What is Identity Threat Detection and Response (ITDR) and What are its Benefits?
In today’s digital landscape, businesses face numerous cyber threats that can compromise their sensitive data, intellectual property, and reputation. One such critical aspect of cyber security is Identity Threat Detection and Response (ITDR). This blog post aims to delve into the concept of ITDR, its significance in safeguarding businesses, and the crucial role it plays in the ever-evolving cybersecurity landscape.
Understanding ITDR
Identity Threat Detection and Response (ITDR) is a proactive approach to cyber security that focuses on detecting and mitigating threats targeting user identities within an organization’s network. It involves constantly monitoring user activities, analyzing behavior patterns, and promptly responding to any suspicious or potentially malicious activities. Through ITDR procedures, businesses seek to discover potential and actual identity-related threats, respond to them appropriately, and reduce the likelihood of them reoccurring. Identities are a top target of cybercriminals; in fact, Verizon reports that nearly half (49%) of breaches involve credentials. It’s no wonder Gartner includes identity threat detection and response (ITDR) among its top 7 cybersecurity trends.

The Importance of ITDR to Businesses
ITDR works as the second and third layers of Defense after Prevention. Identity-related threats encompass various malicious activities, including account takeover fraud, synthetic identity creation, data breaches, and phishing attacks. These threats pose significant risks to businesses as cybercriminals increasingly target user identities and credentials. In fact, nearly half of all breaches involve compromised credentials, making ITDR a crucial aspect of cybersecurity.
ITDR plays a pivotal role in safeguarding companies from the financial, reputational, legal, and regulatory consequences of fraud and identity-related breaches. In fact, in 2022, the Identity Defined Security Alliance (IDSA) reported that a staggering 84% of organizations had experienced identity-related breaches, with 78% reporting direct operational impacts. This underscores the urgency of implementing robust ITDR measures.
Key Features to Look for in ITDR Solutions:
When considering ITDR solutions, it’s essential to prioritize customizable risk rules, advanced monitoring using machine learning, and customizable automation:
- Customizable Risk Rules: Tailor your ITDR solution to your specific business needs and risk tolerance. Fine-tune the system to minimize false positives, reducing fraud risks without inconveniencing legitimate users.
- In-Depth Monitoring: Seek solutions that leverage machine learning for adaptive identity and behavioral analysis. Anomaly detection is crucial for flagging unusual activities that may indicate identity threats.
- Customizable Automation: Configure automated responses to suspicious activities, ensuring real-time actions are taken and the appropriate personnel are alerted.
ThreatResponder’s ITDR Module:
Now, let’s turn our attention to the star of the show: the Identity Threat Detection & Response (ITDR) module. ITDR represents a significant leap forward in cybersecurity, offering advanced threat detection and response capabilities poised to redefine how organizations safeguard their digital identities. Cyber threats are becoming increasingly sophisticated. Attackers are constantly devising new ways to infiltrate networks, compromise identities, and execute malicious actions from within organizations. To combat these evolving threats, we need a new approach—one that combines the power of technology and human intelligence.
This is where ITDR comes in. It leverages on-premises Active Directory events, a valuable source of security-related data, to ascertain, detect, and explore advanced threats, compromised identities, and malicious insider actions within your organization.
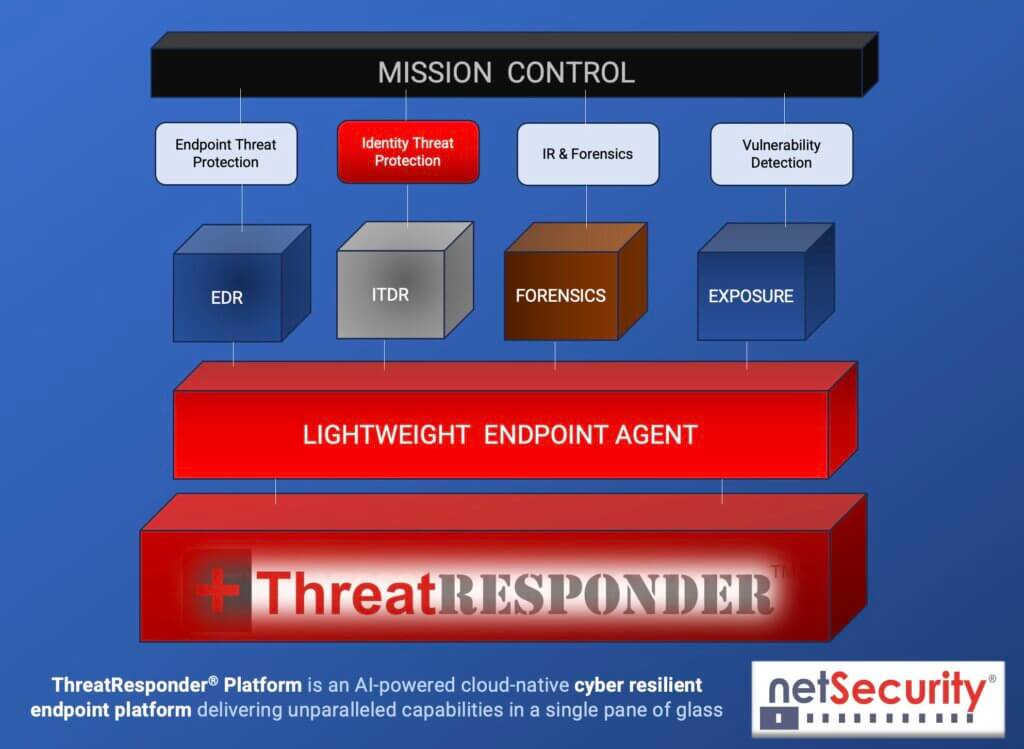
Let’s take a closer look at the key features that make ITDR a game-changer in the world of cybersecurity.
