Solutions to Stay Ahead of the Adversaries
NetSecurity full-stack cyber security solutions allow you to protect your critical assets and comply with regulatory requirements

Cyber Strategy & Program Development
Institute a cyber security strategy, implement a framework, measure your state, develop a strategic roadmap, and mature your security program

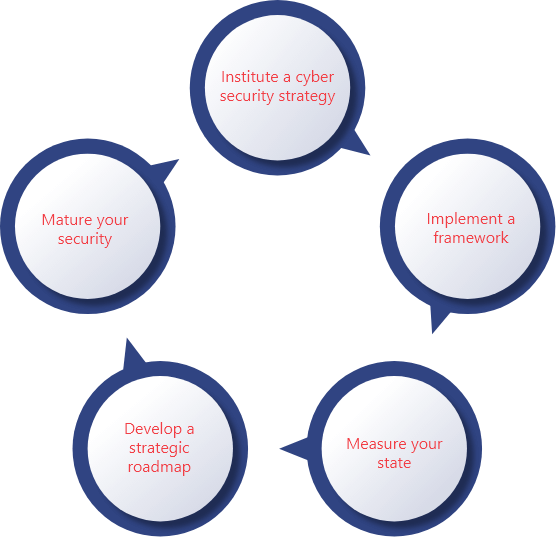
A cyber strategy and a sound security program are necessary to reduce enterprise information technology risks and cyber attacks
Security Policy Development:
Are your plans to protect your corporate assets clearly documented, understood, and implemented across your organization? NetSecurity will work with you to understand your business requirements and to evaluate the effectiveness of your existing security policies, standards, guidelines, and procedures. NetSecurity can work with you to establish security processes that support business goals and objectives.
Security Program / Roadmap Development
Do you have a sound security program? What direction is your security program heading? To answer these questions, we review your program or help to implement one that incorporates: governance; compliance and audits; risk management; incident response; data loss prevention; disaster recovery and contingency planning; training and awareness; supply-chain (third-party) management; cloud service providers; security engineering; and security operations. We apply our lifecycle approach to cyber security to fortify your security program.
NetSecurity experts help you establish a security maturity level and formulate a security roadmap. We assess or measure the effectiveness of your cyber security program in critical areas.
Our cyber forensic investigators work with your team to ensure that your organization has adequate preparation to conduct a digital investigation should one be needed. We help you develop incident response playbooks based on your unique environment, which ensures that you recover from a data breach or business interruption. NetSecurity’s cyber forensic investigators also help with pre-breach planning as well as provide support in conducting incident or breach response rehearsal, simulation, table-top, and training exercises.

Security Engineering & Operations

Security experts agree that a defense-in-depth approach to executing security strategies that meet business goals is the best solution to risk mitigation. NetSecurity’s approach ensures that no single technology or solution is relied on to provide adequate security. NetSecurity will work closely with your organization to clearly understand your business and technical requirements. We support the collection, review, correlation, and analysis of events and logs from infrastructure assets, which allows us to conduct cyber threat hunting across these assets to find the “needle in the haystack.” Our consultants review current security controls in order to gauge effectiveness of these controls to recommend and implement solutions that meet your business requirements. With our in-depth hands-on cyber expertise, NetSecurity’s consultants assist you by providing security solutions in the different information technology areas including cloud operations, Internet of Things (IoT), embedded systems, web/mobile applications, network, wireless, and endpoint security.
Security Assessments
Identify your enterprise risks and prioritize your mitigation strategy
Penetration Testing & Red Team Exercises
Vulnerability Assessment
Risk Assessment
Compromise Assessment

