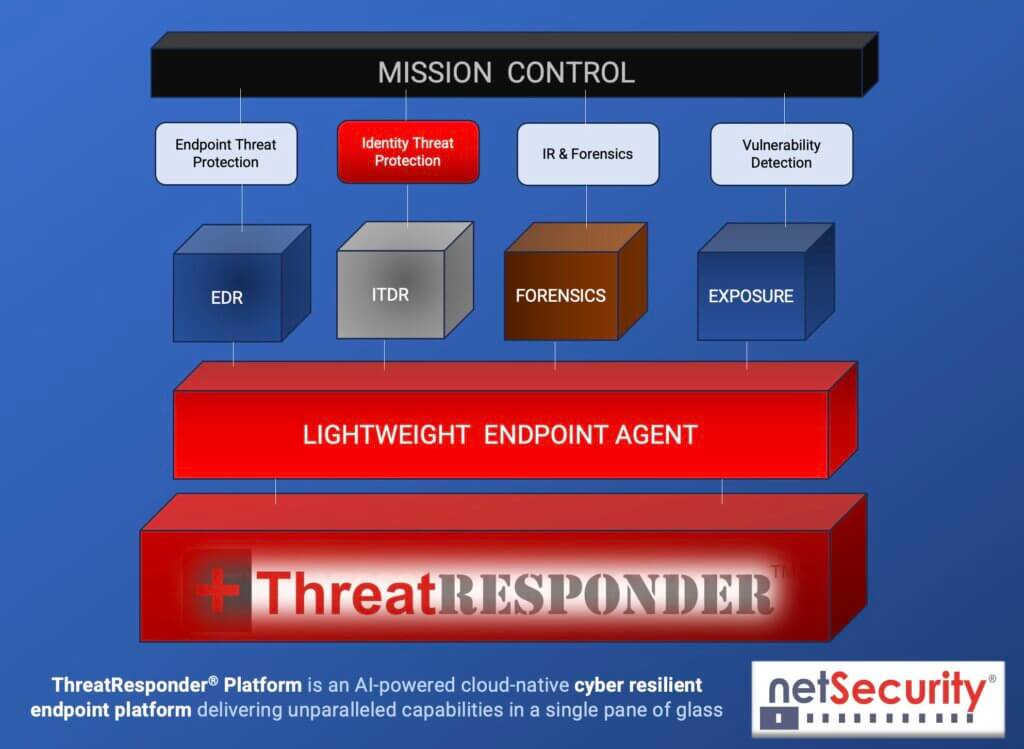
How ITDR Enhances ThreatResponder’s Ecosystem
The integration of ITDR into the ThreatResponder Platform enhances the overall ecosystem in profound ways. It adds a new layer of security intelligence that complements existing features. When combined with Endpoint Threat Protection, Incident Response & Forensics, Proactive Threat Hunting, and Vulnerability Detection, ITDR forms a comprehensive cybersecurity solution that leaves no stone unturned.
Imagine a scenario where a potential threat is detected by ITDR. Within moments, ThreatResponder’s incident response capabilities kick into action, isolating affected endpoints and initiating a forensic investigation. Proactive threat hunting tools are deployed to identify the root cause, and vulnerabilities are automatically assessed and patched. This seamless integration ensures a rapid and effective response to any threat.
This new ITDR engine complements the EDR, Forensics, and Vulnerability Detection (“Exposure”) modules. With the ITDR module, ThreatResponder detects and prevents real-time, identity-related threat activities in an AD environment that bypass typical EDRs and endpoint security products, including:
- Lateral movements (RDP, pass-the-hash, credential harvesting, Mimikatz, etc.)
- Reconnaissance (LDAP, BloodHound, SharpHound, etc.)
- Unusual endpoints usage
- Persistence (Golden Ticket attack, privilege escalation)
- Unusual login activities (unusual locations and hours)
- Outbound bytes anomalies for users (detect when users upload much more data than their daily averages)
In addition, this ITDR module helps organizations to:
- Monitors the event logs and network traffic of domain controllers
- Detects and prevents real-time, identity-related threat activities in an AD environment, including:
- Lateral movement (RDP, pass-the-hash, credential harvesting, Mimikatz, etc.)
- Reconnaissance (LDAP, BloodHound, SharpHound, etc.)