- ITDR: A Rule-Driven Approach: At the core of ITDR’s capabilities is a rule-driven approach. We have designed a set of rules for threat detection that you can enable or disable based on your organization’s unique security needs. This flexibility ensures that ITDR aligns seamlessly with your existing security protocols and policies. But we didn’t stop there. We understand that every organization is different, and threats can take various forms. That’s why ITDR allows you to define your own rules. This level of customization empowers you to tailor threat detection to your specific requirements, adapting to the ever-changing threat landscape.
- Leveraging On-Premises Active Directory Events: Active Directory is the backbone of user management in most organizations. ITDR harnesses the power of Active Directory events to gain deep insights into user activities, permissions, and potential anomalies.
- Advanced Threat Detection: ITDR employs advanced algorithms and machine learning to identify threats that might otherwise go unnoticed. It continuously analyzes Active Directory events to detect patterns indicative of potential threats.
- Compromised Identity Identification: One of the most challenging aspects of cybersecurity is identifying when user identities have been compromised. ITDR excels in this area, providing early warnings and actionable insights when it detects signs of identity compromise.
- Uncovering Malicious Insider Actions: Malicious insiders can pose a significant threat to organizations. ITDR keeps a vigilant eye on user activities, flagging suspicious actions that could indicate insider threats.
What can ThreatResponder’s ITDR Do?
Though there are many use cases for the ITDR module, mentioned below are a few identity threats that ThreatResponder’s ITDR module can help thwart:
- Lateral movements (RDP, pass-the-hash, credential harvesting, Mimikatz, etc.)
- Reconnaissance (LDAP, BloodHound, SharpHound, etc.)
- Unusual endpoints usage
- Persistence (Golden Ticket attack, privilege escalation)
- Unusual login activities (unusual locations and hours)
- Outbound bytes anomalies for users (detect when users upload much more data than their daily averages)
In addition, this ITDR module helps organizations to:
- Monitors the event logs and network traffic of domain controllers
- Detects and prevents real-time, identity-related threat activities in an AD environment, including:
- Lateral movement (RDP, pass-the-hash, credential harvesting, Mimikatz, etc.)
- Reconnaissance (LDAP, BloodHound, SharpHound, etc.)
- Unusual endpoints usage
- Persistence (Golden Ticket attack, privilege escalation)
- Unusual login activities (unusual locations and hours)
- Outbound bytes anomalies for users (detect when users upload much more data than their daily averages)
- Allows for the creation of risk profiles for AD users
- Provides in-depth visibility into all user activities in an AD environment and with hunting capability
- Provides MITRE ATT&CK heat map of threats and detection
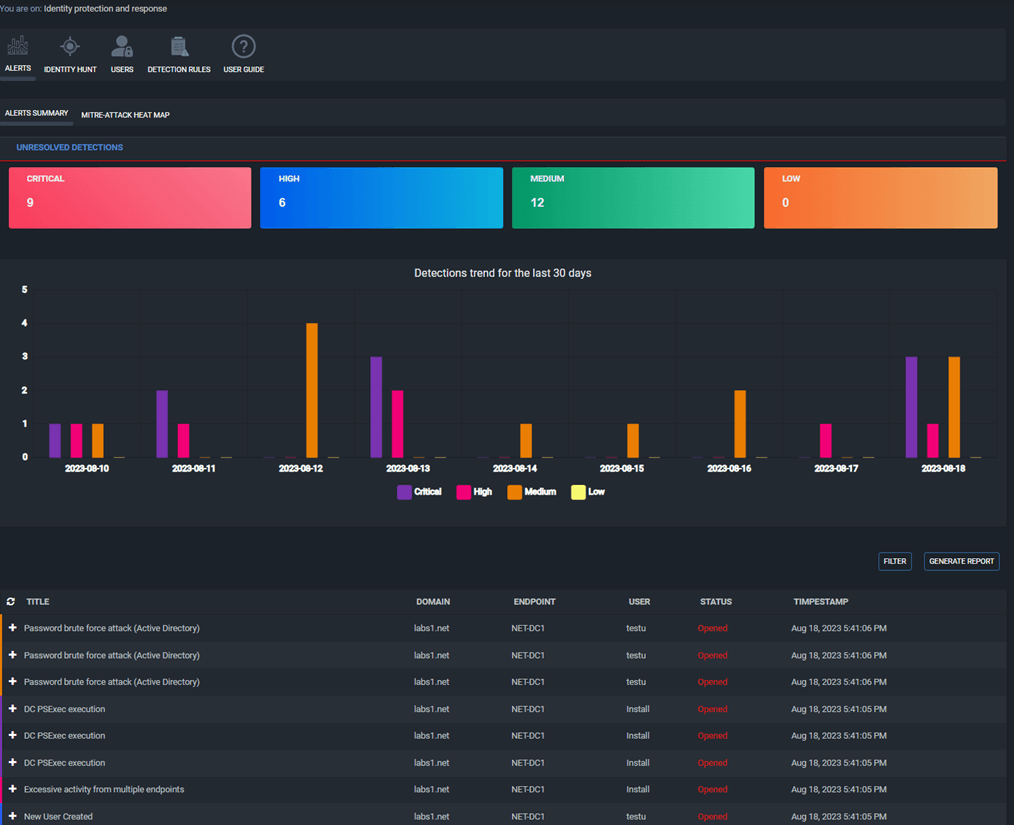
ThreatResponder’s ITDR Module Dashboard
Try ThreatResponder for Free
Want to try our ThreatResponder, cutting-edge Endpoint Detection & Response (EDR), and ThreatResponder FORENSICS, the Swiss knife for forensic investigators in action? Click on the below button to request a free demo of our NetSecurity’s ThreatResponder platform.
Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).