LockBit 5.0 Resurface with Cross‑Platform Ransomware That Targets Windows, Linux, and ESXi
LockBit 5.0 has resurfaced as a hardened, cross‑platform ransomware family designed to disrupt heterogeneous enterprise estates at scale. Beyond simply updating an encryptor, this release aligns tooling, anti‑analysis, and operator ergonomics to enable affiliates to hit Windows, Linux, and VMware ESXi in the same campaign. The result is a refined kill chain: stealthier ingress, faster pre‑encryption suppression of defenses, and hypervisor‑level impact that magnifies downtime. For organizations that virtualize critical workloads, the LockBit 5.0 ransomware model raises the stakes; defenders must treat hypervisors as Tier‑0 and assume blast radius extends well beyond a single endpoint.
Why LockBit 5.0 Matters to Defenders
LockBit 5.0 ransomware isn’t a wholesale rewrite; it’s an aggressive evolution of a mature codebase that prioritizes evasion and speed. Its cross‑platform design lets affiliates pivot cleanly between operating systems without switching tradecraft, while shared behaviors like randomized extensions, log tampering, and locale checks complicate detection engineering. Critically, the ESXi encryptor targets virtual machine datastores, turning one compromised host into dozens of encrypted services. Combined with pre‑encryption service termination and telemetry blinding on Windows, LockBit 5.0 minimizes the window for responders and undercuts common containment patterns such as in‑fabric snapshots and same‑network backups.
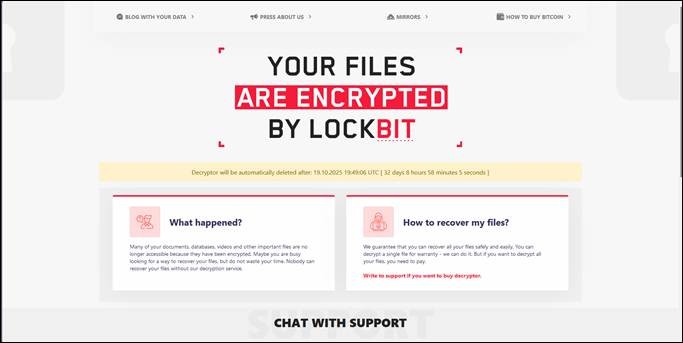
Figure: The leak site where link on the ransom note directs to when visited by victims | Source: TrendMicro
Windows Variant: Evasion, ETW Tampering, and Service Kill Chains
The Windows build of LockBit 5.0 emphasizes stealthy loading and telemetry degradation. Payloads are reflection‑loaded from memory, reducing reliance on disk artifacts and frustrating static inspection. Early in execution, the sample patches EtwEventWrite (e.g., short‑circuiting with a RET) to impair Event Tracing for Windows, thereby blinding security controls that depend on ETW providers. API calls are resolved dynamically at runtime to thwart signature matching and sandboxes keyed to known imports. Before encryption, the ransomware iterates through a hashed or obfuscated allowlist to terminate security tools, EDR agents, and backup services, stripping the host of self‑protection. Post‑encryption, it clears event logs to degrade forensics and timeline reconstruction. Encrypted files receive a randomized 16‑character extension, and execution logic includes locale and geo checks to avoid specific regions.