- Unusual endpoints usage
- Persistence (Golden Ticket attack, privilege escalation)
- Unusual login activities (unusual locations and hours)
- Outbound bytes anomalies for users (detect when users upload much more data than their daily averages)
- Allows for the creation of risk profiles for AD users
- Provides in-depth visibility into all user activities in an AD environment and with hunting capability
- Provides MITRE ATT&CK heat map of threats and detection
Preparing for the Future with ITDR
Cybersecurity is not a static field. Threats are continually evolving, and organizations must adapt to stay secure. ITDR is designed with this dynamic nature in mind. It equips organizations to:
- Adapt to Evolving Threat Landscapes: As new threats emerge, ITDR’s rule customization and advanced threat detection algorithms allow organizations to quickly adapt their security strategies.
- Enhance Insider Threat Detection: With insider threats on the rise, ITDR’s focus on identifying malicious insider actions is a critical asset.
- Stay Ahead of Identity Compromise: Identity compromise is a common attack vector. ITDR’s early detection capabilities help organizations prevent and mitigate these threats.
- Maintain Regulatory Compliance: ITDR’s detailed logging and reporting features assist organizations in meeting regulatory compliance requirements.
Glimpse of Identity Threat Detection & Response (ITDR) Module
At first, you will be presented with this alerts and summary view, that will show you the alerts stats and detections for ITDR:
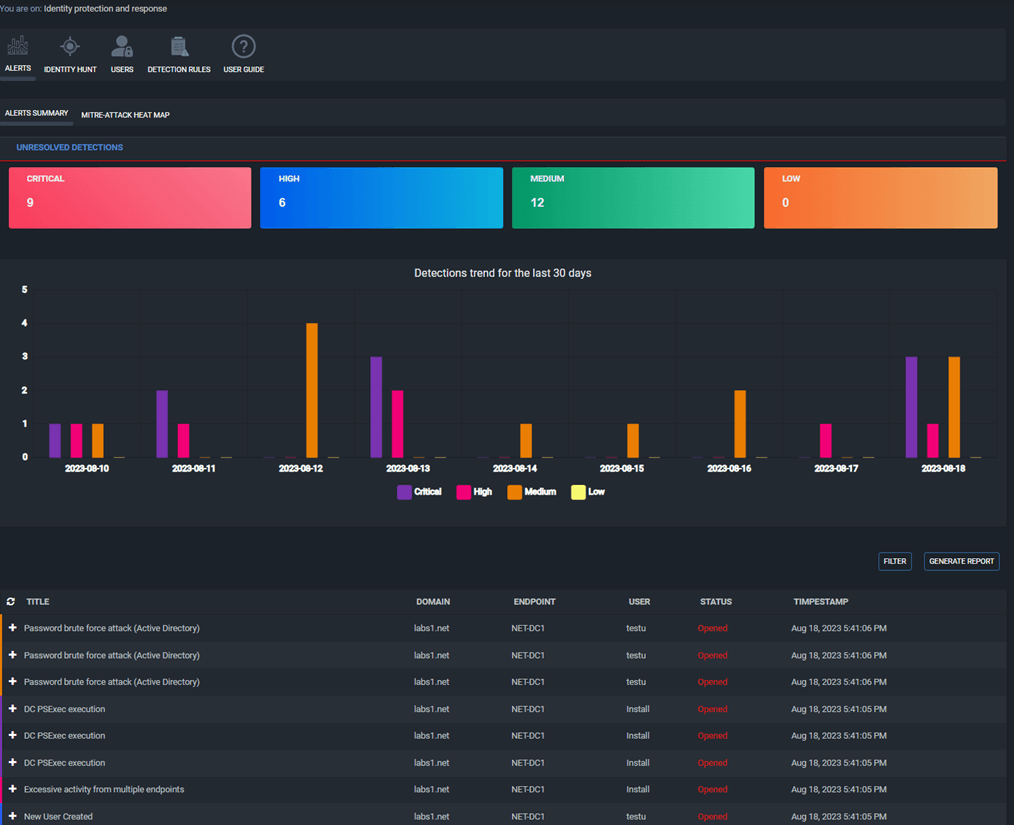
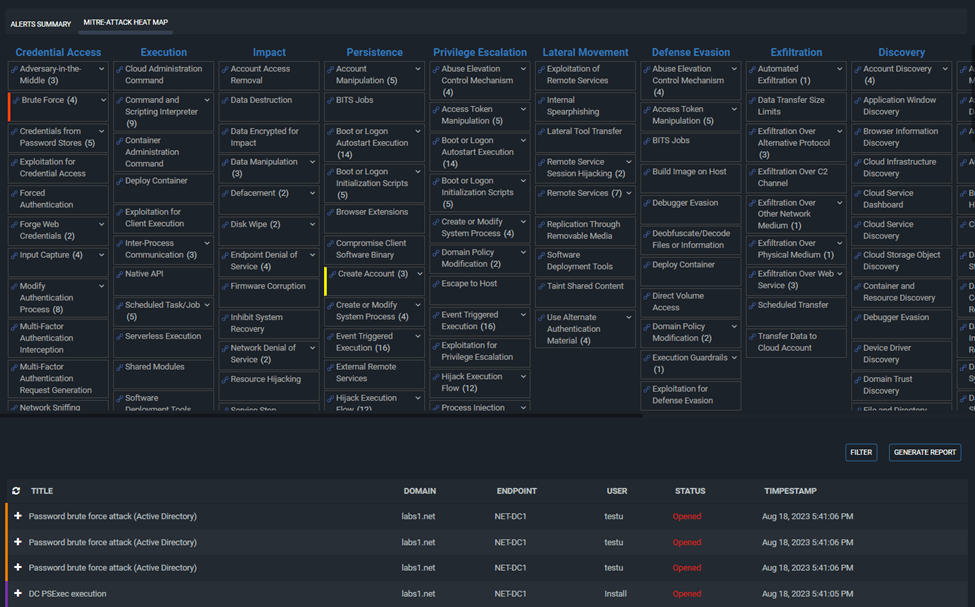
Additionally, we have a MITRE Heat Map view, where you can view which alert matched the MITRE techniques. When you click on a technique, the alerts will be filtered