CISA, FBI, MS-ISAC, and ASD’s ACSC Release Advisory on LockBit Affiliates Exploiting Citrix Bleed (CVE-2023-4966)
The Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), Multi-State Information Sharing & Analysis Center (MS-ISAC), and Australian Signals Directorate’s Australian Cyber Security Center (ASD’s ACSC) have recently released a joint Cybersecurity Advisory (CSA) on LockBit Affiliates Exploiting Citrix Bleed.
The Threat Landscape
The advisory was released in response to LockBit 3.0 ransomware affiliates and multiple threat actor groups exploiting CVE-2023-4966. This vulnerability, labeled as Citrix Bleed, affects Citrix’s NetScaler web application delivery control (ADC) and NetScaler Gateway appliances. Historically, LockBit affiliates have conducted attacks against organizations of varying sizes across multiple critical infrastructure sectors—including education, energy, financial services, food and agriculture, government and emergency services, healthcare, manufacturing, and transportation. To understand LockBit in further detail, see the CISA’s threat report on LockBit.
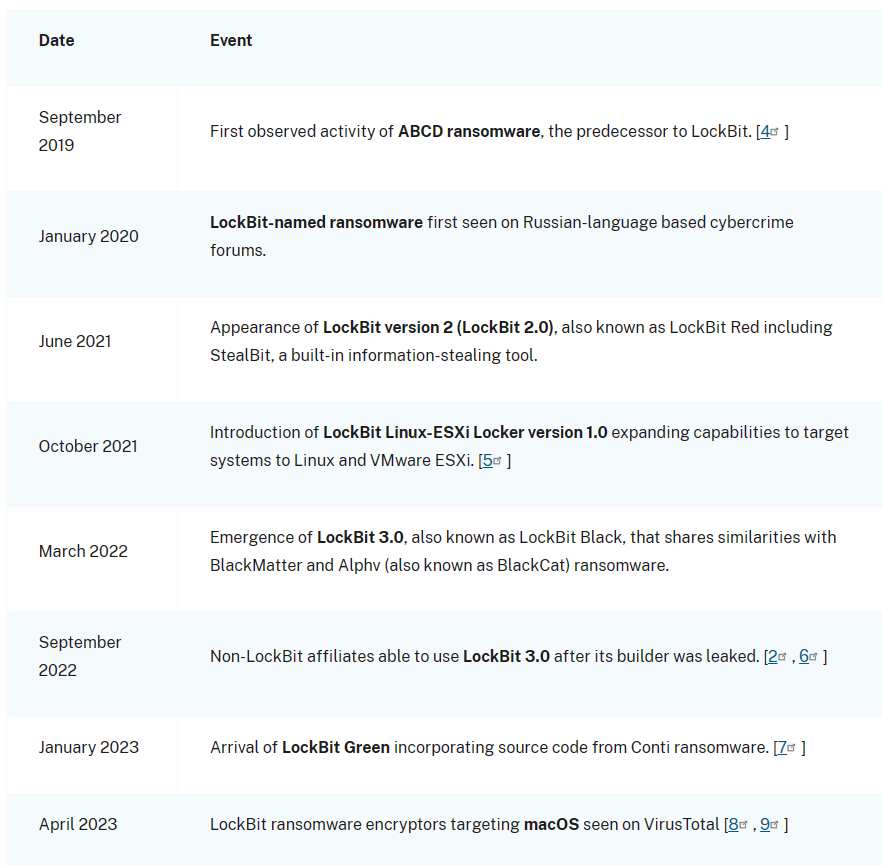
Figure: LockBit Evolution (Source: CISA)
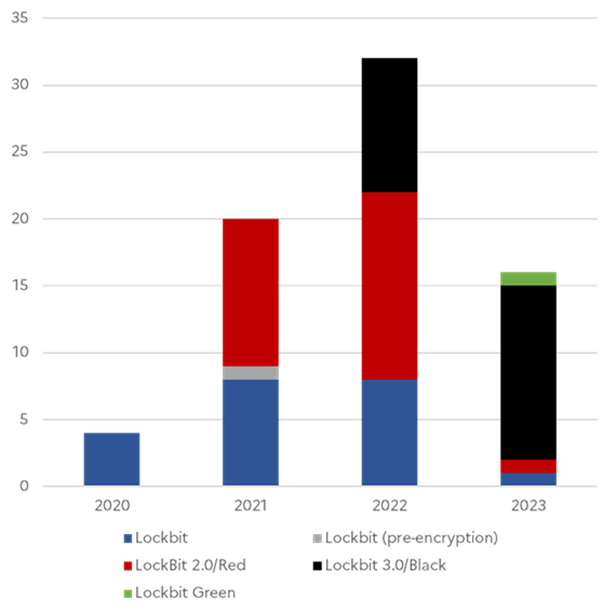
Figure: ANSSI-Observed LockBit Strains by Year (Source: CISA)
Figure: Alleged Number of Victims Worldwide on LockBit Leak Sites (Source: CISA)
The Advisory
The joint CSA provides tactics, techniques, and procedures (TTPs), as well as indicators of compromise (IOCs). If compromise is detected, the authoring organizations encourage network defenders to hunt for malicious activity on their networks using the detection methods and IOCs provided within the CSA and apply the incident response recommendations. Additionally, immediate application of publicly available patches is also recommended. For more information, visit the #StopRansomware website.