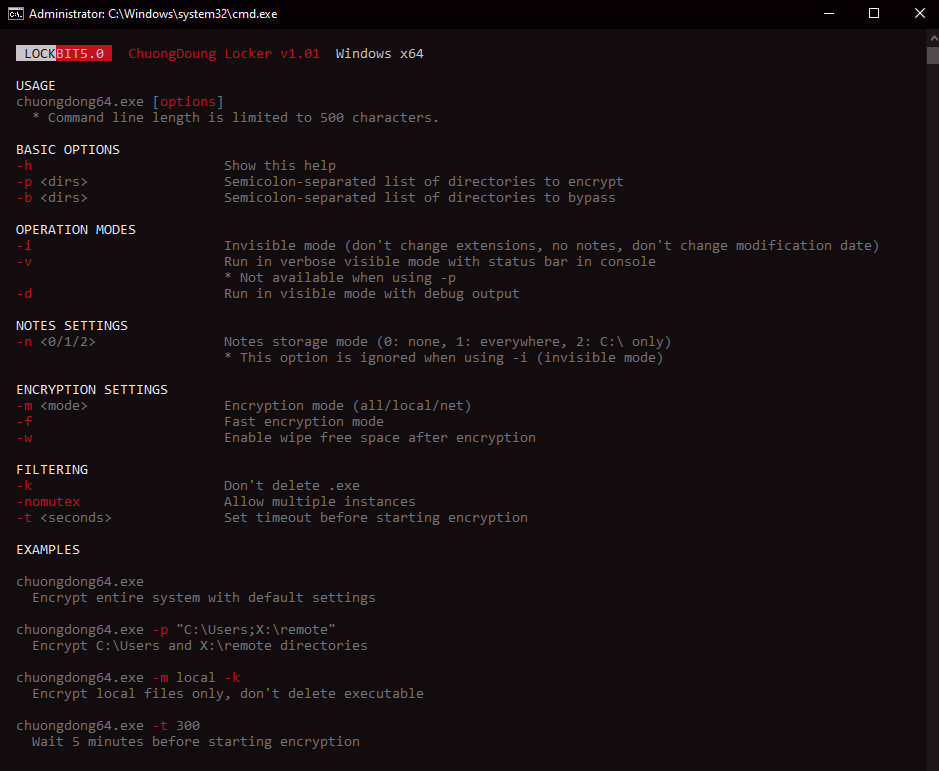
Figure: Help command shows the parameters and their respective uses | Image Source: TrendMicro
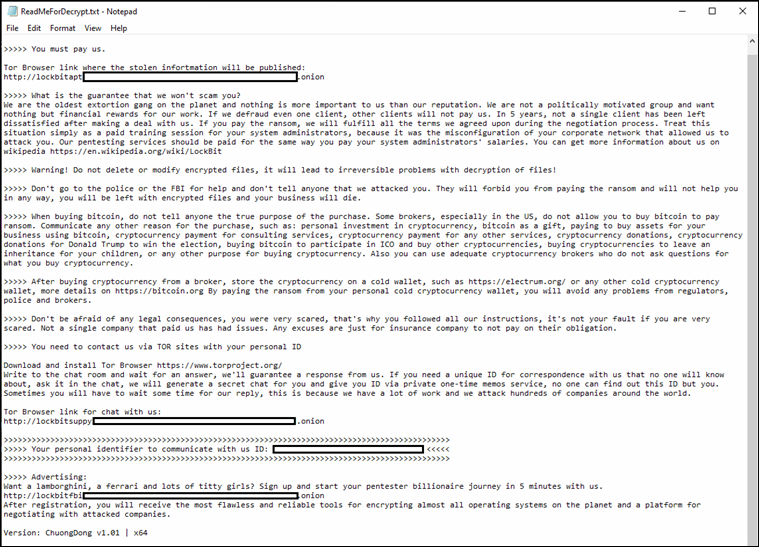
Figure: The ransom note generated by LockBit 5.0 | Image Source: TrendMicro
Linux Variant: Command‑Line Precision for Targeted Impact
The Linux variant exposes a consistent set of command‑line switches that let operators scope jobs with precision—include or exclude directories, filter by file types, and control logging verbosity. This lets affiliates balance speed versus noise: high‑value paths can be prioritized while noisy system locations are skipped, shortening dwell time. Execution feedback (e.g., which objects were processed or bypassed) enables hands‑on‑keyboard tuning mid‑operation. The Linux encryptor mirrors enough semantics from the Windows build to simplify operator training and scripting, lowering the barrier for affiliates to conduct cross‑platform LockBit 5.0 ransomware campaigns.
