ClickFix: The New Social Engineering Trick Hackers Are Using To Infect Organizations
If you thought phishing was just about shady links in emails, think again. A new technique called ClickFix is making waves in the cybercrime world—and not in a good way. It’s clever, sneaky, and it’s growing fast. In fact, security researchers have seen a 500%+ spike in ClickFix attacks in 2025.
So, what makes this technique different? Instead of tricking you into clicking a bad link, ClickFix tricks you into running the bad command yourself. That’s right—you become the attacker’s accomplice without even realizing it.
Let’s break down how it works, why it’s so effective, and most importantly, how you can protect yourself and your organization.
What Is ClickFix?
ClickFix is a social engineering attack. Instead of exploiting a software bug, it exploits you.
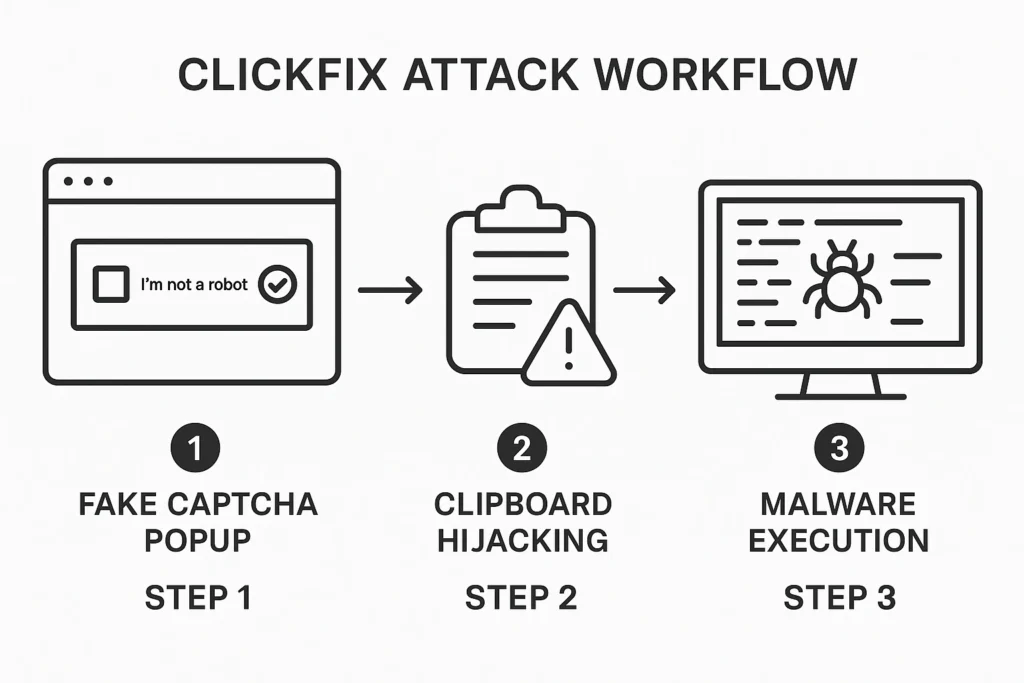
Figure: ClickFix Attack Workflow | Source: Cybersecurity News
Here’s how ClickFix Attacks work:
- You visit a website that is infected with ClickFix and you see a fake error message popup.
- It tells you to “fix” the problem by running a command in Windows Run, PowerShell, or Terminal.
- You copy-paste the command, thinking you’re solving the issue.
- In reality, you just installed malware like Lumma Stealer, DarkGate, or NetSupport RAT.
Because you ran the command yourself, your antivirus often doesn’t flag it. That’s what makes ClickFix so dangerous.
Here is a detailed step-by-step Breakdown of ClickFix Social Engineering Attack:
- The Lure
- Fake browser update pop-up
- “Verify you’re human” CAPTCHA
- “System error—run this command to fix”
- The Hook
- Uses urgency (“Do this now or lose data”)
- Uses authority (pretends to be Microsoft, Google, or IT support)
- Uses familiarity (CAPTCHAs and error messages look real)
- The Execution
- You paste a command into Run or PowerShell.
- The command silently downloads malware.
