Unmask Hidden Cyber Threats Instantly: How ThreatResponder’s Forensic Capabilities Revolutionize Incident Response
Why Forensic Investigation Is Critical for Modern Cybersecurity
Cyber breaches are no longer rare events. Studies show that the average time to detect a breach exceeds 200 days, giving attackers ample time to steal sensitive data and escalate privileges. Manual forensic investigations are slow, resource-heavy, and prone to human error. Organizations need a solution that is fast, accurate, and automated. ThreatResponder delivers exactly that.
What Makes ThreatResponder Forensics Unique
ThreatResponder’s forensic module is designed to streamline and automate the entire investigation process. From configuration to artifact selection, every step is optimized for efficiency and precision.
Configuration Made Simple
Step 1: Define Investigation Parameters
The forensic process begins with an intuitive configuration interface. Users can:
- Select Scan Type (Online or Offline)
- Assign an Investigation Name and Description
- Choose Operating System Platform (Windows, Linux, macOS)
- Set Scan Priority for faster results
- Enable Real-Time Event Collection for dynamic investigations
- Define Time Interval and Time Zone for targeted analysis
This flexibility ensures investigations are tailored to organizational needs.
Step 2: Choose Endpoints
ThreatResponder allows security teams to select specific endpoints or groups of endpoints for investigation. This targeted approach minimizes resource usage while maximizing forensic depth.
Step 3: Select Artifacts for Deep Analysis
Artifacts are the digital footprints attackers leave behind. ThreatResponder enables users to select from a wide range of artifacts, including:
- File Changes and Access Evidence
- Deleted Files
- Event Logs
- Browser Downloads
- Registry Entries
- Prefetch Files
- Mapped Network Drives
- Shortcut (.lnk) Files
- Recent Documents
Users can also configure hash calculations (MD5, SHA1, SHA256, SHA512) and specify file types such as:
- Document Files (.docx, .xls)
- Known Ransomware Extensions
- Image, Video, and Audio Files
- Archive Files (.zip, .rar)
This granular control ensures no detail is overlooked during the investigation.
Step 4: Enhance Detection Accuracy
ThreatResponder allows the application of custom rules and indicators to detect anomalies, suspicious patterns, and known threat signatures including deploying YARA rules. This proactive approach improves detection accuracy and reduces false positives.
Step 5: Get Actionable Insights
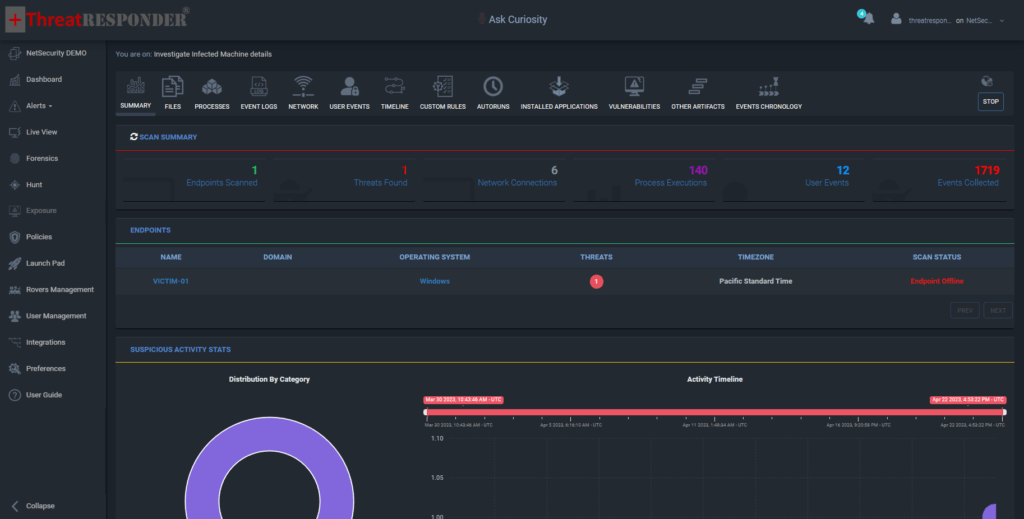
Once all parameters are set, ThreatResponder performs an automated forensic investigation, analyzing selected artifacts and correlating data to identify:
- Hidden malware infections
- Advanced persistent threats (APTs)
- Unauthorized file modifications
- Suspicious user activities
- Indicators of compromise (IOCs)
The results are compiled into a detailed forensic report, providing actionable insights for remediation and future prevention.
Key Benefits of ThreatResponder Forensics
Speed and Efficiency
Time is critical during a cybersecurity incident. ThreatResponder’s automated forensic processes drastically reduce investigation time compared to traditional manual methods. Instead of spending hours or even days collecting and analyzing artifacts, ThreatResponder completes these tasks in minutes. This rapid turnaround enables security teams to respond to threats immediately, minimizing potential damage and downtime.
Accuracy
Human error is one of the biggest challenges in manual forensic investigations. ThreatResponder leverages advanced algorithms and intelligent automation to ensure precise data collection and analysis. By eliminating guesswork and standardizing processes, the platform delivers highly accurate results, reducing false positives and ensuring that security teams focus only on genuine threats.
Comprehensive Coverage
Cyber attackers leave traces across multiple layers of an endpoint, from file systems to registry entries and network connections. ThreatResponder provides complete visibility by analyzing a wide range of artifacts, including deleted files, event logs, browser downloads, and mapped network drives. This holistic approach ensures that no suspicious activity goes unnoticed, giving organizations confidence in their forensic investigations.
Scalability
Modern enterprises often manage thousands of endpoints across diverse environments. ThreatResponder is built to scale effortlessly, allowing simultaneous investigations on multiple endpoints without compromising performance. Whether you are investigating a single workstation or an entire network, ThreatResponder delivers consistent speed and accuracy at any scale.
Proactive Threat Hunting
ThreatResponder is not just a reactive tool; it empowers organizations to hunt for threats proactively. By applying custom rules, indicators of compromise (IOCs), and advanced detection techniques, security teams can identify hidden infections, ransomware, and advanced persistent threats before they escalate into full-blown breaches. This proactive approach strengthens overall security posture and reduces the risk of costly incidents.
In an era where cyber threats are becoming more sophisticated, relying on traditional methods is a recipe for disaster. ThreatResponder’s forensic capabilities empower security teams to detect, analyze, and respond to threats faster than ever before, ensuring business continuity and compliance. Do not wait for a breach to expose your vulnerabilities. Contact NetSecurity today to learn how ThreatResponder can transform your incident response strategy and keep your organization secure.
Disclaimer
The page’s content shall be deemed proprietary and privileged information of NETSECURITY CORPORATION. It shall be noted that NETSECURITY CORPORATION copyrights the contents of this page. Any violation/misuse/unauthorized use of this content “as is” or “modified” shall be considered illegal and subjected to articles and provisions that have been stipulated in the General Data Protection Regulation (GDPR) and Personal Data Protection Law (PDPL).