What are Type 1 and Type 2 Errors in Cyber Security. Which One is Dangerous To Your Organization?
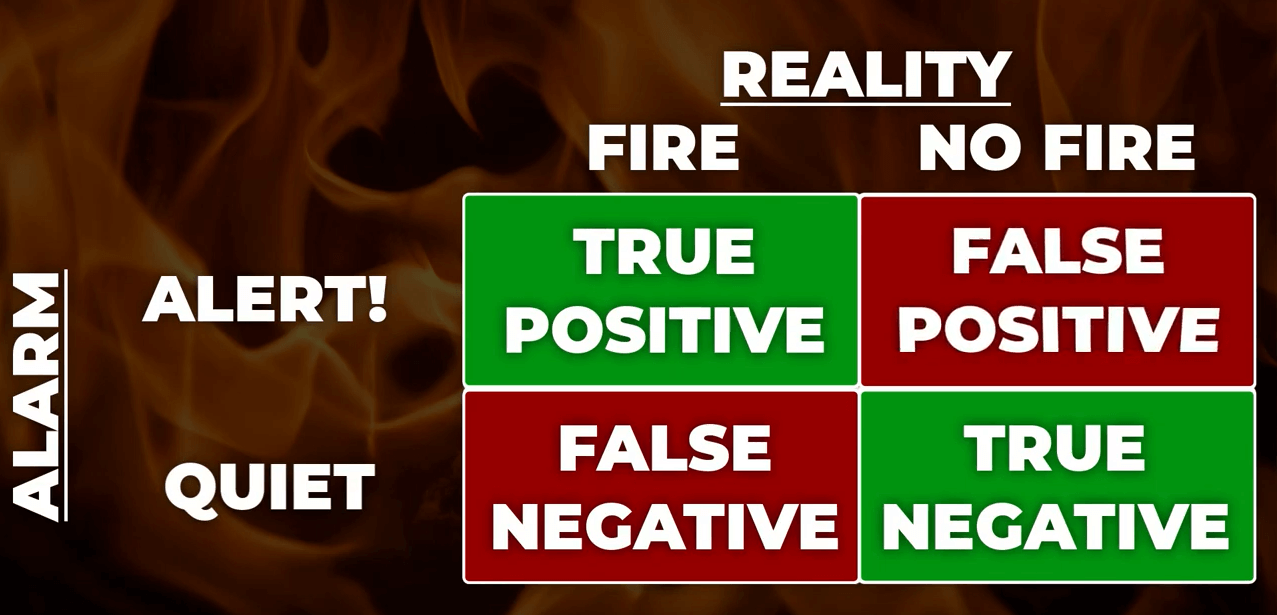
Type 1 and Type 2 errors are the statistical methodologies that are applicable to determine if the result is a false positive or false negative. In cyber security, as large number of security tools are employed to determine if a threat is real. In most of the situations, these tools are effective in detecting the real threats to organizations. Such accurate detection are called as “True Positive” alerts. However, there are chances that, in some situations, these tools can go wrong and trigger false alerts. These errors are classified in two types:
What are Type 1 Errors?
Type 1 error is also called as “False Positive” errors. For example, if a security tool triggers alerts without any actual threat/risk to the organization, then this type of alert is considered to be a “False Positive” alert. Another simpler example to understand type 1 error in cyber security is “Authentic users being classified as hackers by security tools.” False positive alerts are very common in the cyber security operations and soc analysts can tune the security rules or tools accordingly to reduce the number of false positive alerts.
What are Type 2 Errors?
Type 2 error is also called as “False Negative” errors. For example, despite the existence of threat/risk to the organization, if a security tool does not generate an alert, then it is considered to be a “False Negative” error. Another simpler example to understand type 1 error in cyber security is “hackers are accepted as authorized users by security tools.” Such errors can be extremely dangerous and can cause serious damage to the organizations. It is extremely important to remediate any such Type 2 errors as soon as possible to avoid serious damages and avoid the disruption of entire business.
How To Avoid Type 1 & Type 2 Errors and Detect Advanced Cyber Threats?
Cyber security threats and ransomware attacks are increasing at a tremendous pace. It is extremely difficult for cyber security analysts and incident responders to investigate and detect cyber security threats using conventional tools and techniques. NetSecurity’s ThreatResponder, with its cloud-based machine learning threat detection engine and its diverse capabilities, can help your team detect the most advanced cyber threats, including APTs, zero-day attacks, and ransomware attacks. It can also help automate incident response actions across millions of endpoints, making it easy, fast, and hassle-free.
Want to try our ThreatResponder, cutting-edge Endpoint Detection & Response (EDR), and ThreatResponder FORENSICS, the Swiss knife for forensic investigators in action? Click on the below button to request a free demo of our NetSecurity’s ThreatResponder platform.
Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).