- The Damage
- Stolen passwords, cookies, and financial info
- Remote access trojans (RATs) for full control
- Lateral movement across networks
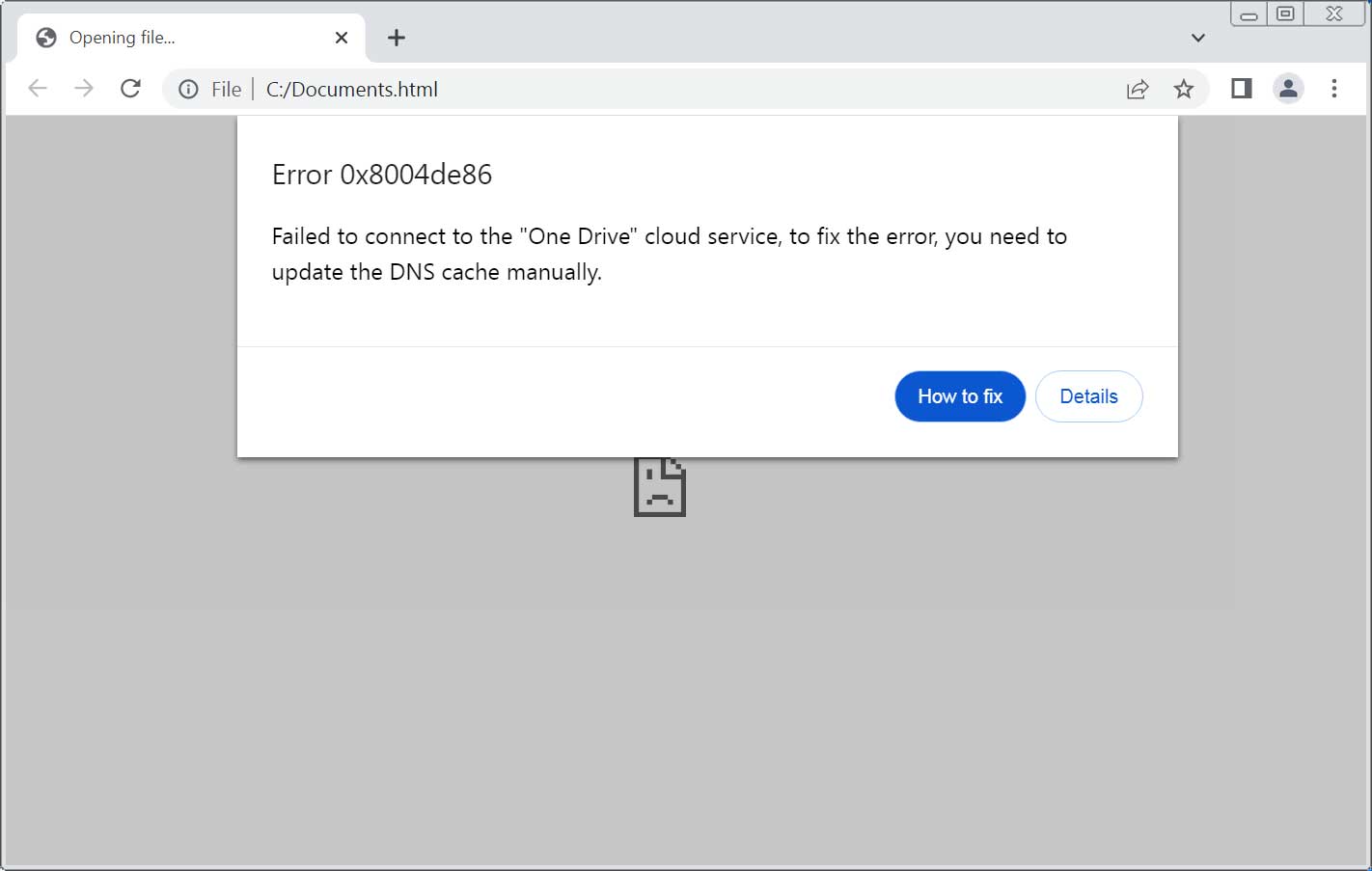
Figure: ClickFix phishing attachment | Source: Bleeping Computer
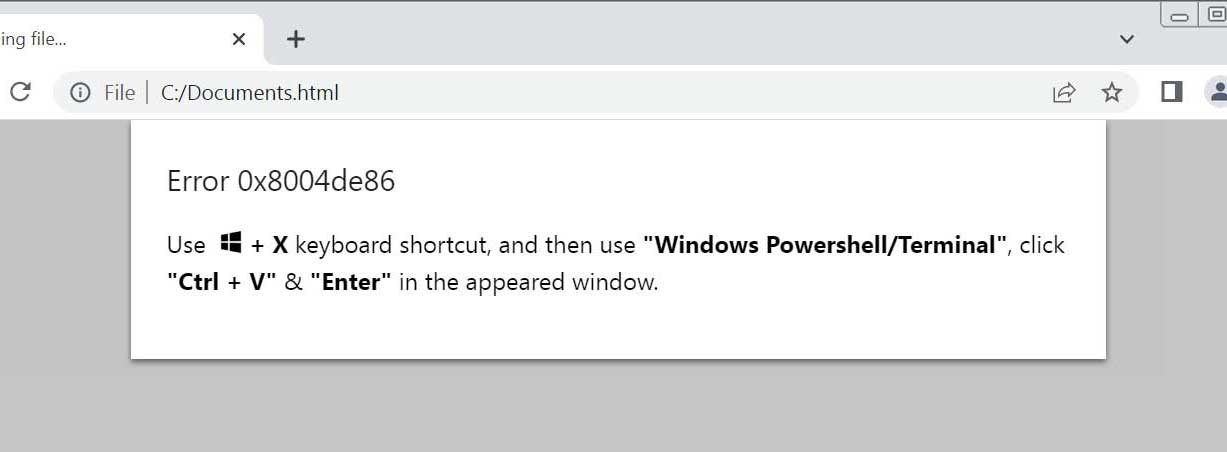
Figure: ClickFix phishing attachment – “How To Fix” Trap | Source: Bleeping Computer
Why It Works So Well in Tricking Users?
