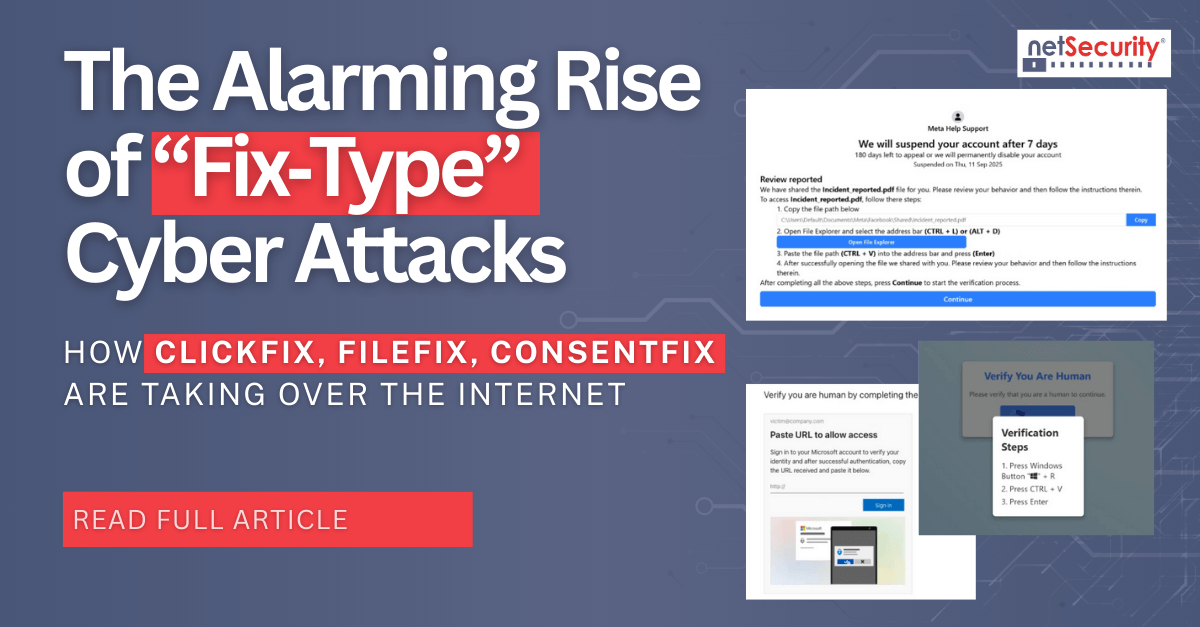

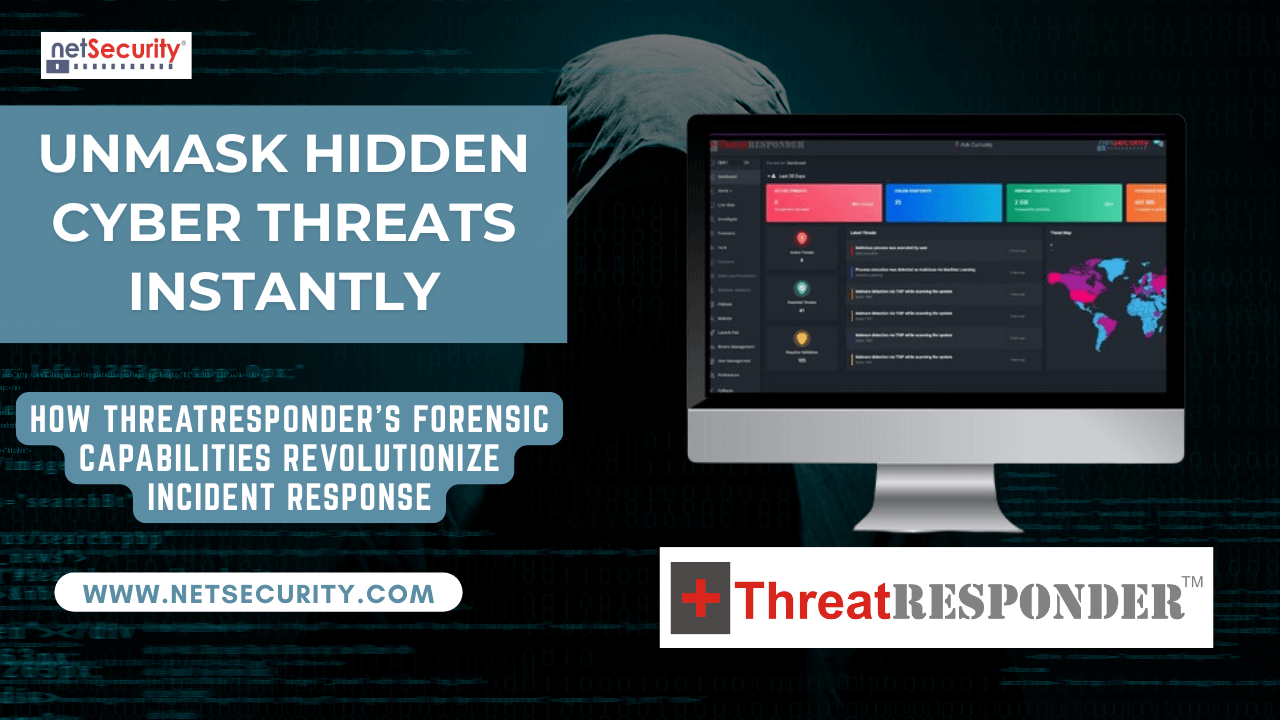


NetSecurity seeks professionals interested in becoming part of our company that creates ThreatResponder®, which is positioned to be the “next big thing” in cyber. We seek full-time employment or 1099 expert consultants with high regard for creativity and innovation. To begin the application process, please complete the form below.

Lorem ipsum dolor sit amet, consectetur adipiscing elit. Sed vulputate velit mi, non hendrerit justo varius ac. Cras gravida, dolor vel pulvinar tempus, erat massa facilisis tortor, in lobortis dui arcu at ligula. Nunc consequat arcu non lobortis eleifend. Vestibulum vel metus finibus, semper nunc nec, tristique felis. Donec auctor vestibulum sapien. Mauris tristique eget metus in vulputate. Etiam nec tempor odio. Praesent quis commodo metus, eu fringilla ipsum. Fusce quis aliquam mauris, vel sollicitudin ex. Praesent sed imperdiet sapien, vitae interdum turpis. Cras mollis nisi at lorem eleifend viverra at vitae est. Mauris luctus sem in arcu pharetra suscipit. Aliquam id eleifend elit, in ullamcorper neque. Nam gravida urna et ipsum fringilla lobortis. Vivamus eget fermentum purus. Duis est nulla, interdum sed iaculis eu, ultrices a arcu. Donec commodo, diam