The Implications
The exploitation of the Citrix Bleed vulnerability by LockBit 3.0 ransomware affiliates and other threat actor groups poses a significant threat to organizations across various sectors. The joint advisory by CISA, FBI, MS-ISAC, and ASD’s ACSC underscores the importance of proactive cybersecurity measures in today’s digital landscape.
Organizations are encouraged to take immediate action by applying the recommended patches and using the provided detection methods and IOCs to hunt for potential compromises. By doing so, they can significantly enhance their cybersecurity posture and mitigate the risk of falling victim to ransomware attacks.
The joint advisory serves as a crucial reminder of the persistent and evolving cyber threats that organizations face today. It highlights the importance of maintaining robust cybersecurity practices and staying vigilant against potential threats. As the digital landscape continues to evolve, so too must our cybersecurity measures to protect against these ever-present threats. For more information on the Advisory, please refer to the original advisory on the CISA website.
How Can You Prevent LockBit Ransomware Attacks?
As the threat landscape continues to evolve, traditional security measures are often insufficient. You need a more comprehensive approach to cybersecurity that goes beyond perimeter defenses. This is where ThreatResponder by NetSecurity comes into play. ThreatResponder is an all-in-one, unified, cloud-native, machine learning-driven cyber-resilient endpoint security platform.
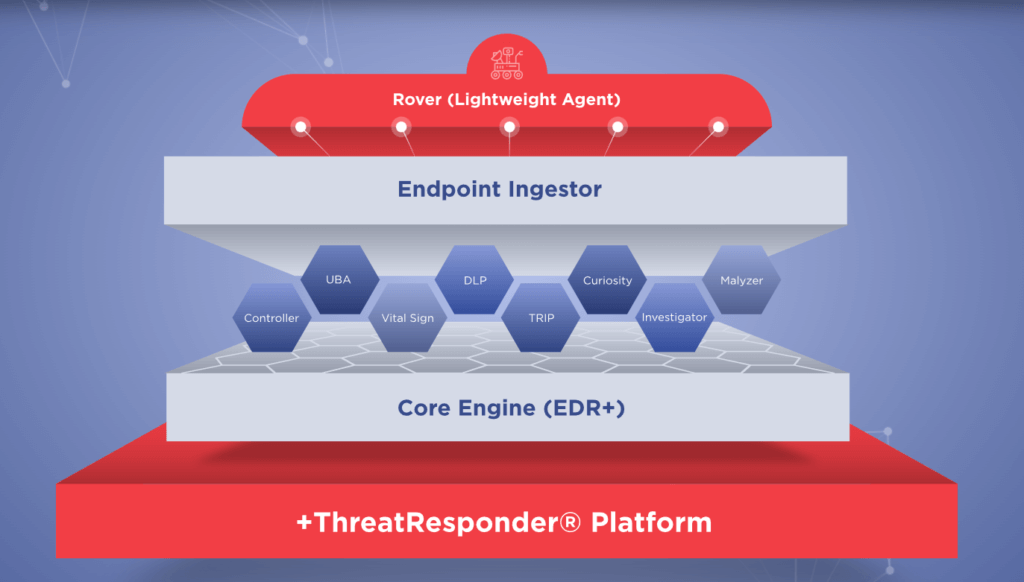
These pillars collectively create a formidable defense system against a wide range of cyber threats. However, in an ever-evolving digital world, there’s always room for improvement and expansion.