accordingly. It is the same for the stats, of you click on CRITICAL, HIGH, etc… the alert list will be filtered. So this dashboard is a little more interactive.
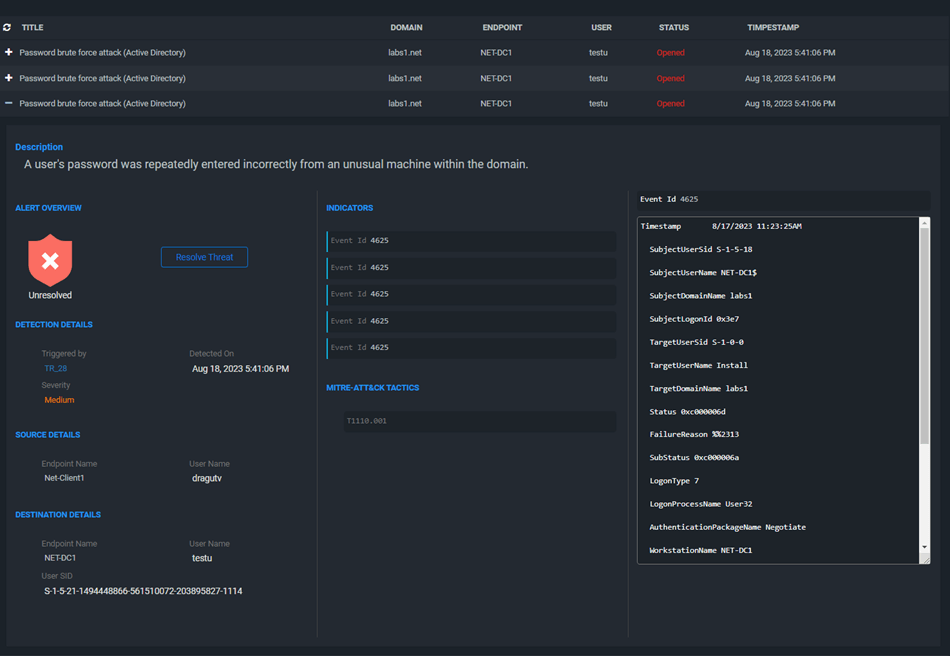
If you expand an alert, you can see more details about the detection. We still need to work on the presentation here a little bit:
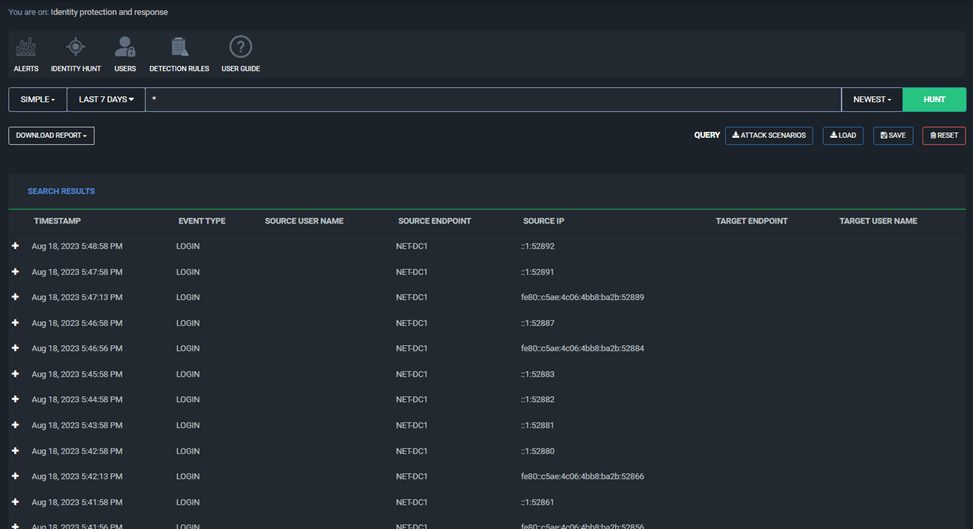
Then we have the Identity Hunt, which is the same functionality now as the User Hunt. The goal here is that in time we will show more identity related details.
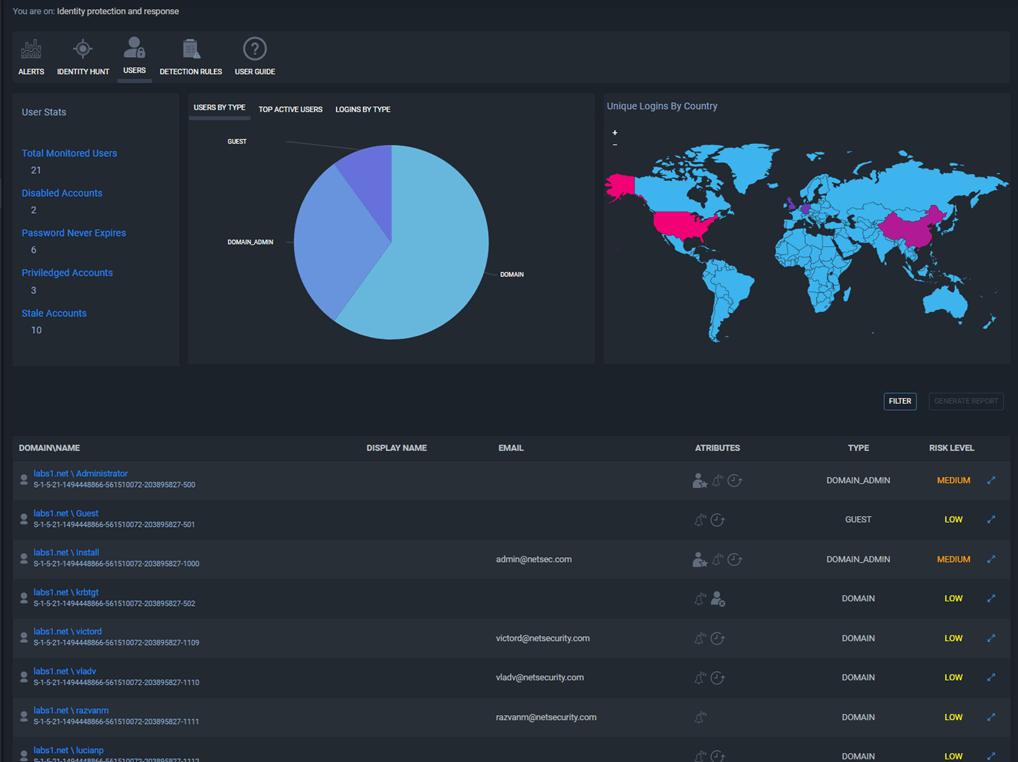
Then we have the users page, where you can see a list of all of the users in the AD environment, with different properties and filter characteristics. You can, for example, list users that:
- Have the password never expire property
- Stale users (users that were not active for a long time)
- Disabled accounts
- Etc.