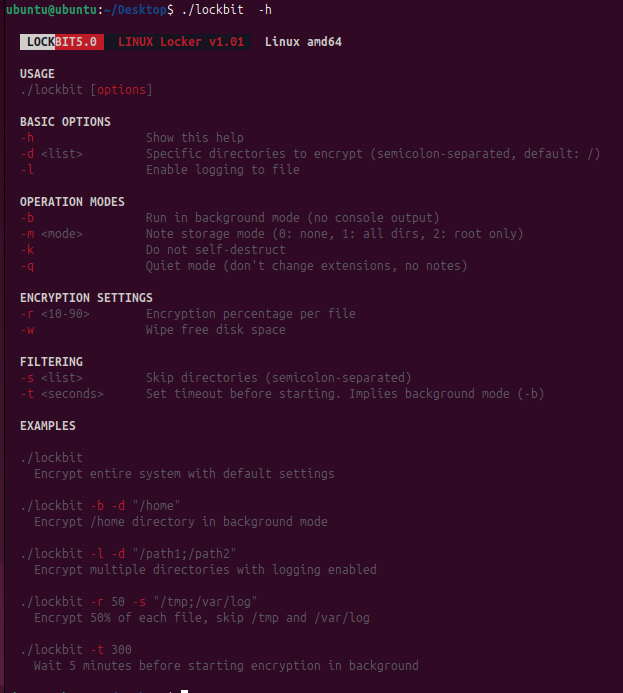
Figure: The LockBit 5.0 Linux version shows similar formatting of help options | Image Source: TrendMicro
ESXi Variant: Hypervisor‑Level Blast Radius
LockBit 5.0’s ESXi encryptor targets VMFS datastores and VM disk files, yielding outsized impact from a single foothold. Because one ESXi host often concentrates dozens of business services, encrypting at the hypervisor level collapses application tiers simultaneously. The variant prioritizes speed, minimizes interaction with management services that could tip detections, and presents CLI options that align with common vSphere operational patterns. For defenders, this breaks assumptions that VM‑centric snapshots and same‑fabric backups will be available during a ransomware event; once the datastore is encrypted, recovery hinges on immutable, off‑fabric backups and pre‑prepared rebuild automation.
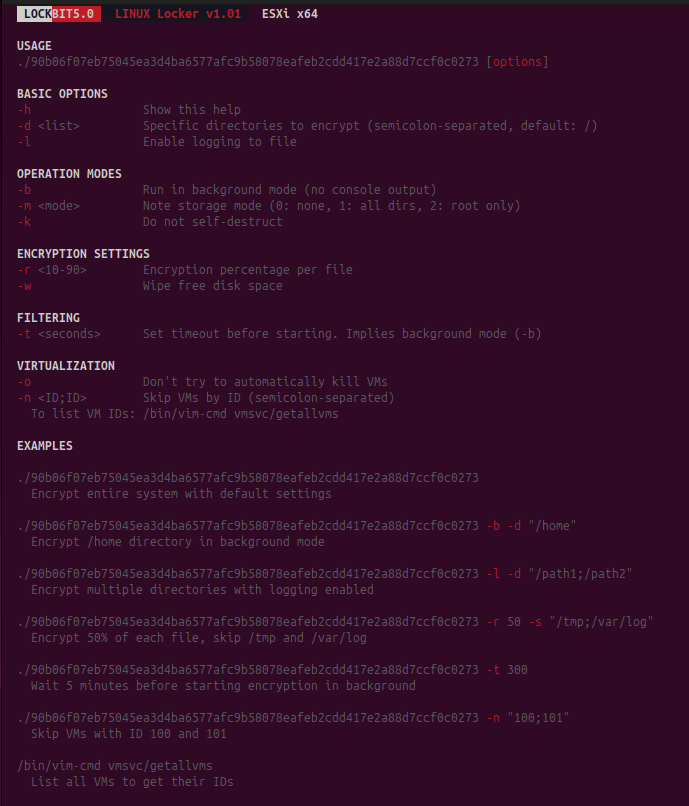
Figure: ESXi variant help command showing virtualization-specific parameters | Image Source: Trend Micro
RaaS Economics and Affiliate Operations
LockBit 5.0 ransomware continues the franchise’s Ransomware‑as‑a‑Service model. Core operators maintain encryptors, leak infrastructure, and negotiation workflows, while affiliates own initial access, privilege escalation, and lateral movement. The operator experience is tuned for speed: cleaner help menus, sensible defaults, and predictable CLI behavior across platforms. That ergonomics investment reduces affiliate errors during high‑pressure, post‑exploitation windows and increases the likelihood of rapid, multi‑platform encryption once a domain foothold is established.