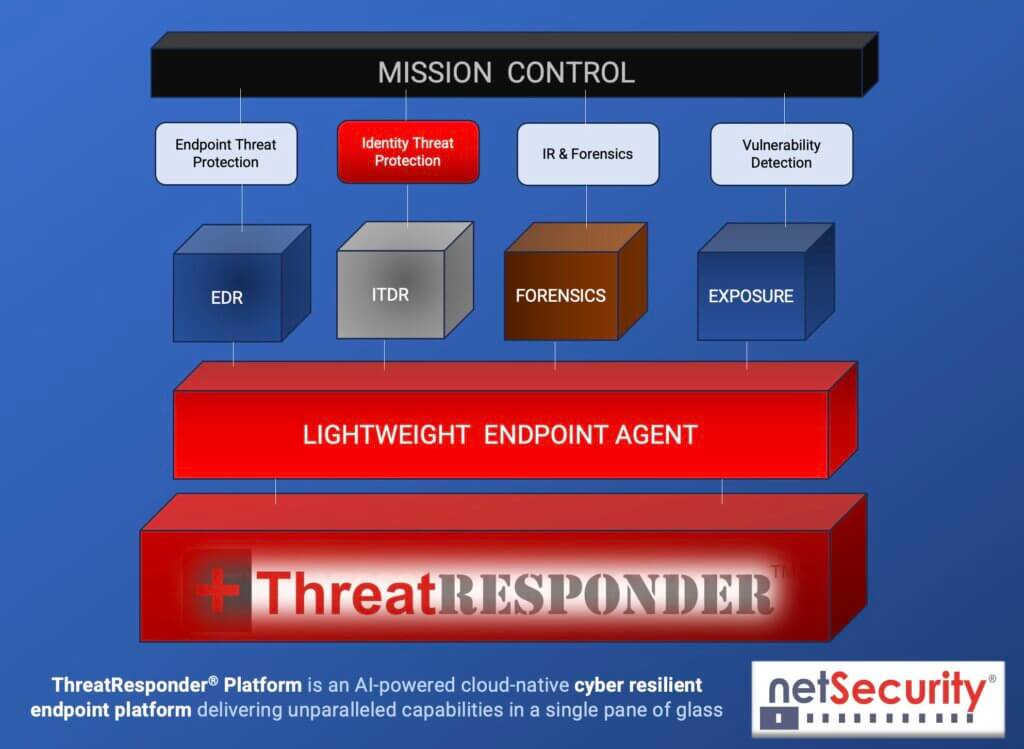
It is designed to provide cybersecurity teams with the necessary tools and insights to defend their organizations effectively. Let’s take a closer look at the core features of ThreatResponder:
Endpoint Detection and Response (EDR)
Endpoint Detection and Response is a critical component of modern cybersecurity. ThreatResponder continuously monitors endpoints (devices and servers) for signs of suspicious activities, such as malware infections or unusual behavior. When a threat is detected, ThreatResponder responds in real-time to mitigate the risk, making it an invaluable asset in threat containment and incident response.
Identity Threat Detection and Response
User identities are a prime target for attackers. ThreatResponder analyzes user behaviors and privileges to identify suspicious activities and potential threats. By understanding user identity and access patterns, it can detect unauthorized access and protect sensitive data from breaches.
Forensics
In the aftermath of a security incident, forensics play a crucial role in understanding the attack and its impact. ThreatResponder provides detailed forensic capabilities, helping CISOs and their teams analyze the scope of an incident, track the attacker’s movements, and collect evidence for potential legal action.
Threat Hunting
Proactive threat hunting is essential for identifying threats before they cause significant damage. ThreatResponder equips CISOs with advanced threat-hunting tools, enabling them to search for hidden threats, vulnerabilities, and indicators of compromise within their organization’s network.
Vulnerability Detection
Identifying and patching vulnerabilities is a fundamental part of cybersecurity. ThreatResponder helps CISOs stay on top of vulnerabilities within their organization’s systems and applications, allowing them to prioritize and address weaknesses before they are exploited by attackers.
The Advantages of a Unified Approach
One of the key strengths of ThreatResponder is its unified approach to cybersecurity. By consolidating multiple security functions into a single platform, CISOs can benefit from the following advantages:
- Simplified Management: Managing multiple cybersecurity solutions can be complex and time-consuming. ThreatResponder streamlines management, reducing the overhead associated with disparate security tools.
- Enhanced Visibility: A unified platform provides a holistic view of an organization’s security posture, allowing CISOs to better understand their threat landscape and take proactive measures.
- Improved Collaboration: ThreatResponder encourages cross-functional collaboration between security teams. It allows for the sharing of threat intelligence and coordinated incident response efforts.
- Cost Efficiency: Investing in a single platform that encompasses multiple security functions can be more cost-effective than purchasing and maintaining numerous individual solutions.
Try ThreatResponder for Free!
Are you ready to take the next step in defending your organization against cyber threats? Explore ThreatResponder by NetSecurity today and bolster your organization’s cybersecurity defenses.

Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).