So you can do a hygiene in the environment if you want to:
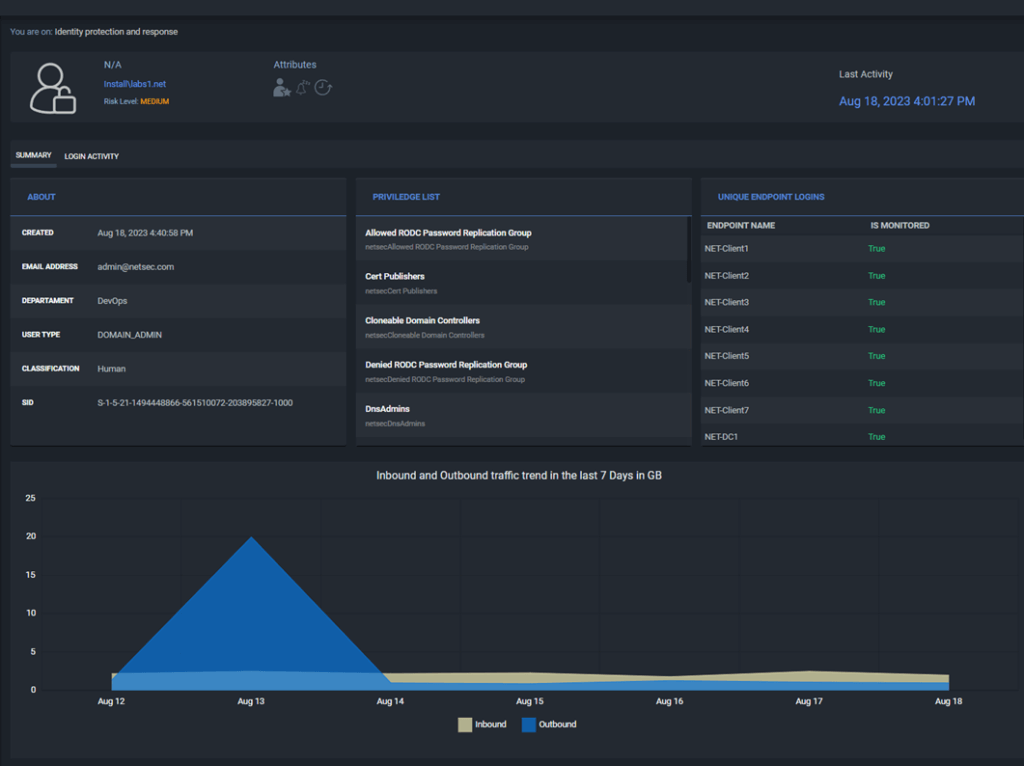
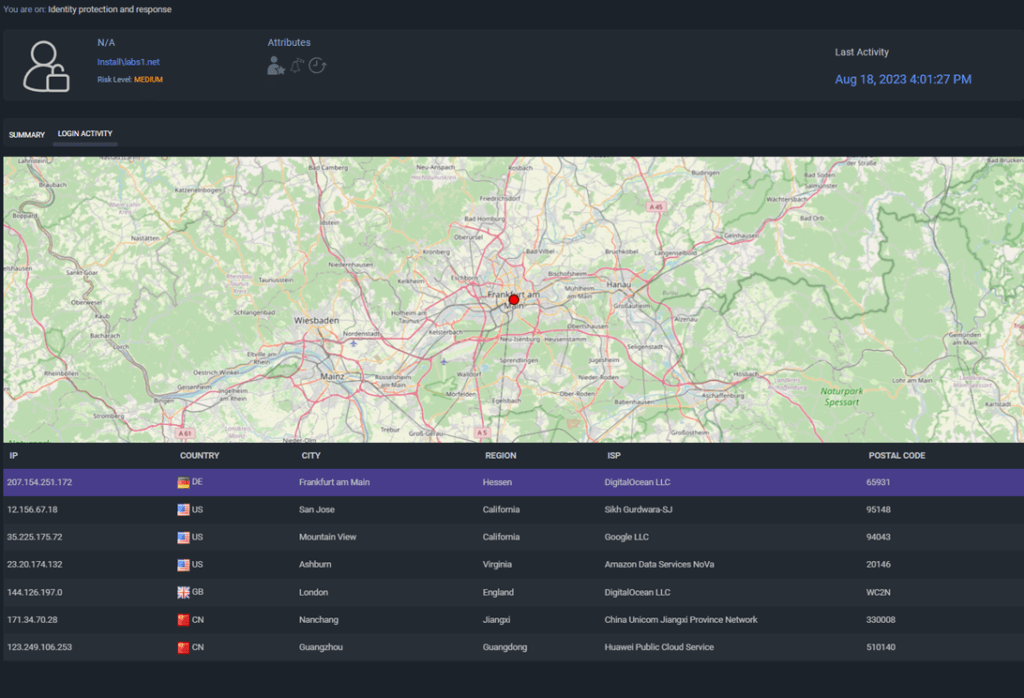
Each user in the AD environment, has a “User Story” page. Here we try to show various attributes and stats about the user if you want to investigate it further. This page is not finished as we need to add a timeline of the user activity:
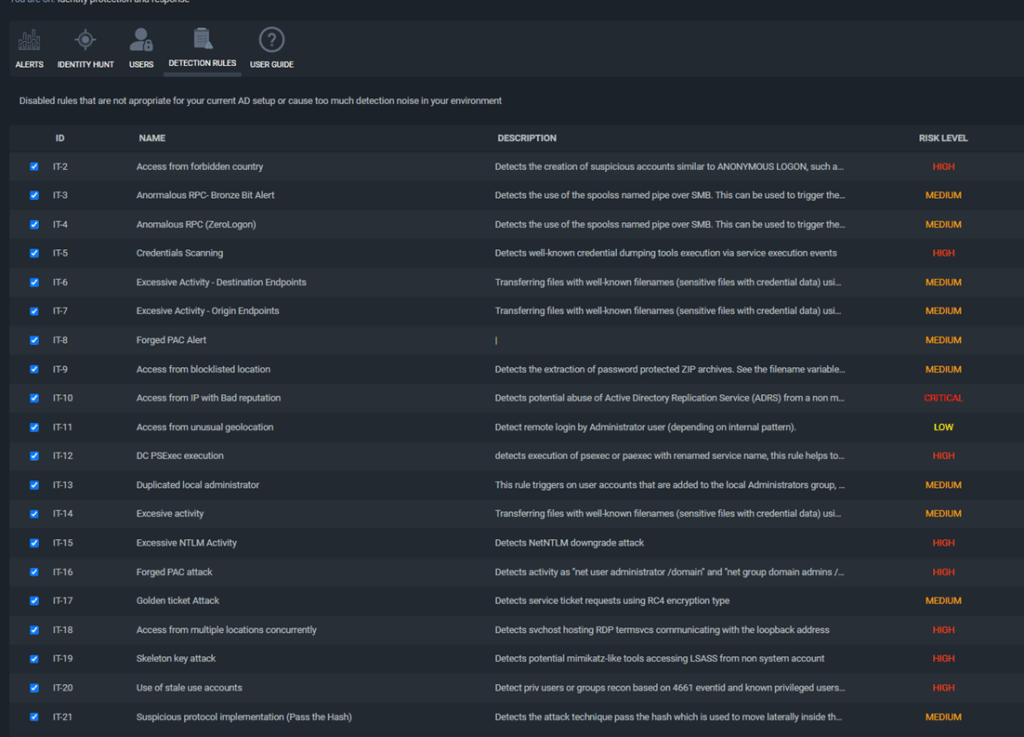
You can then see what detection rules are enabled and if you want you can modify the enabled/disabled list:
There are still a lot of things to be done and will be done, but this is just the beginning.
Bringing ITDR to Our Users
We are excited to announce that the ITDR module will be available to all our users starting next week. As we prepare to roll out ITDR to our users, we invite you to join us on this journey to elevate your organization’s cybersecurity. Together, we can face the evolving threat landscape with confidence, knowing that the power of ITDR and ThreatResponder is on our side. Protecting your digital world has never been more achievable, and we’re excited to embark on this cybersecurity adventure with you. Stay secure, stay vigilant, and stay protected with NetSecurity’s ThreatResponder Platform. Considering the unparalleled protection and insights it provides, we believe this investment in your organization’s security is well worth it. Thanks for your continued support/patronage!
Try ThreatResponder for Free
Want to try our ThreatResponder, cutting-edge Endpoint Detection & Response (EDR), and ThreatResponder FORENSICS, the Swiss knife for forensic investigators in action? Click on the below button to request a free demo of our NetSecurity’s ThreatResponder platform.
Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).