Unmasking the QBot: How this Banking Trojan Attacks Your Organization
What is QBot?
The QakBot banking Trojan, also known as QBot, QuackBot, and Pinkslipbot, has been around for over a decade. It was discovered in 2007 and is continuously developed and maintained since then. Over the last few years, QakBot has emerged as one of the most prevalent banking Trojans on the internet. Although its main purpose is to steal banking credentials (e.g., logins and passwords), it has also acquired functionalities that allow it to spy on financial operations, spread itself, and install ransomware.
Even today, QakBot is still growing in functionality, including keystroke logging, a backdoor, and techniques to evade detection. Besides detecting virtual environments, it can also perform auto-updates and changes cryptor/packer settings. Further, QakBot is designed to prevent experts or automated tools from analyzing and debugging it.
Another interesting piece of functionality is the ability to steal emails. By using this information, attackers later send targeted emails to victims, luring them into opening those emails with the information they’ve obtained.
How QBot Attack?
QakBot is a malicious threat that is known to infect its victims mainly through spam campaigns. These campaigns often involve Microsoft Office documents (Word, Excel) or password-protected archives containing malicious macros, claiming that they contain important information, like an invoice. In some cases, the emails contain links to web pages that host malicious documents. Furthermore, the payload may also be transferred to the victim’s machine via other malware already present on the compromised machine. The vector of infection may vary depending on the nature of the target organization. Cybercriminals often perform OSINT beforehand to decide which infection vector will be most effective.
The attack chain of recent QakBot attacks are as follows:
-
Attacker sends phishing emails with malicious HTML or ZIP attachments containing an Office document or a virtual harddrive to the targeted victims.
-
The user receives the phishing email and clicks the malicious document.
- A malicious macro is executed. Some variants perform a ‘GET’ request to a URL requesting a ‘PNG’ However, the file is in fact a binary.
-
In addition to the loaded payload (stager), another binary contains encrypted resource modules. During runtime, the DLL binary (loader) is decrypted from one of the encrypted resources.
-
A ‘Stager’ loads the ‘Loader’ into memory, which runs the payload during runtime. It retrieves configuration settings from another resource.
-
The payload communicates with the C2 server.
-
Additional threats such as ProLock, Royal, Black Basta ransomware can now be pushed to the infected machine.
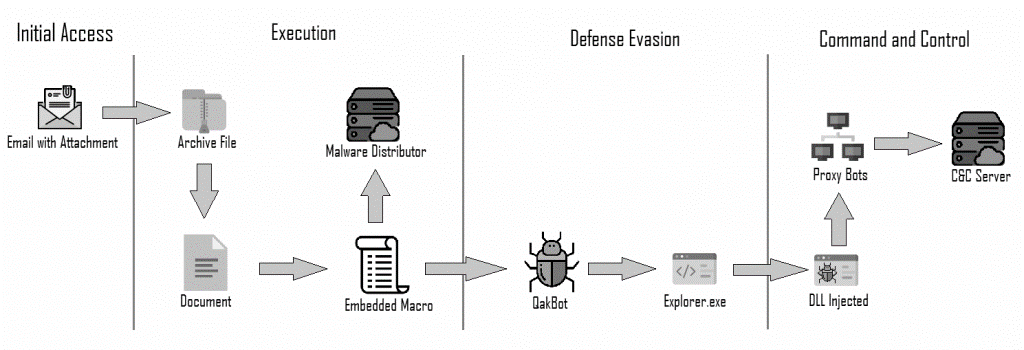
QBot Ransomware Attack Flow
How to Prevent QBot Ransomware Attack
Cyber security threats and ransomware attacks are increasing at a tremendous pace. It is extremely difficult for cyber security analysts and incident responders to investigate and detect cyber security threats using conventional tools and techniques. NetSecurity’s ThreatResponder, with its cloud-based machine learning threat detection engine and its diverse capabilities, can help your team detect the most advanced cyber threats, including APTs, zero-day attacks, and ransomware attacks. It can also help automate incident response actions across millions of endpoints, making it easy, fast, and hassle-free.
Want to try our ThreatResponder, cutting-edge Endpoint Detection & Response (EDR), and ThreatResponder FORENSICS, the Swiss knife for forensic investigators in action? Click on the below button to request a free demo of our NetSecurity’s ThreatResponder platform.