How Clop Ransomware Exploited MoveIT (CVE-2023-34362) Vulnerability and How You Can Protect Your Organization?
In recent years, the digital landscape has witnessed a significant surge in ransomware attacks. Especially after the MoveIT vulnerability (CVE-2023-34362), data breaches shot up drastically, causing significant havoc and disruption to organizations worldwide. One name that is consistent in making the headlines by exploiting this vulnerability is Clop ransomware. In this article, we will understand what Clop ransomware is, its attack mechanisms, propagation techniques, entities it typically targets and how to protect your organization from Clop ransomware attacks.
What is Clop Ransomware and How do They Operate?
Clop is a variant of CryptoMix Ransomware that was first discovered in early 2019. It has leveraged a Ransomware as a Service (RaaS) and gained notoriety for its devastating consequences. It is leverages verified and digitally signed binary to exploit vulnerabilities and bypass system defenses. It is also tracked by various organization with different names. Other names for Clop ransomware are Lace Tempest, TA505 and FIN11. Clop is considered to be Pro-Russian group and targets organization that support Ukraine in the Russia-Ukraine war. In previous years, Clop has been on the sidelines while its competitors like LockBit and BlackBasta were leading and booming the ransomware space by breaching organization across US and Europe. As exploiting critical zero-day vulnerabilities and phishing attacks that allow remote access to the threat actors being the primary attack tactics of the group, since May 2023, when Progress Software Corporation announced the MoveIT zero-day vulnerability in its Managed File Transfer (MFT) software, Clop has been dominating the ransomware space. CL0P is known for its use of the ‘double extortion’ tactic of stealing and encrypting victim data, refusing to restore victim access and publishing exfiltrated data on Tor via the CL0P^_-LEAKS website. When CISA, FBI and federal agencies from five eye countries (US, UK, Canada, Australia, New Zealand) released a joint advisory about clop ransomware exploiting MoveIT vulnerability, Clop ransomware group started naming and shaming organizations that were breached by exploiting MoveIT vulnerability on its data leak site. Prior to MoveIt vulnerability, Clop ransomware also claimed responsibility for exploiting organizations by exploiting Accellion FTA Servers and GoAnywhere MFT (CVE-2023-0669) zero-day vulnerabilities that created a significant impact to organizations across North America and Europe.
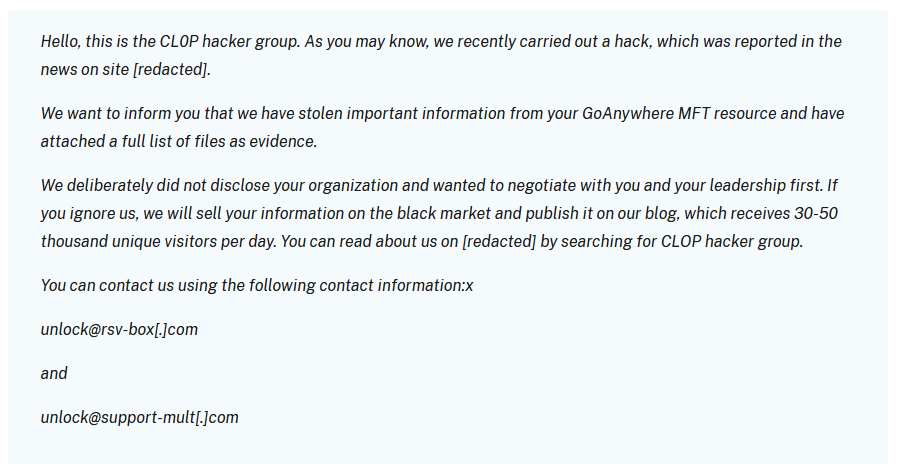
Figure 1. Clop Ransom Note – Source CISA
Clop Ransomware – Attack Methodology and Toolkit
CL0P’s toolkit contains several malware types to collect information, including the following:
- FlawedAmmyy/FlawedGrace remote access trojan (RAT) collects information and attempts to communicate with the Command and Control (C2) server to enable the download of additional malware components [T1071], [T1105].
- SDBot RAT propagates the infection, exploiting vulnerabilities and dropping copies of itself in removable drives and network shares [T1105]. It is also capable of propagating when shared though peer-to-peer (P2P) networks. SDBot is used as a backdoor [T1059.001] to enable other commands and functions to be executed in the compromised computer. This malware uses application shimming for persistence and to avoid detection [T1546.011].
- Truebot is a first-stage downloader module that can collect system information and take screenshots [T1113], developed and attributed to the Silence hacking group. After connecting to the C2 infrastructure, Truebot can be instructed to load shell code [T1055] or DLLs [T1574.002], download additional modules [T1129], run them, or delete itself [T1070]. In the case of TA505, Truebot has been used to download FlawedGrace or Cobalt Strike beacons.
- Cobalt Strike is used to expand network access after gaining access to the Active Directory (AD) server [T1018].