Common Cross‑Platform Behaviors and Operator UX
LockBit 5.0 variants share key traits that defenders can align against: randomized 16‑character file extensions on encrypted content; post‑job event‑log manipulation; locale and geolocation checks; and structured, self‑documenting CLI usage that facilitates scripted deployment. Ransom notes and negotiation endpoints remain standardized, easing affiliate onboarding and maintaining brand continuity across LockBit 5.0 ransomware operations.
Initial Access and Lateral Movement Patterns
Affiliates commonly combine opportunistic perimeter exploitation with credential abuse. Typical routes include exposed RDP/VPN portals, weak or reused admin credentials, and unpatched internet‑facing services on hypervisor, backup, or management planes. Once inside, discovery focuses on AD, backup controllers, and vCenter/vSphere. Credential elevation leverages living‑off‑the‑land tooling, and lateral movement proceeds toward virtualization and storage tiers. Before detonating LockBit 5.0 ransomware payloads, operators aim to disable endpoint protection, corrupt or delete reachable backups, and schedule encryption to coincide with low‑staff windows.
Detection and Mitigation Priorities
1) Treat ESXi as Tier‑0
Isolate management networks; restrict vCenter/ESXi Shell/SSH; enforce MFA with phishing‑resistant factors; vault and rotate hypervisor credentials; apply vendor patches rapidly.
2) Harden Windows Telemetry Against ETW Tampering
Detect patching of EtwEventWrite and unusual ETW provider failures; rely on kernel‑mode sensors and non‑ETW corroboration where possible; baseline DLL integrity for critical providers.
3) Disrupt Pre‑Encryption Kill Chains
Alert on bulk service/driver termination targeting security and backup agents; monitor for hashed comparisons against service names; block tampering of backup processes and VSS.
4) Make Backups Immutable and Off‑Fabric
Use object‑lock/immutability and separate administrative domains; test restores under hypervisor‑outage conditions; automate bare‑metal and VM rebuild workflows.
5) Segment Administration and Enforce Least Privilege
Apply tiered admin models; separate workstation and server admin accounts; require just‑in‑time elevation; implement strong MFA for all remote access paths.
6) Hunt for Cross‑Platform TTPs
Search for discovery of backup, vSphere, and storage endpoints; enumerate anomalous use of hypervisor CLIs/APIs; look for rapid service disablement and coordinated encryption staging.
LockBit 5.0 IOCs:
Following are the Indicators of Compromise related to LockBit 5.0:
SHA256 7ea5afbc166c4e23498aa9747be81ceaf8dad90b8daa07a6e4644dc7c2277b82 180e93a091f8ab584a827da92c560c78f468c45f2539f73ab2deb308fb837b38 4dc06ecee904b9165fa699b026045c1b6408cc7061df3d2a7bc2b7b4f0879f4d 90b06f07eb75045ea3d4ba6577afc9b58078eafeb2cdd417e2a88d7ccf0c0273 98d8c7870c8e99ca6c8c25bb9ef79f71c25912fbb65698a9a6f22709b8ad34b6
ThreatResponder – All-in-One Platform To Prevent Advanced Ransomware Attacks
LockBit 5.0 ransomware represents a pragmatic but potent step forward: memory‑resident loading and ETW suppression on Windows, CLI‑driven precision on Linux, and hypervisor‑level disruption on ESXi. Its cross‑platform design compresses defender response time and challenges assumptions about in‑fabric resilience.
That’s where NetSecurity’s ThreatResponder changes the game. Unlike point solutions, ThreatResponder delivers an all-in-one platform that combines:
- EDR + ITDR — to detect endpoint and identity threats, including credential abuse that often follows perimeter compromises.
- Threat Hunting & Forensics — enabling security teams to investigate post-exploitation activity and uncover stealthy ransomware behaviors.
- Integrated Vulnerability Management — giving CISOs visibility into exposed assets and missing patches before attackers exploit them.
- Threat Intelligence Feeds — enriched with global insights on adversary tactics, techniques, and procedures used by ransomware groups like LockBit 5.0.
With ThreatResponder, organizations gain unified visibility, proactive detection, and automated response to stop advanced ransomware attacks before they cause damage.
Disclaimer