Penetration Testing &
Red Team Exercises
Simulating sophisticated adversaries to identify your risks
NetSecurity is an adversary simulation and network penetration testing company that is trusted by both Government and commercial entities. We help you uncover enterprise risks through advanced adversarial threat simulation against people, technology, and processes. Measuring how well your security infrastructure will perform against today’s most advanced threats is vital to the success of your cyber security program. NetSecurity will assist you in identifying the threats faced by your information assets so that you can quantify your threats and mitigate risk appropriately. Our depth of expertise includes network, wireless, web/mobile applications, cloud, IoT, ICS/SCADA, and social engineering testing.
Through our penetration testing and red teaming exercises, we provide you with a detailed understanding of the exposure to vulnerabilities that your information assets face. We then identify most vulnerabilities and focus on areas in which a compromise would have the greatest risk to your business. As a network penetration testing company, NetSecurity simulates or emulates cyber adversaries’ tools, tactics, and procedures (TTPs), which allows you to identify your security weaknesses and mitigate the risks faced by your enterprise before your network is targeted.
Our consultants use the same tools and techniques used by hackers and the most-determined adversaries to identify and validate security vulnerabilities of your environment. We systematically analyze this data to determine the level of risk associated with these vulnerabilities and to provide prioritized recommendations to help you mitigate risk to achieve your information security objectives.
NetSecurity’s network and web application penetration testing methodology uses standards specified in the Open Source Security Testing Methodology Manual (OSSTMM), Open Web Application Security Project (OWASP), and NIST Security Testing Standards. Using these standards as a base, we tailor our methodology to yield optimal results for your enterprise.
NetSecurity is a different kind of network penetration testing company. From experience, we know that to be effective, we suggest that network penetration testing exercises be combined with a compromise assessment service, which allows us to evaluate key assets to determine if sophisticated threat actors are conducting covert operations on your network or leveraging your infrastructure.
-
Network
-
Wireless
-
Web/Mobile Applications
-
Cloud
-
IoT
-
ICS/SCADA
-
Social Engineering

Vulnerability Assessments
Account for all your assets and discover security vulnerabilities of each


Do you have an account of your assets and the security vulnerabilities of each? The effectiveness of existing security controls is crucial to the continued success of an organization’s security strategy. NetSecurity will work with you to identify security weaknesses associated with your network, operating systems, servers, and applications. Our consultants will help you identify and mitigate risks and vulnerabilities associated with your wired and wireless networks, mobile devices, cloud platforms, IoTs, web applications, databases, and proprietary applications.
NetSecurity gathers network information and, in some cases, simulates a malicious intruder. Then we run automated scanning tools and use manual testing to discover system vulnerabilities. Our vulnerability assessment service provides a thorough, hands-on security assessment to ensure that the security of your network and system is appropriate to your business and operational needs.
The vulnerability assessment report includes an analysis of findings and a detailed action plan for improving your enterprise’s security posture.
Cyber Risk Assessment
Identifying risks within and with third-parties and supply chain
Supply Chain
Technology
Third-Party
Merger & Acquisition


Compromise Assessment

Who is Hacking Your Network™?
Is your network being held hostage by adversaries and insiders? Unless you dig deep to understand cyber activities on your network, adversarial threats may go undetected. Unearth hidden threats that bypass traditional security products.
Leveraging ThreatResponder® Platform, NetSecurity conducts compromise activities and provides actionable threats in your enterprise within minutes, and determine dwell time of adversaries’ operations.

Regulatory Compliance
Comply with regulatory requirements and avoid fines

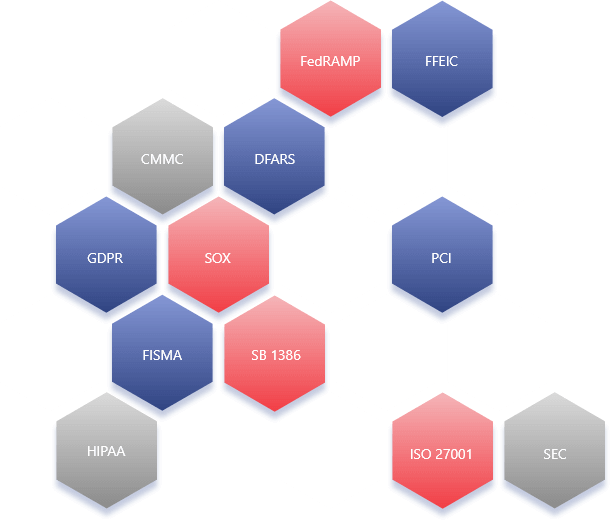
NetSecurity ensures that you avoid fines and meet regulatory compliance. Most importantly we ensure that your enterprise is protected proactively. NetSecurity provides solutions to help you meet your organization’s regulatory requirements including those required by GDPR, DFARS, CMMC, FedRAMP, GLBA, HIPAA, PCI, SOX, SEC, FFEIC, OMB, FISMA, SB 1386, and ISO 27001. We support your team in identifying security gaps, assessing controls, and providing remediation support. For more than a decade, NetSecurity has helped Federal agencies and Fortune 1000 corporations achieve and maintain regulatory compliance.





