Elevate Your Cybersecurity Team’s Morale with ThreatResponder Forensics
Challenges For Cyber Security Analysts
Cybersecurity analysts who perform computer and Windows forensic investigations face a range of challenges in their work. Some of the key problems they encounter include:
- Rapidly Evolving Threat Landscape: Cyber attackers are constantly developing new techniques and methods to breach security systems, making it challenging for analysts to keep up with the latest threats and respond appropriately.
- Volume and Complexity of Data: In computer and Windows forensic investigations, analysts are often required to sift through large volumes of data, including logs, network traffic, and system files. This can be a time-consuming and complex task, particularly when the data is spread across multiple devices or locations.
- Encryption and Obfuscation: Cybercriminals often use encryption and obfuscation techniques to hide their activities and make it more difficult for analysts to identify and analyze their actions.
- Lack of Resources: Cybersecurity teams may have limited resources, including personnel, time, and funding, which can make it difficult to conduct thorough forensic investigations.
- Collaboration and Communication: In many cases, forensic investigations require collaboration between different teams and stakeholders, including law enforcement, legal counsel, and other experts. Effective communication and collaboration are essential for ensuring that investigations are conducted efficiently and accurately.
- Stress and Fatigue: Cybersecurity investigations can be extremely stressful and mentally demanding, requiring analysts to sift through large volumes of data, identify patterns, and make critical decisions under pressure. This can lead to high levels of stress and fatigue, which can negatively impact the quality of the investigation and the mental health of the analysts.
- Artifact Collection: Collecting relevant artifacts during a forensic investigation can be a complex and time-consuming process. Analysts must identify the types of artifacts that are relevant to the investigation, and then locate, extract, and analyze them. Some artifacts may be hidden or difficult to access, while others may be located on remote devices or in the cloud.
- Reporting: Once an investigation is complete, analysts must produce a detailed report that summarizes their findings and provides recommendations for remediation. This report must be comprehensive, accurate, and detailed enough to withstand scrutiny in a court of law, if necessary. Preparing such a report can be challenging, particularly if the investigation involved a large number of devices, users, or systems.
Overall, performing computer and Windows forensic investigations requires a high level of skill, knowledge, and attention to detail. Analysts must be able to navigate a range of technical, legal, and organizational challenges, while ensuring that they collect and analyze all relevant artifacts and produce accurate and comprehensive reports. Effective communication and collaboration with other stakeholders, such as legal counsel and law enforcement, are also critical to the success of the investigation. By reducing the work load, stress and leveraging advanced cybersecurity resilience tools like ThreatResponder Forensic you can elevate the morale of your cybersecurity team to tackle advanced cyber threats.
How is ThreatResponder Different and How it Can Elevate Your Team Morale
NetSecurity’s ThreatResponder Forensic Module is an advanced solution that can help solve the challenges faced by cybersecurity analysts during computer and Windows forensic investigations. This module is designed to offer a comprehensive range of capabilities, including a machine learning-based detection engine, light-weight agent, advanced detection capabilities, easy evidence collection, and automatic report generation.
One of the key features of ThreatResponder’s Forensic Module is its machine learning-based detection engine. This engine is designed to detect rapidly evolving threats with behavioral analysis, which can help analysts stay ahead of emerging threats. By analyzing patterns of behavior across multiple devices and systems, this engine can identify anomalies that may indicate a security breach or other malicious activity.
Another important capability of ThreatResponder’s Forensic Module is its lightweight agent. This agent is designed to collect and deliver large volumes of complex data, including logs, network traffic, and system files, without impacting system performance. This data is then made available to the analyst through the management console, which provides an easy-to-understand view of the data.
ThreatResponder’s Forensic Module also has advanced detection capabilities that can decrypt and deobfuscate encrypted and obfuscated data, making it easier for analysts to identify and analyze malicious activity. Additionally, the module is capable of recovering deleted files, which can be critical in investigations where data may have been intentionally or accidentally destroyed.
In terms of evidence collection, ThreatResponder’s Forensic Module makes this process easy and effective. Analysts can quickly and easily collect all relevant artifacts, including files, registry keys, and other system data, using the module’s built-in tools. This evidence can then be analyzed and correlated with other data to build a complete picture of the incident.
Finally, ThreatResponder’s Forensic Module includes automatic report generation, which can be critical for effective communication and collaboration with other stakeholders, such as legal counsel and law enforcement. The module can automatically generate a detailed report that summarizes the findings of the investigation and provides recommendations for remediation. This report can be presented to management and other stakeholders to help inform decision-making and ensure that appropriate action is taken.
Overall, NetSecurity’s ThreatResponder Forensic Module is an advanced solution that can help cybersecurity analysts overcome the many challenges they face during computer and Windows forensic investigations. By providing advanced detection capabilities, easy evidence collection, and automatic report generation, this module can help analysts stay ahead of emerging threats, identify and analyze malicious activity, and communicate effectively with other stakeholders.
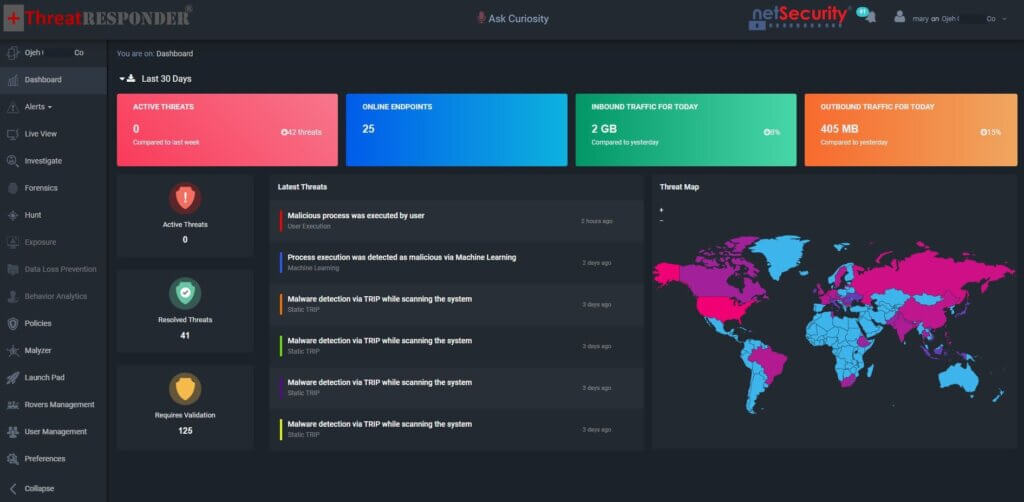
ThreatResponder Dashboard
In addition to these features, ThreatResponder also provides advanced analytics capabilities that help organizations quickly identify and respond to potential threats. The solution is designed to be easy to use, allowing organizations to quickly implement and start using it to prevent cyber attacks.Want to try our ThreatResponder, cutting-edge Endpoint Detection & Response (EDR), and ThreatResponder FORENSICS, the Swiss knife for forensic investigators in action? Click on the below button to request a free demo of our NetSecurity’s ThreatResponder platform.
Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).