- It bypasses defenses: Security tools see you running the command.
- It feels normal: We’re used to fixing errors ourselves.
- It uses trusted tools: PowerShell and Run are built into Windows.
- It’s backed by big players: Nation-state groups like APT28 and Kimsuky are already using it.
Which Threat Groups Use ClickFix Attacks?
State-Sponsored Operations:
According to recent reports, ClickFix social engineering attacks have surged by 517% in the past six months, becoming the second most common vector behind only phishing. Following are some of the state-sponsored threat actors that leverage ClickFix attacks for initial access to the target network:
- Russian APT28: Utilized ClickFix in campaigns targeting Ukrainian government entities, distributing Lucky Volunteer information stealer through fake document sharing notifications.
- North Korean Kimsuky: Posed as Japanese diplomats in conversation-based social engineering, eventually directing targets to ClickFix-enabled sites deploying Quasar RAT.
- Iranian MuddyWater: Incorporated ClickFix into broader espionage campaigns targeting critical infrastructure.
Malware Payload Diversity:
ClickFix campaigns have successfully delivered:
-
- Information Stealers: Lumma Stealer, SnakeStealer, RedLine Stealer, and Vidar Stealer for credential harvesting.
- Remote Access Trojans: NetSupport RAT, AsyncRAT, DarkGate, and SectopRAT for persistent system control.
- Banking Malware: DanaBot for financial fraud operations.
- Ransomware: Interlock ransomware group adopted ClickFix for initial access in corporate environments.
- Post-Exploitation Tools: Havoc C2 framework for advanced persistent threat activities.
.webp)
Figure: ClickFix Malware Attack Campaigns | Source: Cybersecurity News
How NetSecurity’s ThreatResponder Helps Stop ClickFix Attacks
While awareness and good cyber hygiene are critical, organizations need a powerful security platform to detect and stop ClickFix before it causes damage. That’s where NetSecurity’s ThreatResponder® comes in.
ThreatResponder is designed to see what others miss—especially attacks like ClickFix that rely on human error and trusted system tools. Here’s how it helps:
Advanced Threat Detection
- Behavioral Analysis: ThreatResponder doesn’t just look for known malware signatures. It monitors unusual activity—like suspicious PowerShell or Run commands—that often signal a ClickFix attempt.
- Real-Time Alerts: Security teams are notified instantly when risky commands are executed, reducing attacker dwell time.
Endpoint Protection & Response
- Endpoint Visibility: ThreatResponder gives full visibility into what’s happening on every endpoint, so hidden ClickFix payloads can’t lurk undetected.
- Automated Response: Malicious processes can be isolated or killed automatically, stopping the attack in its tracks.
Threat Intelligence Integration
- In-Built VirusTotal: ThreatResponder integrates with up-to-date threat intelligence, ensuring it recognizes the latest ClickFix campaigns and malware families like Lumma Stealer or DarkGate.
- Contextual Insights: Security teams get detailed forensic data to understand how the attack unfolded and prevent recurrence.
User & Insider Risk Monitoring
- Command Monitoring: If a user is tricked into running a suspicious command, ThreatResponder flags it immediately.
- Policy Enforcement: Organizations can restrict risky tools (like unrestricted PowerShell) through ThreatResponder’s policy controls.
Rapid Incident Response
- One-Click Containment: Infected endpoints can be quarantined remotely, preventing lateral movement.
- Forensic Investigation: ThreatResponder provides deep visibility into attacker tactics, techniques, and procedures (TTPs), helping teams learn and adapt.
Why ThreatResponder is the Right Defense Against ClickFix
ClickFix thrives on stealth and speed, convincing users to act quickly before they think. ThreatResponder counters this by:
- Watching every endpoint in real time
- Detecting suspicious command execution instantly
- Automating containment before attackers can spread
- Giving security teams the intelligence they need to respond decisively
With ThreatResponder, organizations don’t just rely on users to “spot the phish.” They gain a safety net that catches what slips through and in the case of ClickFix, that can mean the difference between a minor scare and a major breach. With NetSecurity’s ThreatResponder, you can stay one step ahead, protect your users, and shut down these attacks before they take root.