- DEWMODE is a web shell written in PHP designed to target Accellion FTA devices and interact with the underlying MySQL database and is used to steal data from the compromised device [1505.003].
- LEMURLOOT is a web shell written in C# designed to target the MOVEit Transfer platform. The web shell authenticates incoming http requests via a hard-coded password and can run commands that will download files from the MOVEit Transfer system, extract its Azure system settings, retrieve detailed record information, create, insert, or delete a particular user. When responding to the request, the web shell returns data in a gzip compressed format.
What is MoveIT Vulnerability and How Clop Ransomware Exploited MoveIT Vulnerability?
MOVEit is typically used to manage an organization’s file transfer operations and has a web application that supports MySQL, Microsoft SQL Server, and Azure SQL database engines. According to National Vulnerability Database (NVD), CVE-2023-34362 is defined as: “In Progress MOVEit Transfer before 2021.0.6 (13.0.6), 2021.1.4 (13.1.4), 2022.0.4 (14.0.4), 2022.1.5 (14.1.5), and 2023.0.1 (15.0.1), a SQL injection vulnerability has been found in the MOVEit Transfer web application that could allow an unauthenticated attacker to gain access to MOVEit Transfer’s database. Depending on the database engine being used (MySQL, Microsoft SQL Server, or Azure SQL), an attacker may be able to infer information about the structure and contents of the database, and execute SQL statements that alter or delete database elements. NOTE: this is exploited in the wild in May and June 2023; exploitation of unpatched systems can occur via HTTP or HTTPS. All versions (e.g., 2020.0 and 2019x) before the five explicitly mentioned versions are affected, including older unsupported versions.”
The MOVEit Transfer vulnerability, famously CVE-2023-34362, covers multiple flaws that an attacker can chain together to achieve RCE with elevated privileges. The first part of the exploit chain uses SQL injection to obtain a sysadmin API token. That token can then be used to call a deserialization function that does not properly validate input, allowing for remote code execution. A second vulnerability, CVE-2023-35036, was assigned and Progress Software released patches and an advisory addressing this issue. Patches for CVE-2023-35036 are meant to mitigate multiple parts of the successful exploit chain initially discovered to have been used during the exploitation of the first vulnerability, CVE-2023-34362. On June 15, 2023, another vulnerability was identified, CVE-2023-35708. Progress Software is in the process of releasing installable patches for this issue although DLL drop-ins.
On June 5, the Clop ransomware group made a public announcement through their Tor data leak site, taking accountability for the targeted attacks. They issued a severe warning, stating that if the victims failed to comply with their extortion demands, their data would be made public. The group set a deadline of June 14 for the affected parties to establish communication, failing which their company name would be exposed on the data leak site as a cautionary measure. Although no data has been released thus far, the group has initiated the practice of publicly identifying and shaming the companies that have fallen victim to their attacks.
Figure 2. Clop Ransomware Public Announcement
Clop Ransomware Indicators of Compromise (IOCs)
Here is a link to access the Indicators of Compromise related to Clop Ransomware: JSON Format, STIX Format
How to Prevent Clop Ransomware Attacks on Your Network?
In addition to having regular backups, implementing multifactor authentication, and disabling unused ports as recommended by CISA in its #StopRansomware advisory, implementing an advanced and sophesticated threat detection and prevention platform like ThreatResponder is necessasary.
NetSecurity’s ThreatResponder is a comprehensive, cloud-native endpoint protection and cyber resilient solution that provides organizations with an all-in-one solution for preventing most advanced ransomware attacks. Some of the key features of ThreatResponder include:
- Endpoint Security: ThreatResponder includes robust endpoint security capabilities that help protect against threats and prevent data loss.
- Threat Hunting: The solution includes a threat hunting capability that enables organizations to proactively search for and identify potential threats.
- Forensic Investigation: ThreatResponder provides a comprehensive forensic investigation capability thathelps organizations understand the root cause of a cyber attack and respond accordingly.
- Vulnerability Management: ThreatResponder includes a vulnerability management capability that helps organizations identify and remediate vulnerabilities in their systems.
- Real-Time Access to Endpoints: The solution provides real-time access to thousands of endpoints instantly, enabling organizations to quickly and effectively respond to cyber threats and contain them before the damage takes place.
- Threat Intelligence: ThreatResponder provides real-time threat intelligence that helps organizations stay ahead of the latest cyber threats.
In addition to these features, ThreatResponder also provides advanced analytics capabilities that help organizations quickly identify and respond to potential threats. The solution is designed to be easy to use, allowing organizations to quickly implement and start using it to prevent cyber attacks.

Want to try our ThreatResponder, cutting-edge Endpoint Detection & Response (EDR), and ThreatResponder FORENSICS, the Swiss knife for forensic investigators in action? Click on the below button to request a free demo of our NetSecurity’s ThreatResponder platform.
Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).