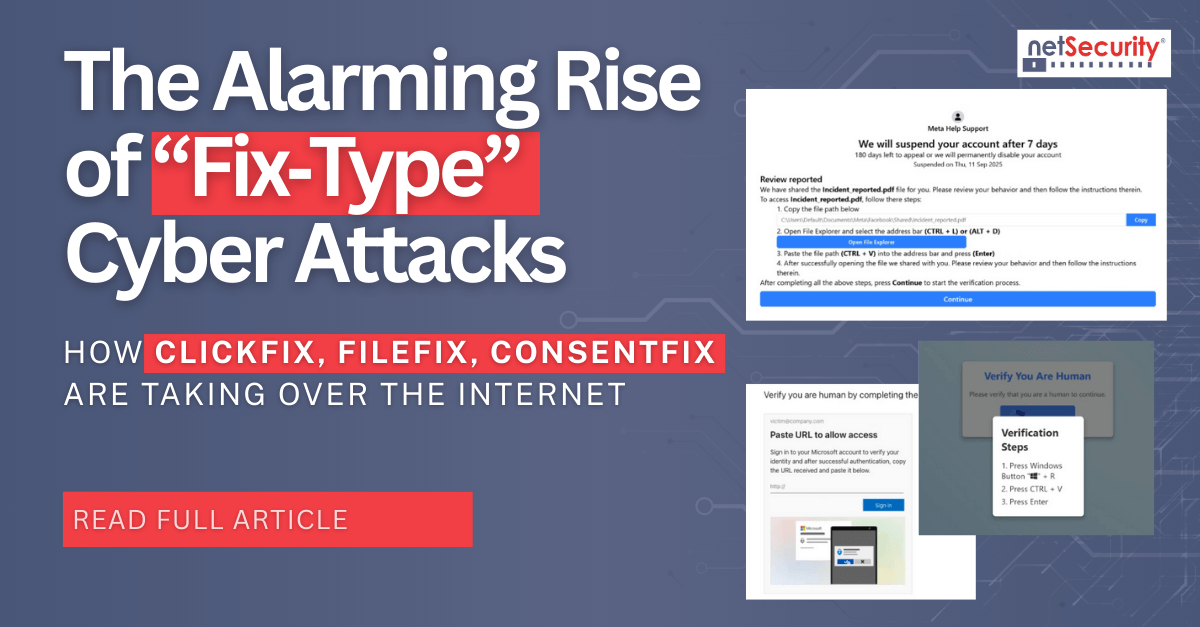
New VoidLink Malware: A Cloud‑Native, Modular Linux Framework Built for Stealth
VoidLink is the latest malware that has captured the headlines with it novel stealthy techniques. In this article, let’s deep dive into what is VoidLink, its capabilities, techniques and IOCs. So let’s dive in.
What is VoidLink?
VoidLink is a cloud native advanced Linux malware framework designed for long term, stealthy access. It blends custom loaders, a core implant, kernel and user mode rootkits, and an extensive in memory plugin system. The framework profiles its environment, adapts behavior to reduce detection, and persists across modern cloud and container deployments. Its architecture and operator console enable tailored implants, runtime configuration, and rapid post exploitation workflows.
Architecture overview
VoidLink arrives via a two stage loader that delivers a stable core implant. The core manages global state, task execution, and encrypted communications while supporting on demand delivery of additional capabilities as plugins. The result is a full command and control agent rather than a single purpose backdoor. The design favors modularity, allowing capabilities to be swapped or extended without rebuilding the implant.
Cloud and container awareness
Upon initialization, the implant detects whether it is running on a major cloud provider and whether it resides inside Docker or a Kubernetes pod. It queries instance metadata where available and builds an accurate profile of the host and its orchestration context. This information guides post exploitation choices such as secret extraction from container runtimes, container escape checks, and lateral movement tailored to clustered environments.
Plugin API and in memory modules
A custom Plugin API exposes file I O, socket creation, process execution, symbol resolution, and C2 logging. Plugins are delivered as ELF object files and are loaded directly into memory to minimize artifacts. API calls use direct syscalls to bypass common user space hooks. This approach mirrors well known BOF style extensibility without relying on external tooling and enables rapid expansion of functionality during an operation.
Rootkit package and concealment
VoidLink includes multiple concealment strategies and selects one based on kernel features:
- LD_PRELOAD for user space hiding when kernel mode is unavailable or on very old kernels
- Loadable Kernel Module for kernels that allow it
- eBPF based hooks for newer locked down systems
These components hide processes, files, network sockets, and the presence of the rootkit modules themselves. A host behavior monitor learns CPU, memory, network, and process patterns to time activity and beaconing for low visibility intervals such as off hours.
Communications and VoidStream protocol
Command and control uses an encrypted messaging layer named VoidStream. Supported transports include HTTP 1.1, HTTP 2, WebSocket, DNS, and ICMP. Requests are camouflaged to resemble normal web or API traffic, and file exfiltration can be wrapped in content that looks like common web assets such as JS, CSS, or HTML, or embedded into PNG like blobs. Samples also include early support for mesh style C2 that allows infected machines to relay messages for peers when direct outbound access is limited.
Adaptive evasion and risk scoring
At startup, the implant inventories host security controls and kernel hardening. It computes a risk score and suggests an evasion posture that other modules honor. For example, port scans slow down under heavy monitoring and beacon intervals stretch to reduce anomalies. This adaptive model is applied consistently across discovery, lateral movement, and exfiltration steps.
Anti analysis and anti forensics
VoidLink implements anti debugging and runtime integrity checks to detect hooks or patching. Sensitive code regions can be decrypted just in time and re encrypted while idle to frustrate memory scanners. On tamper detection, the implant self deletes and triggers anti forensic routines that remove command histories, login records, system logs, and dropped files, overwriting data with random bytes to prevent recovery.
Operator dashboard and builder
Operators manage agents, tasks, files, and plugins through a web based dashboard. The interface groups the mission flow into agent management, terminal access, implant builder, reconnaissance, credentials, persistence, lateral movement, process injection, stealth, and evidence wiping. A builder panel generates customized implant variants and lets operators tune operational parameters such as heartbeat cadence and evasion posture. Most settings can also be adjusted at runtime.
Default plugin categories
VoidLink ships with dozens of plugins organized by function:
- Reconnaissance: system and environment profiling, user and group enumeration, process and service discovery, filesystem and mount mapping, and local network topology.
- Cloud and containers: discovery for container platforms, privilege escalation helpers, container escape checks, and misconfiguration probes that enable host breakout or cluster traversal.
- Credential harvesting: SSH keys, Git and local password material, browser credentials and cookies, environment variable secrets, process argument tokens, and items stored in the system keyring.
- Utilities and lateral movement: file management, interactive and non interactive shells, port forwarding and tunneling, and an SSH based worm that attempts to spread to known hosts.
- Persistence: cron jobs, systemd services, and dynamic linker abuse via LD_PRELOAD.
- Anti forensics: log wiping, selective shell history removal, and timestomping to disrupt incident timelines.
Indicators of compromise
Sample hashes published with early stages and implants can aid triage and hunting:
70aa5b3516d331e9d1876f3b8994fc8c18e2b1b9f15096e6c790de8cdadb3fc9
13025f83ee515b299632d267f94b37c71115b22447a0425ac7baed4bf60b95cd
Key Takeaways
- Prioritize telemetry for cloud metadata queries, container discovery and escape checks, and unusual access to orchestration interfaces.
- Hunt for LD_PRELOAD persistence patterns, anomalous eBPF activity, and unsigned or unexpected kernel modules.
- Inspect Linux hosts for adaptive timing of outbound traffic, especially HTTP requests that mimic site assets or API calls.
- Monitor for rapid creation of in memory mapped ELF objects and syscalls consistent with plugin loading and direct syscall use.
- Protect developer and administrative workstations that bridge to cloud environments since default plugins target SSH keys, local keyrings, browser stores, and environment variables.
- Treat anti forensic behavior as a high severity signal, including selective log wiping, shell history tampering, and timestomping.
NetSecurity will continue to track VoidLink’s evolution and update detections, response playbooks, and hardening guidance for Linux, container, and cloud workloads. With ThreatResponder, organizations gain unified visibility, proactive detection, and automated response to stop advanced ransomware attacks before they cause damage.

Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).